Medusa ransomware’s return highlights a sobering truth: cyber threats are becoming more adaptive and relentless. Targeting industries from healthcare to manufacturing, this ransomware variant has already compromised over 300 organizations, with its reach expanding well into 2025. Detailed information about this threat and the associated IOCs and TTPs can be seen in the CISA Advisory- #StopRansomware: Medusa Ransomware.
The good news? You don’t need to wait until it’s too late to check if your defenses are sufficient. By leveraging the Nagomi Proactive Defense Platform, you can take charge of your security posture today. Assess your organization’s readiness, pinpoint vulnerabilities, and close gaps before they can be exploited. The time to act is now, because being prepared is more than just reducing risk; it’s about ensuring your defenses are ready for whatever the next threat brings.
Medusa Ransomware: What you Need to Know
Medusa ransomware, a ransomware-as-a-service (RaaS) campaign that launched in 2021, has evolved into one of the most formidable threats in cybersecurity. Using a double-extortion model, it not only encrypts your data but also steals it, threatening to expose sensitive information if the ransom isn’t paid. Its sophistication and relentless nature have made it a top concern for organizations worldwide.
What sets Medusa apart is its multi-stage, complex approach. From phishing campaigns and exploiting unpatched vulnerabilities to leveraging legitimate remote access tools like RDP and PsExec for lateral movement, Medusa is far from a simple attack. It’s a well-coordinated operation designed to infiltrate, evade, and extract. It is important to note that this ransomware is not related to the MedusaLocker ransomware or the Medusa mobile malware.
Technical Drill-down
Initial Access – Medusa developers typically recruit initial access brokers (IABs) in cybercriminal forums and marketplaces to obtain entry to potential victims. Medusa offers these affiliates potential payments ranging from $100 USD to $1 million USD, along with the opportunity to work exclusively for the company. Commonly used techniques to gain initial access include phishing campaigns and exploitation of unpatched software vulnerabilities.
Discovery- Medusa actors use living off the land (LOTL) and legitimate tools like Advanced IP Scanner and SoftPerfect Network Scanner for initial user, system, and network enumeration. They leverage PowerShell and Windows Command Prompt for network and filesystem calculation and to utilize Ingress Tool Transfer Capabilities. They also use Windows Management Instrumentation (WMI) to query and gain system information.
Defense Evasion— Living off the Land (LOTL) techniques are used to avoid detection. They also use Certutil (certutil.exe) to avoid detection while performing file ingress and multiple PowerShell detection evasion techniques, attempting to cover their tracks by deleting the PowerShell command line history.
Lateral Movement and Execution – A wide variety of legitimate remote access tools including AnyDesk, Atera, ConnectWise, eHorus, N-able, PDQ Deploy, PDQ Inventory, SimpleHelp, and Splashtop in combination with Remote Desktop Protocol (RDP) and PsExec, are used to move laterally through the network and identify files for exfiltration and encryption. Mimikatz has also been observed in use for Local Security Authority Subsystem Service (LSASS) dumping to harvest credentials and aid lateral movement.
Exfiltration and Encryption – Threat actors install and leverage Rclone to facilitate exfiltration of stolen data to the Medusa C2 server. The actors use Sysinternals PsExec, PDQ Deploy, or BigFix to deploy the encryptor, gaze.exe, on files across the network, with the actors disabling Windows Defender and other antivirus services on specific targets. Encrypted files have a “.medusa” file extension. The process gaze.exe terminates all services related to backups, security, databases, communication, file sharing and websites, then deletes shadow copies and encrypts files with AES-256 before dropping the ransom note. The actors then manually turn off and encrypt virtual machines and delete their previously installed tools.
Extortion – A double extortion model is employed, and victims must pay ransom to decrypt their files and prevent their files from being publicly released. The ransom note demands victims make contact within 48 hours via either a Tor browser based live chat, or via Tox, an end-to-end encrypted instant-messaging platform. If the victim does not respond to the ransom note, Medusa actors will reach out to them directly by phone or email. Ransom demands are posted on the site, with direct hyperlinks to Medusa-affiliated cryptocurrency wallets. At this stage, Medusa concurrently advertises the sale of the data to interested parties before the countdown timer ends. Victims can additionally pay $10,000 USD in cryptocurrency to add a day to the countdown timer.
