back to blog
February 11, 2025
The 10-Year-Old Driver That Killed a 2026 Security Stack
Nir Stolarsky
Table of Contents
A 10-year-old driver did not defeat a modern security stack. Misconfigurations did. This blog explains how attackers used a Bring Your Own Vulnerable Driver technique to disable endpoint protections, and why the real issue was gaps in MFA enforcement, ASR policies, WDAC, HVCI, and lateral movement controls. Through the Nagomi lens, we show how small configuration failures across identity, endpoint, and network layers combine into high blast radius exposure and how continuous validation helps prevent it.

In a recent incident reported by researchers at Huntress, attackers managed to disable dozens of endpoint protection tools using a kernel driver that was first released in 1998.
The attackers didn’t use a sophisticated zero-day, instead using a technique called Bring Your Own Vulnerable Driver (BYOVD), leveraging a decade-old forensic driver from EnCase to mask a vulnerable driver which was later used to gain kernel-level access to terminate security software processes. The industry often treats these as “advanced” threats.
At Nagomi, we see them differently: this was a configuration hygiene failure.
The Anatomy of a Misconfiguration Chain
Breaches like this are rarely about the “EDR-killer” alone. They are the result of a chain of exposures that were likely present in the environment for months.
Link 1: Identity Exposure (The Front Door)
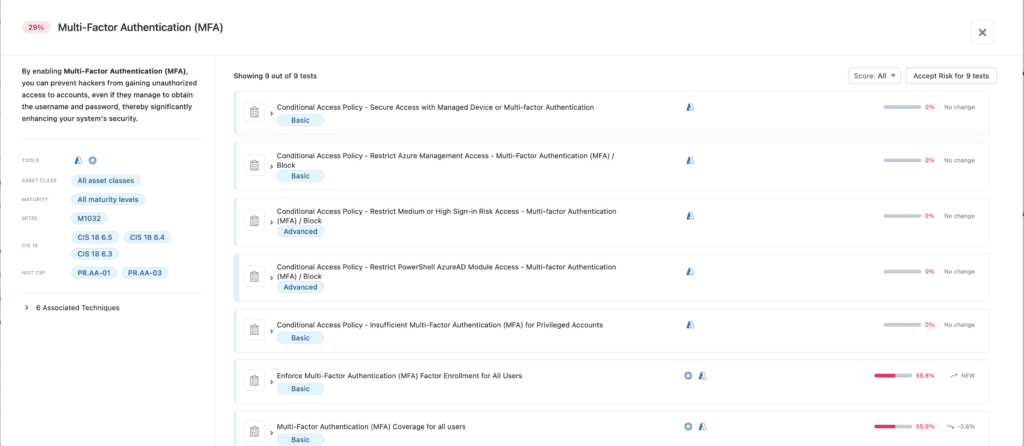
Organizations often believe they are protected because MFA is “available” to their users. However, a tool’s mere existence does not equate to enforcement. In this incident, compromised SonicWall SSLVPN credentials lacking MFA allowed the attacker easy entry into the organization.
The Nagomi Lens:
In this scenario, Nagomi identifies the specific configuration gaps where MFA is “on” in the console but “off” in practice for specific groups of users or protocols:
Microsoft Active Directory’ Conditional Access Policy – Assign MFA Policy For All Users’: We verify that MFA is not just required for some, but is a mandatory global baseline for all accounts (excluding a single break-glass account) to prevent attackers from finding a single “weak link” user.
Microsoft Active Directory ‘Conditional Access Policy – Block Legacy Authentication’: This check specifically looks for the presence of a policy that blocks legacy protocols that do not support MFA.
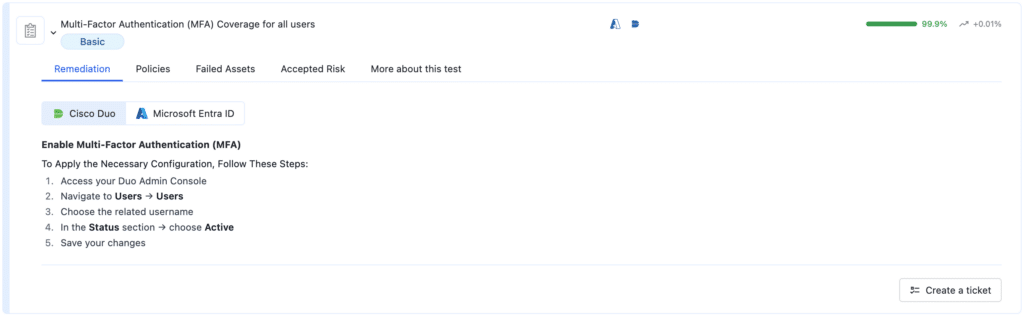
‘Enforce MFA Factor Enrollment’: This test validates that all users have actually enrolled in at least one MFA factor in Okta and Cisco Duo. If a user is “eligible” for MFA but hasn’t enrolled, they are a primary target for an initial compromise.
