back to blog
BLOG
Operationalizing Threat Intelligence: A CISO’s Guide to Turning Threat Noise into Action

Table of Contents

What is Cyber Threat Intelligence?
Cyber threat intelligence (CTI) refers to the process of collecting, analyzing, and using data to understand and respond to cyber threats. The primary goal of CTI is to provide organizations with actionable insights into potential or ongoing cyber-attacks, enabling them to make informed decisions about defending their networks. As CrowdStrike explains, threat intelligence helps security teams understand the tactics, motives, and behaviors of threat actors, allowing them to stay ahead of potential attacks.
What Cyber Threat Intelligence Isn’t
While CTI is often seen as a collection of raw data about cyber threats (such as malware signatures or IP addresses), it is not just about raw information. True CTI involves turning this data into actionable insights, which can be used to improve an organization’s security posture. It’s important to note that not all threat feeds are useful for every organization. Without proper analysis and context, raw data can lead to an overwhelming number of alerts, many of which may not be relevant.
The Evolution of Cyber Threat Intelligence
CTI has evolved significantly over the past decade. Initially, many organizations relied on generic threat feeds that provided little context or relevance. Today, modern CTI goes beyond basic indicators of compromise (IOCs) to include deeper insights such as attacker motives, techniques, and long-term strategies. As threat actors have grown more sophisticated, so too have the methods used to track and counter them, including the use of machine learning, automation, and human analysis.
Types of Cyber Threat Intelligence
Cyber threat intelligence is generally categorized into three types: tactical, operational, and strategic, each serving different purposes within an organization:
- Tactical Threat Intelligence focuses on short-term threats and typically includes specific technical indicators like malicious IP addresses or file hashes. It is machine-readable and often automatically ingested into security tools like firewalls. However, this type of intelligence has a short lifespan, as threat actors frequently change their tactics.
- Operational Threat Intelligence provides insights into the “who, why, and how” behind cyber-attacks. It requires human analysis to track adversaries and understand their tactics, techniques, and procedures (TTPs). This type of intelligence is valuable for security operations centers (SOCs) and incident response teams to prioritize their efforts and anticipate future actions by threat actors.
- Strategic Threat Intelligence offers high-level insights into how broader trends, such as geopolitical events, impact an organization’s cyber risk. This type of intelligence helps executives make informed decisions about long-term security investments and strategies. Unlike tactical or operational intelligence, strategic intelligence requires a deep understanding of global trends and adversary motivations.
By understanding and leveraging these types of intelligence, organizations can better protect themselves from a range of cyber threats, from opportunistic malware to nation-state actors.
This comprehensive approach transforms CTI from a reactive measure into a proactive strategy for cybersecurity resilience.
Challenges in Operationalizing Threat Intelligence
While cyber threat intelligence (CTI) offers immense value in improving security postures, operationalizing it presents several key challenges that organizations must navigate:
Data Overload and Noise
One of the most significant challenges in CTI is dealing with the vast amount of data generated by threat feeds. These feeds can produce millions of indicators daily, which often overwhelm security teams. As a result, identifying actionable intelligence becomes difficult, with security teams spending valuable time filtering out irrelevant data and false positives. This problem can delay threat detection and response times. To address this, organizations must prioritize threats based on relevance to their specific risk profile, tailoring threat intelligence to their unique environments to reduce noise and improve decision-making.

Context and Prioritization
CTI data can be challenging to prioritize without proper context. Many feeds provide raw data, such as IP addresses or file hashes, without sufficient information on how these indicators relate to the organization’s specific threat landscape. This lack of context makes it hard to differentiate between immediate risks and less relevant threats. A solution lies in aligning CTI with the organization’s industry, infrastructure, and assets to ensure that threat intelligence is actionable and prioritized effectively.
Lack of Resources
Maintaining multiple CTI feeds and analyzing them effectively requires substantial resources, including skilled personnel and robust infrastructure. Many organizations struggle to operationalize CTI due to a lack of sufficient resources, such as personnel who are capable of interpreting complex threat data. Investing in automation tools and third-party services can help alleviate some of this burden by reducing the need for manual analysis while ensuring timely responses.
Integration with Existing Tools
Merging multiple threat intelligence feeds into an existing security infrastructure can be complex. Organizations often struggle with integrating CTI data into tools like Security Information and Event Management (SIEM) systems, vulnerability management platforms, and other security solutions. Poor integration leads to fragmented threat visibility, making it harder for teams to respond quickly and efficiently. Investing in platforms that support seamless integration and interoperability across security tools is critical to operationalizing CTI.
Understanding Security Tool Configuration
Another challenge lies in configuring security tools to properly ingest and act on CTI feeds. Without proper configuration, security tools may fail to detect relevant threats, leading to gaps in protection. Ensuring that tools are correctly set up to leverage CTI data is essential for efficient threat detection and response.
