back to blog
BLOG
Scattered Spider Rears Its Ugly Head to Target UK Retailers: How Protected Are You?

You might’ve seen the headlines, big-name UK retailers like Marks and Spencer (M&S), Harrods, and the Co-op group have recently been hit by ransomware attacks. According to reports, the group behind it all is Scattered Spider. If that name doesn’t ring a bell, you might know them by one of their many aliases: Starfraud, UNC3944, Octo Tempest, or Muddled Libra. This crew is well-known in cybersecurity circles for data theft and extortion, often using the BlackCat/ALPHV ransomware to do their dirty work.
The good news is that you don’t have to wait for something to go wrong before checking if your defenses are up to the task. With the Nagomi Proactive Defense Platform, you can get ahead of the game. It helps you assess how ready your organization really is, spot any weak points, and fix them before they become a problem. Now is the time to act, because staying prepared isn’t just about lowering risk. It’s about knowing your defenses are ready for whatever comes next.
Scattered Spider: What You Need to Know
The Scattered Spider group, which targets large companies and their contracted information technology (IT) help desks, is primarily made up of young US and UK nationals who communicate using free social platforms like Discord and Telegram. This group gained notoriety after targeting MGM Resorts in Las Vegas with a ransomware attack and disrupting their operations in September 2023.
Scattered Spider threat actors are considered experts in social engineering attacks and use multiple techniques, especially phishing, push bombing, and subscriber identity module (SIM) swap attacks, to obtain credentials, install remote access tools, and/or bypass multi-factor authentication (MFA).
How did the recent attacks on M&S, Harrods, and Co-op unfold?
Based on the information currently available, here is a step-by-step look at how threat actors executed these targeted ransomware campaigns:
- Recon via social engineering: Attackers used social engineering to gather intel on IT helpdesk staff, learning who to impersonate and how.
- Impersonation: Armed with that knowledge, they posed as IT personnel and contacted other employees through phone calls and SMS.
- Credential harvesting: They convinced employees to hand over network credentials under the guise of IT support.
- Remote access and control: Employees were then instructed to install remote access tools, disable MFA, and reset passwords, which gave the attackers full access.
- Lateral movement and deployment: With access secured, the attackers moved laterally across systems and deployed ransomware.
- Ransomware details: The campaign likely used DragonForce ransomware, a ransomware-as-a-service (RaaS) tool. This model allows cybercriminals to rent the ransomware infrastructure in exchange for a share of any ransom payments.
DragonForce comes with a wide range of damaging capabilities. It can harvest credentials, escalate privileges, disable antivirus programs, encrypt critical files, and cover its tracks by deleting system logs, making it a dangerous weapon in the wrong hands.
In short, this was a well-coordinated attack that combined psychological manipulation, technical execution, and off-the-shelf ransomware tools. It highlights the importance of robust employee training, layered defenses, and real-time monitoring.
Nagomi’s Coverage for the Scattered Spider Group
Step 1: Log into your Nagomi Platform and click “Campaigns” from the left menu. Search for “Scattered Spider” in the search menu to locate the Medusa Ransomware Campaign. Then, click “Explore More”.
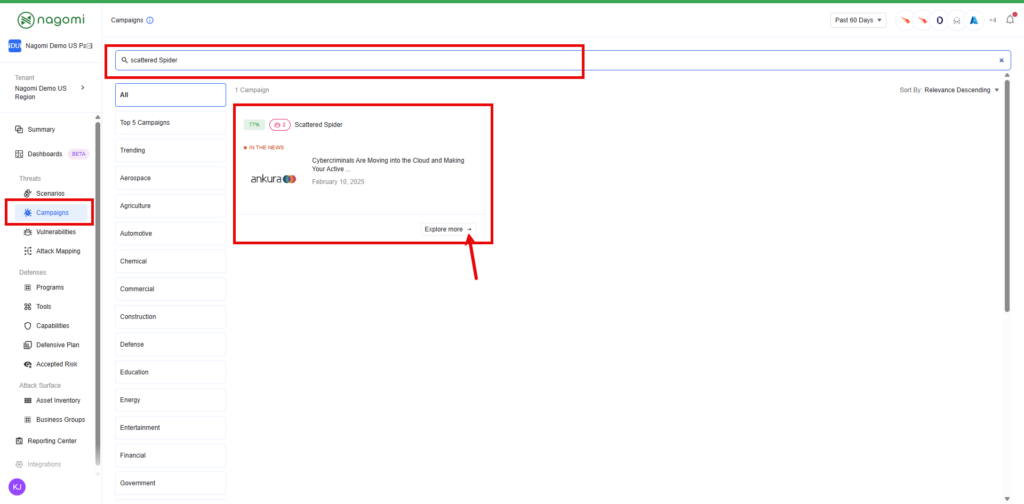
Step 2 – This campaign overview page provides teams with a high-level overview of your organization’s preparedness against the Scattered Spider threat. This page includes the following information:
- Top Susceptible Techniques: Highlights the techniques your organization is most susceptible to based on analyzing the attack campaign, utilization of your deployed security tools, and your overall attack surface.