Nagomi Platform’s Coverage for the Medusa Campaign
How ready is your organization to defend against Medusa? The Nagomi Proactive Defense Platform is built to help you answer that critical question. It provides real-time visibility into your security posture and identifies vulnerabilities that could be exploited in an attack, like Medusa.
Step 1: Log into your Nagomi Platform and click “Campaigns” from the left menu. Search for “Medusa” in the search menu to locate the Medusa Ransomware Campaign. Then, click “Explore More”.
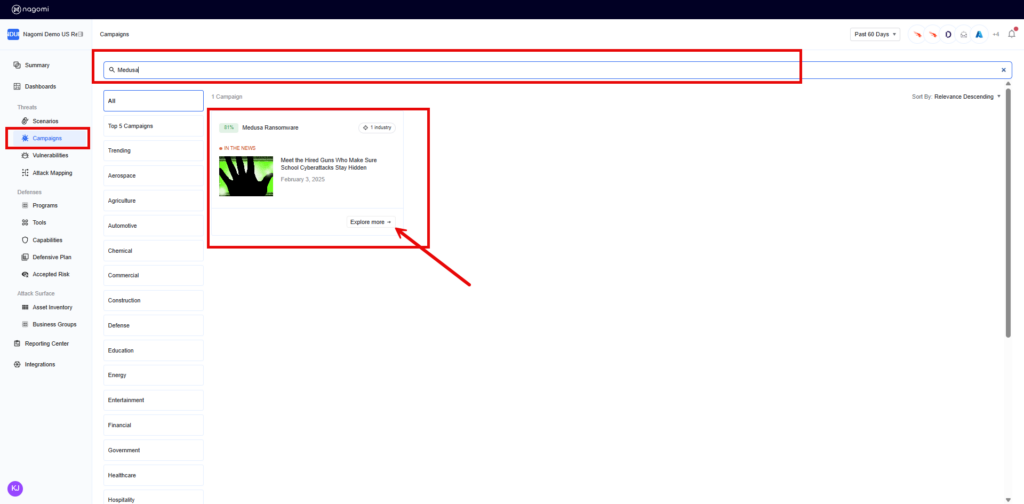
Step 2 – This campaign overview page provides teams with a high-level overview of your organization’s preparedness against Medusa Ransomware. This page includes the following information:
- Top Susceptible Techniques: Highlights the techniques your organization is most susceptible to based on analyzing the attack campaign, utilization of your deployed security tools, and your overall attack surface.
- MITRE ATT&CK Mapping: Highlights how prepared your organization is against the various MITRE tactics being used in the chosen threat campaign.
- Known Exploitable Vulnerabilities: Highlights if any CISA KEV’s are being leveraged as part of the attack campaign.
- Defensive Plans: Recommended remediation steps that can be taken to improve organizational security posture against Medusa ransomware based on the gaps identified by the Nagomi platform.
- All Defensive Capabilities: Highlights all your existing deployed defensive controls with their identified coverage gaps and how they would potentially impact your security posture.
- Missing Capabilities: Highlights those defensive capabilities (security controls) that your organization is currently missing and needs to add to ensure comprehensive protection against the Medusa ransomware threat.
