About This Series
Welcome to Part 1 of a three-part series exploring what it really takes to make Continuous Threat Exposure Management (CTEM) work not in theory, but in practice.
- Part 1 (this post): Why CTEM needs Automated Security Control Assessment (ASCA) to be effective
- Part 2: Why tracking outcomes, not activity, is the key to performance and board reporting
- Part 3: How to continuously validate controls at scale without overloading your team
Let’s get into it….
CTEM: A Helpful Framework, But Not the Goal
Cybersecurity loves a good framework, and CTEM is one that actually delivers. It moves us away from reactive, point-in-time scans to a structured, ongoing approach to managing real risk. No more “whack-a-mole” CVE chasing.
Gartner predicts that organizations adopting CTEM will reduce breaches by two-thirds by 2026. That’s a bold claim, and a compelling reason to take notice.
But CTEM isn’t the endgame. It’s the process. The structure. The how.
The real goal? Reducing the risk of a breach. Using your tools the right way. Knowing your defenses are actually working.
And that’s where most programs fall short: they don’t validate if protections are functioning as intended.
The 5 Stages of CTEM and Where It Breaks
CTEM is built around five stages:
- Scoping: What’s in the exposure program? (workstations, servers, cloud, business units, etc.)
- Discovery: What assets, vulnerabilities, misconfigurations, and threats exist?
- Prioritization: Which risks matter most based on business context?
- Validation: Are deployed controls actually preventing or detecting those threats?
- Mobilization: What actions should we take and where?
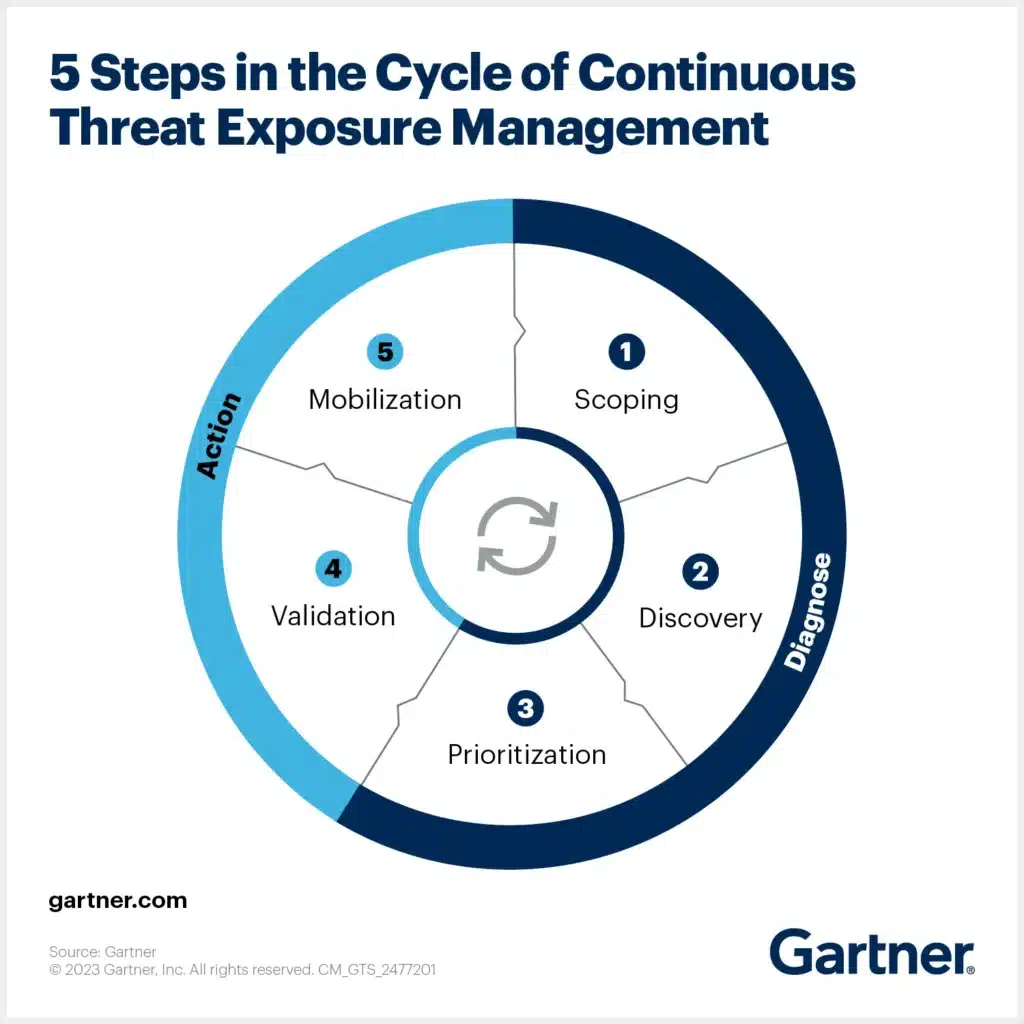
Most organizations stall after stage (3) three. Why? They lack a way to validate whether their controls are doing what they’re supposed to. It’s one thing to identify a critical vulnerability. It’s another to know if it’s been mitigated or if the control is misconfigured, missing, or simply broken.
Enter Automated Security Controls Assessment (ASCA): The Control Checkup You’ve Been Missing
Automated Security Controls Assessment (ASCA) is the missing link in most CTEM programs. It closes the gap between potential exposure and real protection by continuously verifying that your controls are in place, functioning as intended, and mapped to live threats.
In this context, exposure means far more than just software vulnerabilities, it also covers control gaps, misconfigurations, policy drift, and misalignment with adversary TTPs. While organizations often tackle these issues in isolation, ASCA unites them under one lens, giving you a holistic view of your security posture that reflects how attackers actually operate.
As Gartner explains: “ASCA improves the security posture by verifying the proper, consistent configuration of security controls, rather than simply verifying the existence of controls.” — Hype Cycle for Security Operations, 2024
Why CTEM Needs ASCA And What Happens Without It
Here’s the tough reality: many teams assume they’re protected, but in practice, they’re only patched.
They’ve deployed the tools but haven’t confirmed if they’re enforced, properly configured, or aligned to real risks. That’s why misconfigurations are now a leading cause of breaches.
A few real-world questions every team should be asking and answering with data:
- You have MFA, but is it enforced across all user accounts?
- You’ve deployed EDR, but are anti-tampering and lateral movement protections actually active?
- You rolled out email security, but are phishing filters consistent across regions?
If your organization includes multiple subunits with different security stacks, how do you answer any of the questions above with confidence?
Without ASCA, CTEM can give you a false sense of security. With it, you spot the blind spots before attackers do.
CTEM Is Only as Good as the Controls Behind It
CTEM gives you the structure. ASCA ensures it works.
By continuously validating and optimizing controls, ASCA turns CTEM from a theoretical framework into a real, risk-reducing program. That’s the difference between checking boxes and actually protecting your business.
In Part 2, we’ll look at how ASCA unlocks meaningful performance measurement — so you’re not just tracking activity, you’re proving impact.
Stay tuned.
Want to Know More in the Meantime?
Schedule a demo and learn how Nagomi can help your organization navigate today’s complex financial threat landscape with greater clarity, efficiency, and confidence.