Separating Noise from Signal
A significant issue in operationalizing CTI is distinguishing real threats from a sea of irrelevant data. Many threat feeds are generic, listing all known threats without context or relevance to specific organizations. Filtering out irrelevant data and focusing on threats that are actively targeting the organization can help reduce unnecessary alerts and improve response times.
Expertise Gap
Many organizations lack the in-house expertise to manage and analyze threat intelligence data effectively. According to industry surveys, a large portion of security professionals cite a lack of skills and resources to manage comprehensive CTI programs. Addressing this gap requires investment in training programs for security teams or leveraging third-party CTI providers.
By addressing these challenges—through better integration, prioritization, resource allocation, and expertise development—organizations can better operationalize their cyber threat intelligence to strengthen their security postures.
Steps to Operationalize Threat Intelligence
Operationalizing threat intelligence (CTI) involves aligning security data, tools, and processes to turn raw threat intelligence into actionable insights that can proactively enhance an organization’s security posture. The process typically requires a combination of understanding the organization’s security environment, closing gaps, and configuring tools to work seamlessly with CTI feeds. Security teams can maximize their existing security stack by using solutions like Nagomi to streamline these operations.

Step 1: Creating a Custom Threat Profile
Before integrating threat intelligence, it’s crucial for security teams to understand their existing security infrastructure. A custom threat profile is a tailored assessment that identifies potential risks, vulnerabilities, and the specific threat actors targeting your business.
- Gather Key Information: Start by collecting data about your organization’s assets, including sensitive information, critical infrastructure, and key personnel. Consider the following:
- Data Sensitivity: Identify what data is most valuable and where it’s stored.
- Infrastructure: Map out your IT environment, including hardware, software, and network components.
- Business Operations: Understand your operational processes and how they might be disrupted.
- Incident Reports: Analyze any previous breaches or attacks.
- Industry Trends: Stay updated on common threats facing similar organizations through threat intelligence reports.
- Assess Vulnerabilities: Conduct a thorough vulnerability assessment to identify weaknesses within your systems.
- Identify Potential Threat Actors: Different organizations face different threats depending on their industry, size, and location.
- Nagomi’s Role: Nagomi’s platform creates custom threat profiles through a comprehensive approach that includes in-depth assessments of current security postures, gathering threat intelligence relevant to the industry, prioritizing risks based on likelihood and impact, and developing tailored mitigation strategies. Emphasizing continuous monitoring and updates, Nagomi ensures organizations remain resilient against evolving threats, empowering them to proactively defend their assets.
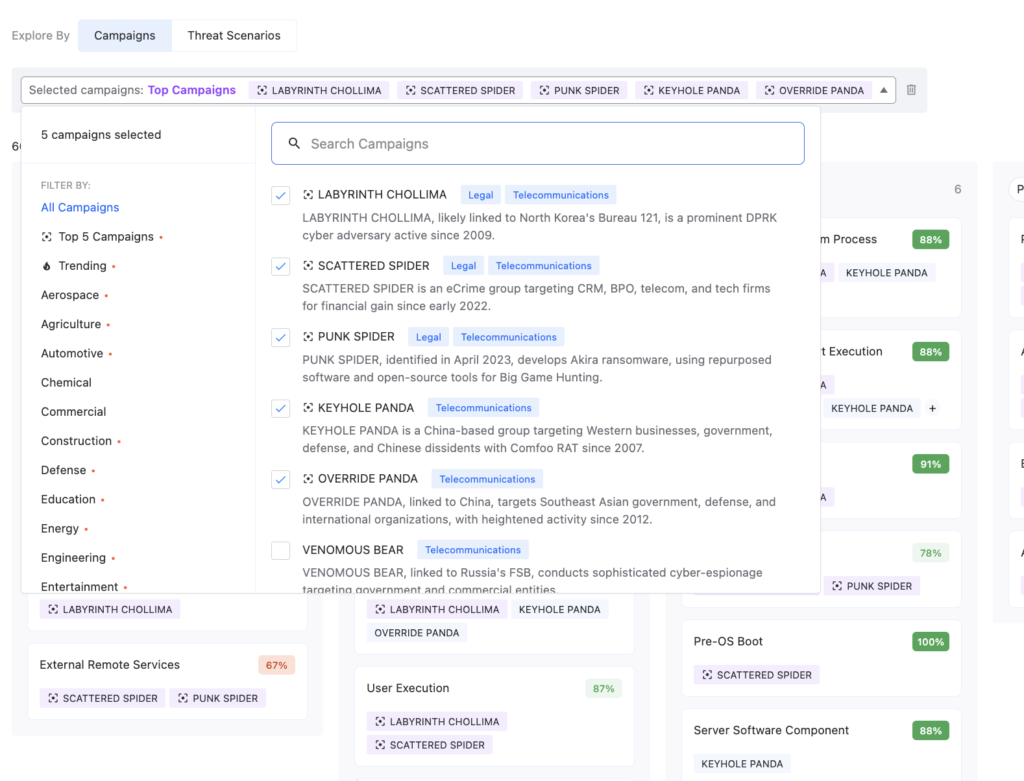
Step 2: Identifying Gaps in Coverage
After reviewing your security infrastructure, the next step is to identify gaps or weaknesses where tools may not provide full protection. These gaps could be caused by misconfigurations, outdated software, or missing security controls.