- MITRE ATT&CK Mapping: Highlights how prepared your organization is against the various MITRE tactics being used in the chosen threat campaign.
- Known Exploitable Vulnerabilities: Highlights if any CISA KEV’s are being leveraged as part of the attack campaign.
- Defensive Plans: Recommended remediation steps that can be taken to improve organizational security posture against Medusa ransomware based on the gaps identified by the Nagomi platform.
- All Defensive Capabilities: Highlights all your existing deployed defensive controls with their identified coverage gaps and how they would potentially impact your security posture.
- Missing Capabilities: Highlights those defensive capabilities (security controls) that your organization is currently missing and needs to add to ensure comprehensive protection against the Medusa ransomware threat.
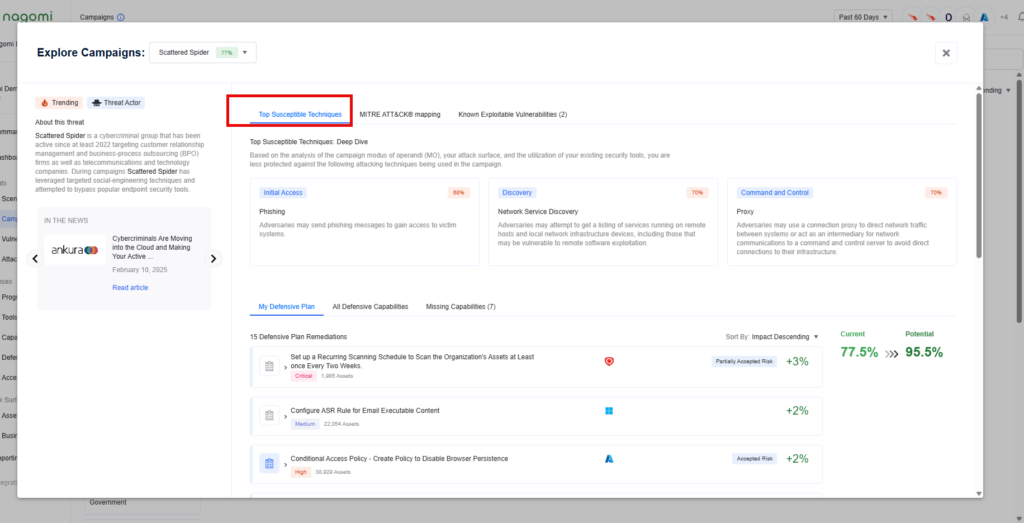
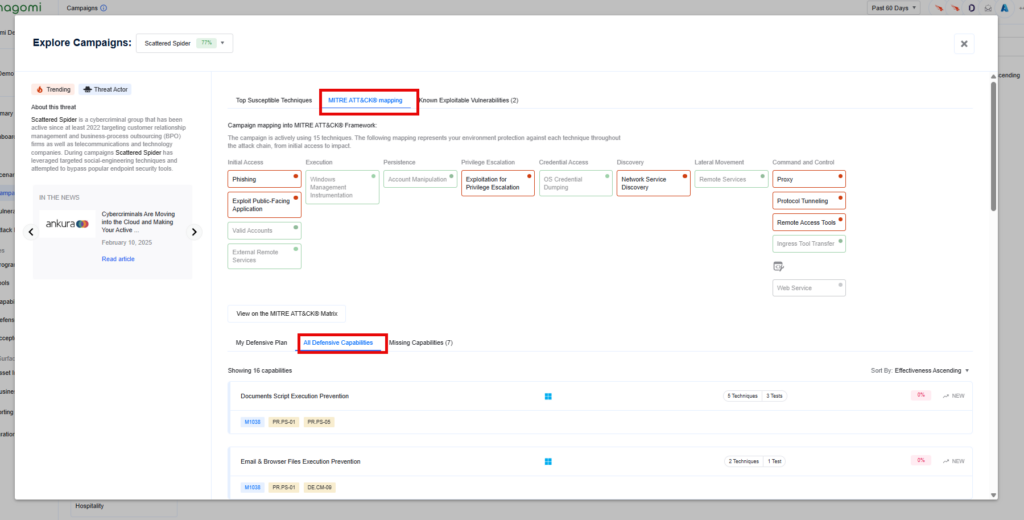
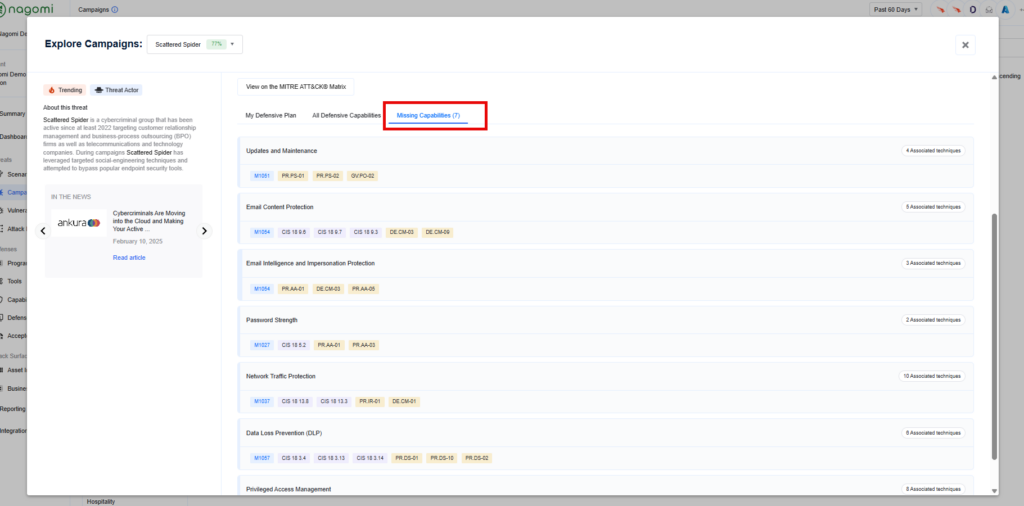
Step 3: Leverage the top 15 remediation recommendations provided by Nagomi to quickly begin the process of fixing identified security gaps.
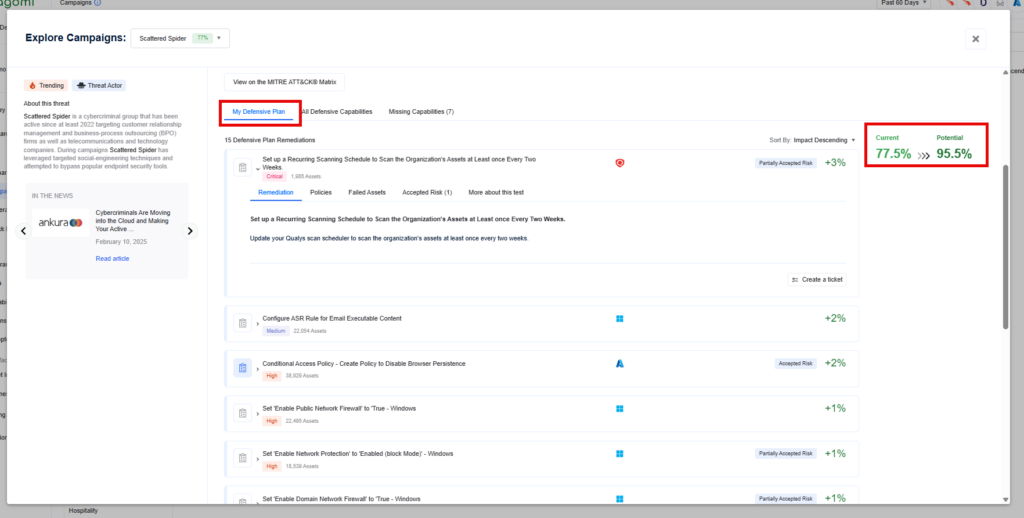
Nagomi’s remediation recommendations are intended to provide incident responders with results-driven steps that can be taken to reduce their mean-time-to-remediate (MTTR).