Link 2: Execution Exposure (Hardening against BYOVD with ASR, WDAC and HVCI)
Once inside, the attacker moved to the endpoint. They used a legitimate, signed kernel driver from 2014. This technique, Bring Your Own Vulnerable Driver (BYOVD) is a way to bypass modern Windows security to gain kernel-level privileges allowing them to disable security software from the “ring 0” level, essentially blinding the EDR before it can even alert.
The Nagomi Lens:
Microsoft has several components that are the “vaccine” for this technique. Firstly, the MS Attack Surface Reduction (ASR) specifically designed to block the download of known-vulnerable signed drivers. In order to install a vulnerable driver, attackers need to use more tools sometimes, creating more opportunities for ASR to intervene and break the attack chain.
However, because this rule can occasionally conflict with older legacy software, organizations frequently leave it set to “Audit” mode. In this breach, “Audit” was simply a front-row seat to the security stack’s destruction.
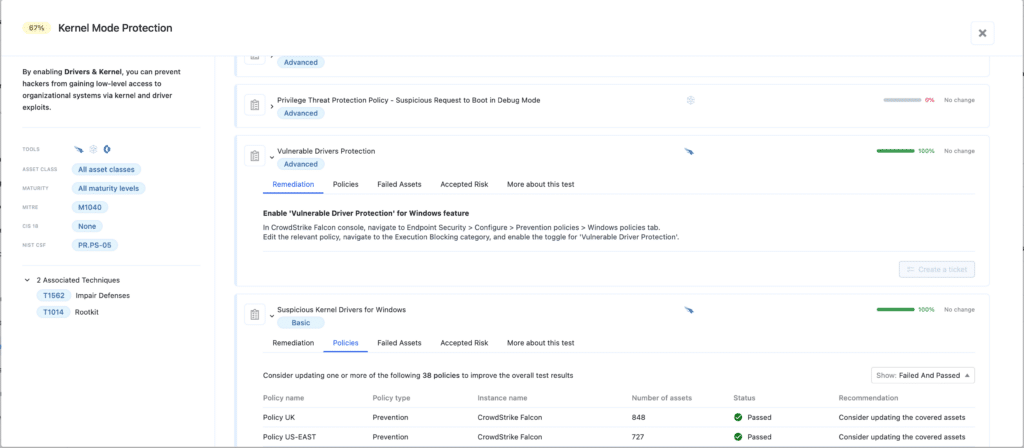
Beyond specific ASR rules, additional hardening components are Windows Defender Application Control (WDAC) (or App Control for Business), and the complementing HVCI (Memory Integrity). While ASR stops the malicious activity from downloading the driver, WDAC stops the driver from being recognized as a valid file if it makes it to the disk, and HVCI stops the driver from exploiting the system memory if it somehow starts running.
Nagomi provides deep visibility into these hardening layers:
We have multiple verification against ASR rules in both Defender and Intune:
- Intune ASR rule ‘Set Endpoint Security Policy for ‘Block executable files from running unless they meet a prevalence, age, or trusted list criterion’ – Windows”.
- ‘ASR – Abuse of Exploited Vulnerable Signed Driver’ for both MS Defender and Microsoft Intune we verify the de facto status of this rule on every machine. If this is set to “Audit” (value 2) or “Disabled” (0) instead of “Block” (1), your modern security stack is vulnerable to a driver from a decade ago.
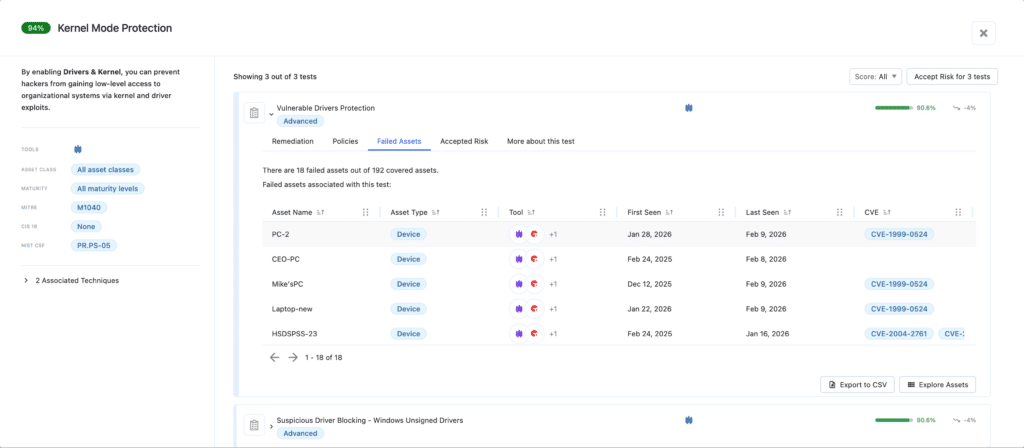
For the WDAC component, Nagomi validates Intune’s rule of ‘Enforce App Control for Business – Windows’. This test verifies if WDAC is in Enforce mode. If active, the 2014 EnCase driver would have been blocked simply because it was “unauthorized” by your corporate policy.For HVCI / Memory Integrity – Nagomi verifies that EDR tools enforce these rules. For Crowdstrike we developed both ‘Vulnerable Driver Protection for Windows’ to Block loading of vulnerable drivers (BYOVD-style) And ‘Suspicious Kernel Drivers for Windows’ to block loading of kernel drivers that CrowdStrike analysts have identified as suspicious. The same goes for SentinelOne and the verification we developed for it.
