Establish a trusted inventory
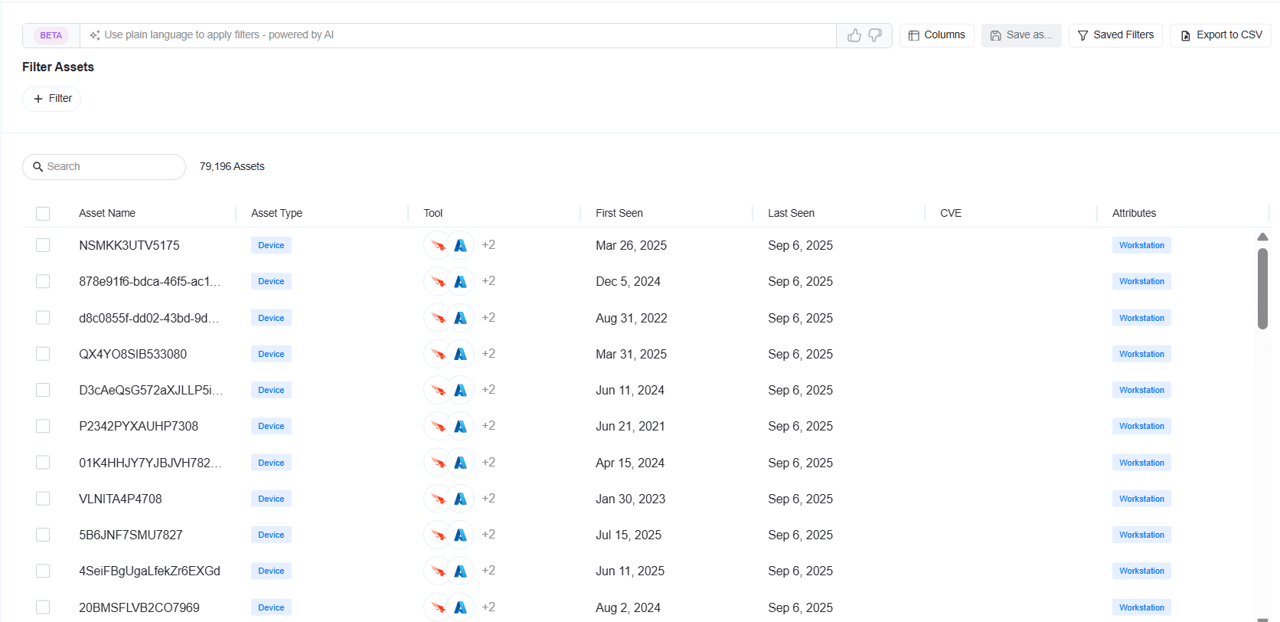
Replace manual spreadsheets and static inventories with a live, correlated asset and control inventory
Identify gaps, unprotected endpoints, and misaligned configurations across business units
Eliminate duplication and conflicting data by reconciling input from CMDBs, EDR, IAM, and scanners
Accelerate triage and reduce time-to-remediation
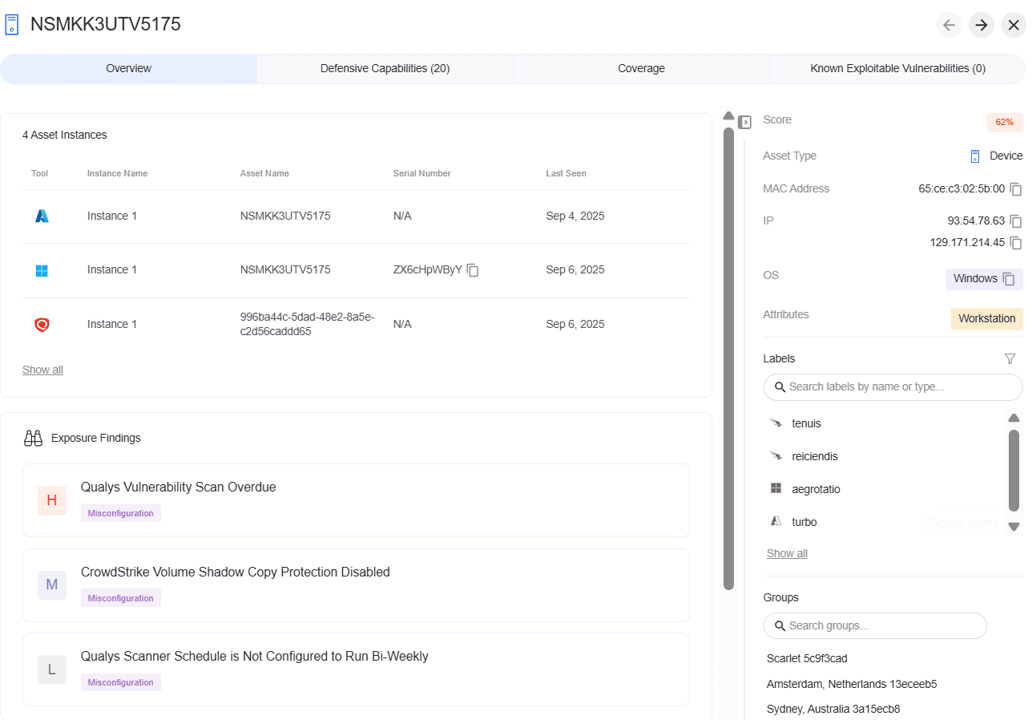
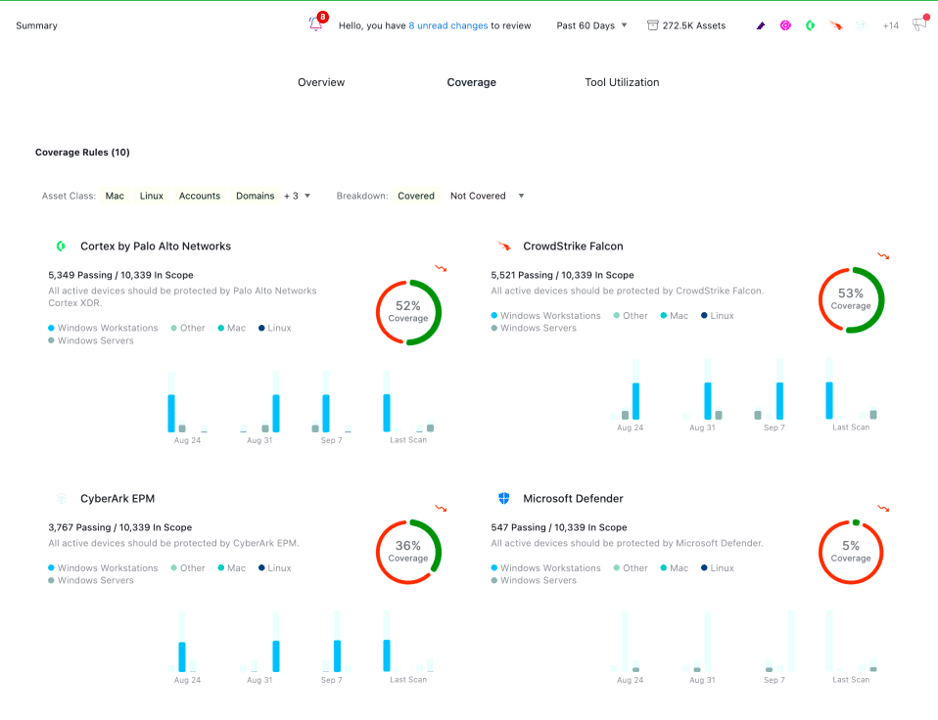
Correlate controls, vulnerabilities, and threats into a unified asset view
Find your riskiest assets with live, correlated context, no queries or pivoting across tools
Highlight coverage gaps and view unprotected, misconfigured, or out-of-policy assets
Leverage dynamic business groupings
Automatically group assets by business units, subsidiaries, locations, user roles, or criticality
Compare exposure and protection across different operational areas to guide smart investments
Break silos between IT, Security, and Ops by providing a shared, view of risk
Nagomi security: your questions, answered
Discover how Nagomi unifies exposures, strengthens controls, and helps teams reduce risk with context, automation, and scale.
Does Nagomi require agents or new tooling to deliver visibility?
No. Nagomi uses read-only API connections to seamlessly integrate with the tools you already have.