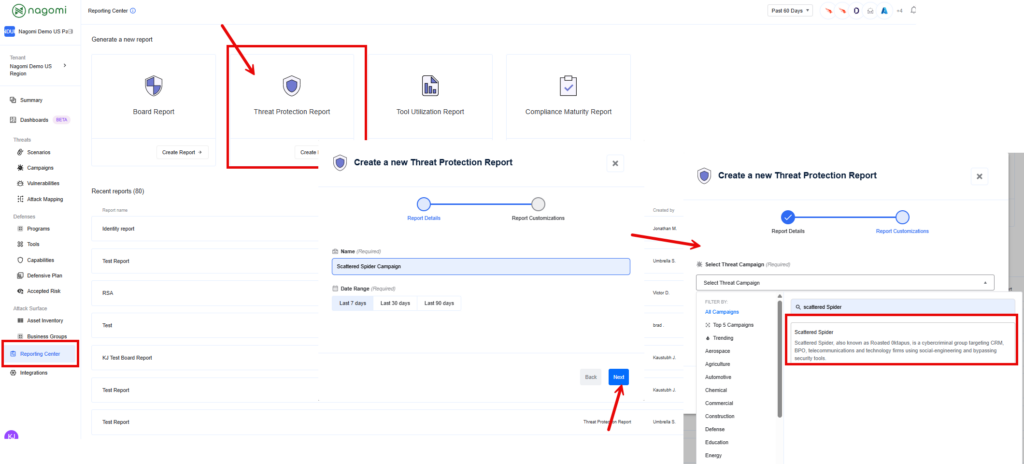
While identifying and closing gaps is a crucial aspect, it’s equally important to effectively communicate organizational preparedness to non-technical stakeholders, such as the Board of Directors. The Nagomi platform simplifies this process by providing SecOps teams with customizable reports and dashboards that can be quickly generated to report program health. In this case, to specifically report organizational readiness against the Scattered Spider campaign, simply click on the “Reporting Center” item from the left-hand menu and select the “Threat Protection Report.”
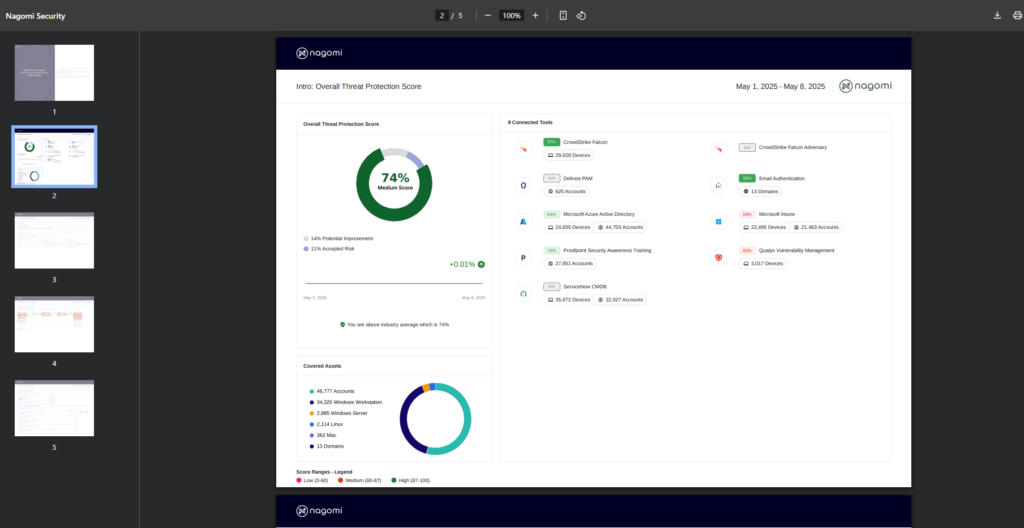
The final report is generated in an easy-to-understand visual PDF format that can be used to communicate organizational preparedness. The report below is the same report that teams can leverage to highlight their organization’s readiness against the Medusa ransomware to all of their stakeholders (both technical and non-technical).
Conclusion
Here’s the bottom line. Groups like Scattered Spider aren’t slowing down, and neither should your security strategy. Today’s threats move fast, and waiting until something breaks is no longer an option. Staying secure means staying a step ahead—spotting gaps before attackers do and making sure your defenses are always ready.
That’s where the Nagomi Platform comes in. It helps you see what matters, take action where it counts, and keep improving every step of the way. Because the strongest security programs don’t just react. They adapt, evolve, and prepare for whatever comes next.