Link 3: Blast Radius Exposure (Containing the Damage)
Even when an EDR is “killed,” the attacker’s mission is just beginning: they need to move laterally. A “blinded” machine shouldn’t result in a compromised network. If your stack is configured for resilience, you can effectively isolate an attacker on a single island. Without proper hardening, an attacker who gains local access can simply “turn off the lights,” dump memory-resident credentials, and pivot to your most sensitive servers without triggering a single alert.
The Nagomi Lens:
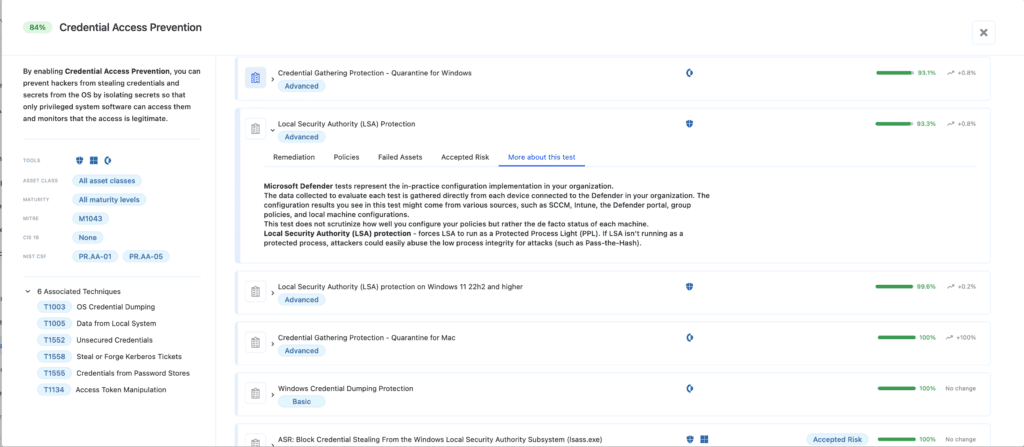
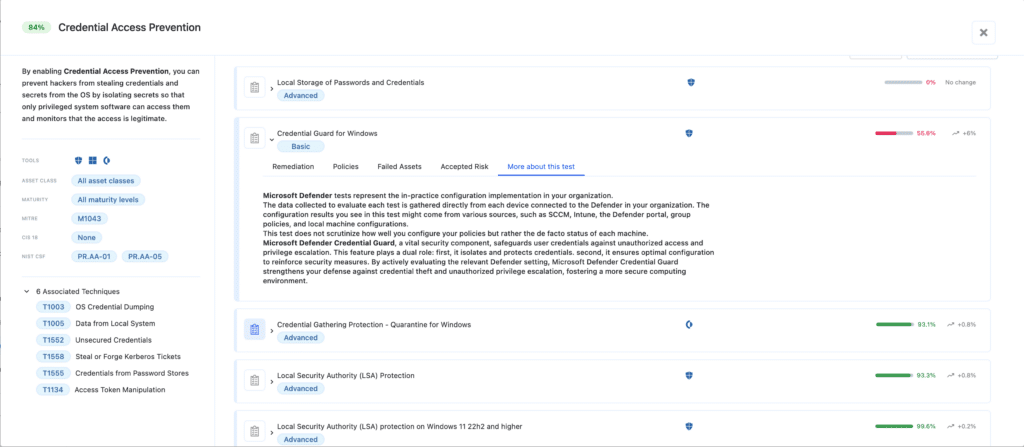
We verify that your defensive “Blast Shield” is locked. This requires enabling Tamper Protection to block user-mode interference, enforcing LSA Protection and Credential Guard to make memory-based credential dumping (like Mimikatz) extremely difficult, and using strict network filtering to kill lateral movement in its tracks.