- Example Gaps: For instance, if your security tools are not configured to detect the latest malware families or if they lack the ability to parse certain types of threat feeds, these gaps must be addressed. Similarly, if a tool fails to cover certain segments of your environment, such as cloud infrastructure or OT/IoT devices, you’ll need to supplement this with additional solutions.
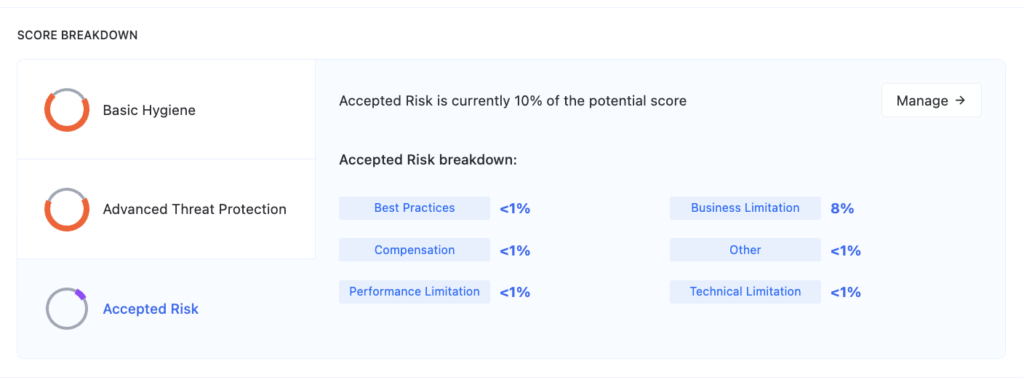
- Nagomi’s Role: Nagomi helps close these gaps by providing visibility into tool performance, identifying misconfigurations, and recommending enhancements. The platform’s ability to validate security controls ensures that all tools are configured optimally to leverage incoming CTI.
Step 3: Understanding Exceptions
Not all environments can implement standard security measures, and these exceptions must be considered when operationalizing threat intelligence. For example, in a factory setting, it may be impossible to enforce multi-factor authentication (MFA) due to the lack of personal devices, or legacy systems may not support modern threat detection capabilities.
- Handling Exceptions: In these cases, security teams must develop alternative processes for monitoring and protecting vulnerable systems that can’t adhere to typical security configurations. This may involve segmenting networks or using compensating controls.
- Nagomi’s Role: Nagomi provides flexibility for handling such exceptions. The platform can help create alternative workflows and compensating controls that ensure critical systems are protected, even when standard security practices can’t be applied.
Step 4: Separating Noise from Signal
Given the overwhelming volume of data generated by CTI feeds, it is critical to filter out irrelevant or low-priority alerts to focus on the threats that pose the greatest risk. This involves setting thresholds for what constitutes actionable intelligence based on the organization’s specific threat profile.
- Tailoring Threat Intelligence: Prioritizing based on relevance to your organization’s assets and threat landscape can greatly reduce false positives and focus attention on real threats.
- Nagomi’s Role: Nagomi enables teams to customize CTI feeds to their environment, helping them focus on the most relevant threats and reduce noise. By continuously refining threat feeds, security teams can more effectively separate noise from actionable intelligence.
Step 5: Automating and Streamlining Workflows
Once threat intelligence has been integrated into the existing infrastructure and tools, the next step is to streamline and automate processes wherever possible. Automating low-level tasks, such as blocking known malicious IPs or updating firewall rules based on CTI data, allows security analysts to focus on more strategic issues.
- Automation Potential: Many routine tasks, such as alert correlation or vulnerability management, can be automated to increase response speed and reduce human error.
- Nagomi’s Role: Nagomi’s platform provides automation capabilities that streamline workflows, such as automating the ingestion of CTI feeds and correlating alerts with relevant intelligence. This helps ensure that critical threats are addressed immediately while reducing the operational burden on security teams.
