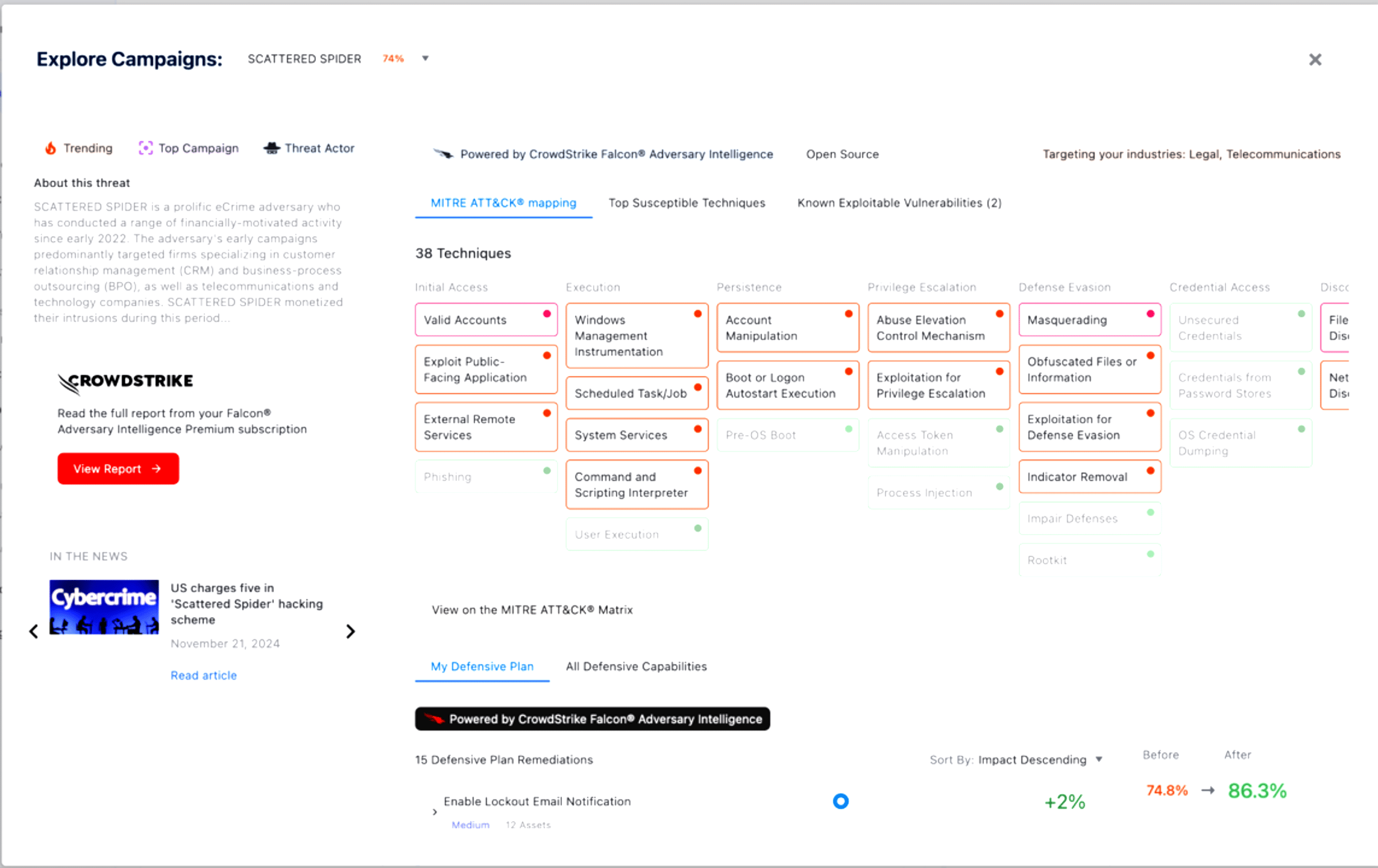
Assess defenses against active threats
Understand your protection level against current threats and campaigns like ransomware or Scattered Spider
Map controls to MITRE ATT&CK to expose defensive gaps
Pinpoint key vulnerabilities exploited by attackers and prioritize remediation based on control effectiveness
Identify compensating controls to close high-impact exposure
Turn intel into action
Automatically map threat intel and TTPs to your defensive controls
Generate prescriptive, tool-specific remediation steps (e.g., CrowdStrike, Defender, Okta)
Continuously track readiness as new threats emerge
Enable continuous threat exposure management
Identify “toxic combinations” of exposures converging on critical assets
Correlate external threat activity with your business context to better understand true risk
Enhance breach and attack simulation by focusing tests on validated gaps
Continuously adapt to emerging threats, dynamically updating exposure insights as new vulnerabilities, attack techniques, or business changes arise.
Nagomi security: your questions, answered
Discover how Nagomi unifies exposures, strengthens controls, and helps teams reduce risk with context, automation, and scale.
What does it mean to “operationalize” threat intelligence with Nagomi?
Nagomi’s correlation engine integrates threat intel with your tools, assets, and business environment to identify the most critical TTPs and exploitable vulnerabilities. It then delivers prioritized defensive guidance to turn insight into action.