- Nagomi verifies Tamper protection on CrowdStrike, SentinelOne and MS Defender – preventing users or malware from changing, disabling, or uninstalling it.
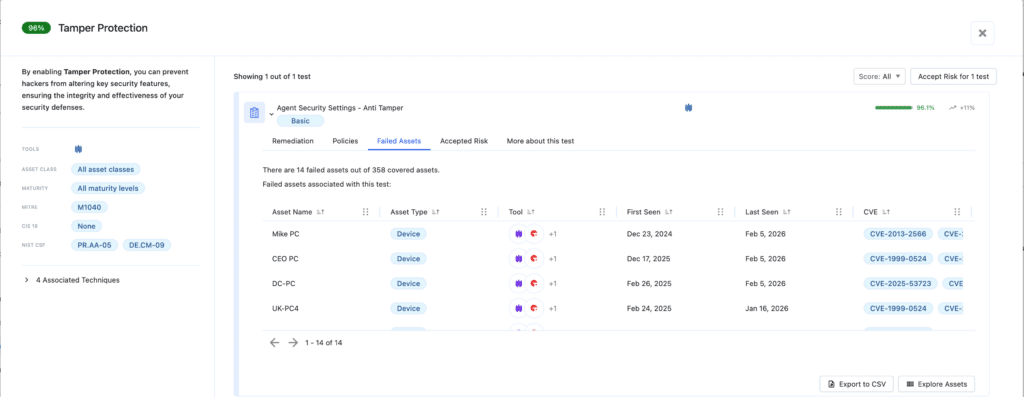
- Nagomi validates that Local Security Authority (LSA) runs as Protected Process Light (PPL) and prevents unauthorized tools from reading the sensitive password hashes stored in memory.
- Credential Guard for Windows: We check for virtualization-based security that isolates secrets in a hardware-protected container, ensuring they remain out of reach even if the OS kernel is compromised.
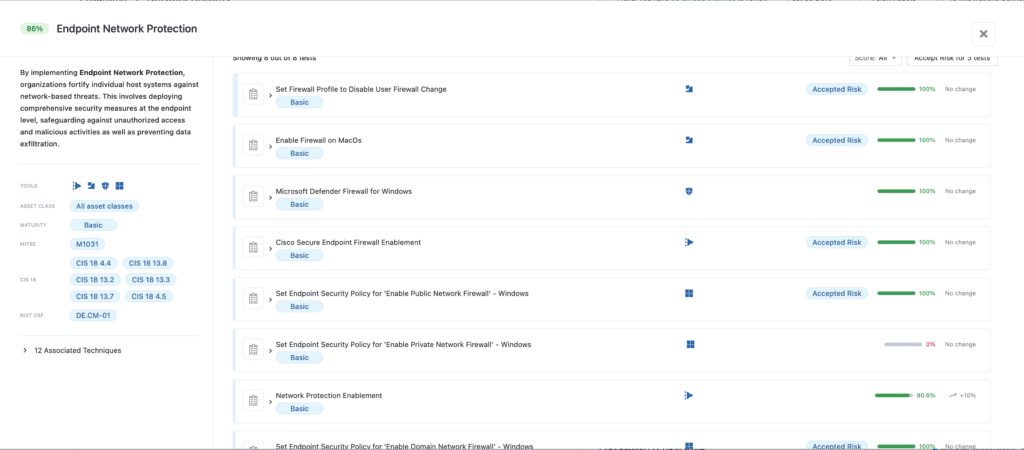
- By auditing the enforcement levels of different network controls, Nagomi ensures your systems are resilient enough to handle a “blinded” EDR. We verify that Windows Defender Firewall is explicitly set to Block all Inbound Traffic for high-risk Public Profiles while simultaneously validating that Microsoft Network Protection is in Block Mode. This multi-layered approach fortifies host systems against unauthorized access and prohibits connections to malicious outbound domains, effectively neutralizing an attacker’s ability to exfiltrate data or move laterally.
It’s Time to Change the Lens
We better stop waiting for the next “Sophisticated APT” headline to audit our stacks. The exposures used in this attack – unprotected VPNs with no MFA, inactive ASR rules, disabled WDAC & HVCI protections, and siloed security layers to contain the damage – all these represent critical weaknesses that lead to an inadequate security posture and, ultimately, a breach.
You don’t need a new tool to stop a BYOVD attack. You need to ensure the tools you already pay for are actually doing their jobs. In Nagomi’s latest Illusion of Maturity research, misconfigurations outweigh vulnerabilities: A small number of high-blast-radius misconfigurations creates more risk than dozens of isolated CVEs, often impacting thousands of assets at once. Don’t wait for the next 10-year-old driver to test your stack. See how Nagomi identifies the exact configuration gaps that turn “enabled” into “enforced”, and closes them before attackers find them. Book a demo today.