Step 6: Continual Improvement and Adaptation
Threat intelligence is not a one-time task but a continuous process. As the threat landscape evolves, so must your security operations. It’s essential to continuously monitor for new threats, assess the effectiveness of current security tools, and integrate emerging intelligence into your workflows.
- Ongoing Assessment: Regularly evaluating the performance of security tools and CTI feeds ensures that your defenses remain aligned with the current threat environment.
- Nagomi’s Role: Nagomi’s continuous security validation tools ensure that your defenses are always up-to-date and that new intelligence is integrated seamlessly into your security stack. By conducting regular assessments, Nagomi helps identify areas of improvement and ensures that the security posture evolves alongside emerging threats .
By following these steps and leveraging tools like Nagomi, organizations can operationalize threat intelligence effectively, maximizing the impact of their existing security infrastructure while staying ahead of emerging threats.
What Should Be Done with Threat Intelligence?
Operationalizing threat intelligence is not just about ingesting data; it also requires careful decisions about what tasks to handle manually, what to automate, and who is responsible for managing specific aspects of threat intelligence.
Manual Work vs. Automation
Some aspects of threat intelligence demand human analysis, while others can be proactively automated. For instance:
- Manual Tasks: Contextual analysis of a threat, such as determining its impact on the organization, often requires human expertise. Security teams need to manually correlate intelligence with ongoing investigations or specific incidents within the organization.
- Automated Tasks: Automating tasks such as blocking known bad IP addresses, updating firewall rules, or correlating alerts with relevant threat intelligence can drastically reduce the time to respond to threats. Automation helps prevent human error and frees up resources for more strategic efforts.
Who is Responsible for What?
Effective threat intelligence involves various stakeholders, from security operations center (SOC) analysts to incident responders and threat hunters. Key roles include:
- SOC Analysts: Responsible for monitoring and responding to real-time alerts.
- Incident Responders: Handle investigations and remediation based on threat intelligence.
- Threat Hunters: Proactively search for emerging threats based on intelligence reports.
Clearly defining responsibilities ensures that threat intelligence is acted upon in a timely and effective manner.
What Does Success Look Like?
A successful threat intelligence program results in:
- Reduced mean time to prevent.
- Fewer false positives, thanks to better data prioritization.
- Improved visibility into real threats targeting the organization.
Metrics such as these help security teams assess their effectiveness and continually refine their processes.

How to Continually Assess New Threats
The cyber threat landscape is constantly evolving, and to stay ahead, organizations must proactively and continuously assess new threats and incorporate them into their processes.
Ongoing Monitoring
- Regular Updates: Security teams should monitor new threats in real time and continuously update their security tools with the latest intelligence. This could include regular updates to malware signatures, indicators of compromise (IOCs), and TTPs (Tactics, Techniques, and Procedures) used by threat actors.
- Nagomi’s Role: Nagomi’s real-time integration capabilities ensure that security tools are always updated with the latest intelligence, helping to minimize the organization’s exposure to new threats.
Adaptive Security Posture
As the threat landscape changes, so should an organization’s security posture. Threat intelligence should drive improvements in security tools, configurations, and workflows.
- Nagomi’s Role: By leveraging continuous validation of security tools, Nagomi helps ensure that your security defenses are always aligned with the latest threat intelligence.
Summary
Operationalizing threat intelligence is crucial for enhancing an organization’s ability to defend against evolving cyber threats. This proactive process requires a clear understanding of the security infrastructure, addressing gaps, integrating threat feeds, and automating processes where appropriate. Platforms like Nagomi play a critical role by helping organizations make the most of their existing security stack. By focusing on key areas such as integration, automation, and continuous improvement, organizations can transform raw threat data into actionable insights, reducing response times and enhancing their overall security posture.
Nagomi’s Threats in the News Feature
Nagomi’s new “Threats in the News” feature is transforming the way cybersecurity teams manage and respond to emerging threats. It filters through a vast array of cybersecurity news to identify the most relevant threats for your organization. By creating a tailored threat profile for each individual customer, Nagomi highlights only the most pertinent campaigns and threat actors, delivering relevant news information and mapping it directly to defensive controls.
Beyond individual threat assessment, “Threats in the News” contributes to a comprehensive threat intelligence strategy. It helps security leaders craft compelling risk narratives for executives while equipping their teams with contextual insights needed for effective action. Additionally, it tracks attack trends, highlights gaps in MITRE ATT&CK coverage, and delivers targeted defensive plans for each threat actor or campaign, empowering security teams to respond efficiently.
Interested in learning more? Request a demo today and test drive the feature first-hand.
See Nagomi’s “Threats in the News” Feature
Current Nagomi customers can experience the power of personalized threat intelligence today with Nagomi’s “Threats in the News” feature. Not a customer yet? Get a demo today to learn more about how this new capability can enhance your organization’s security strategy.