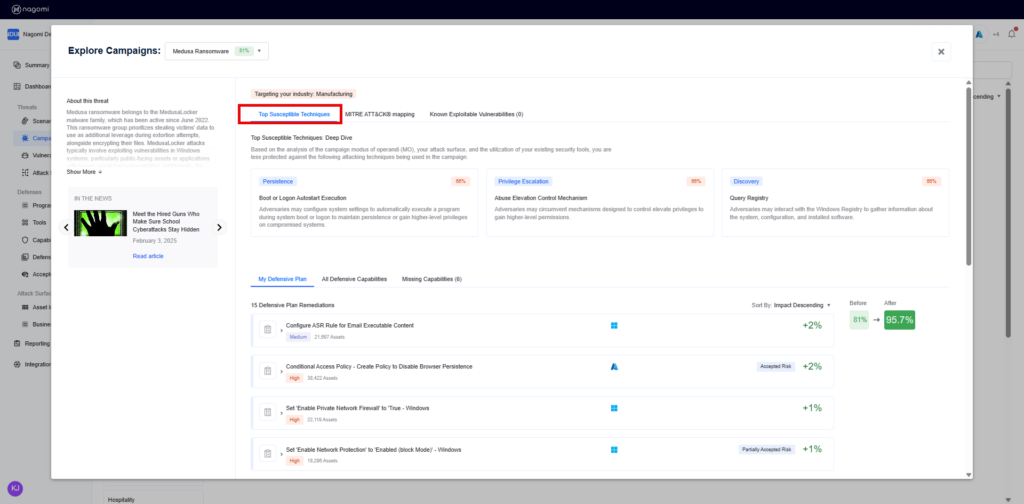
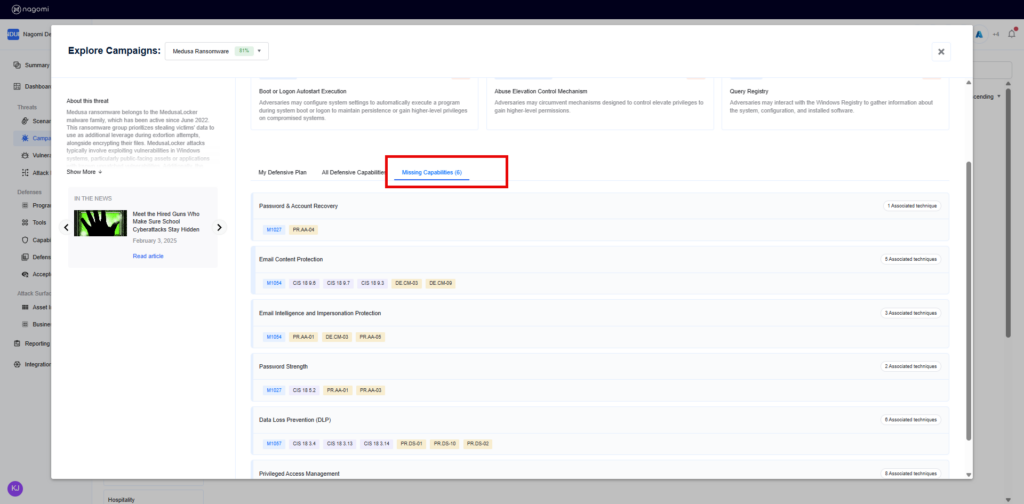
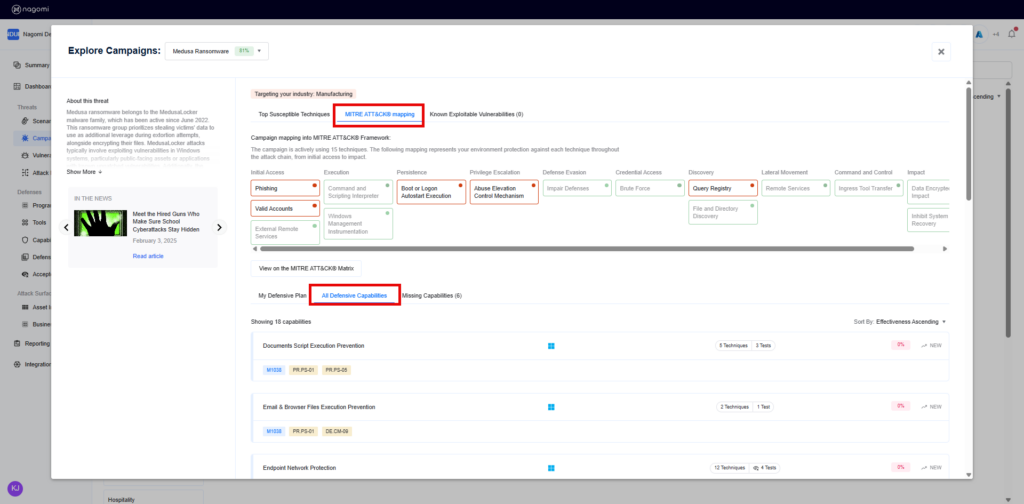
Step 3: Leverage the top 15 remediation recommendations provided by Nagomi to quickly begin the process of fixing identified security gaps.
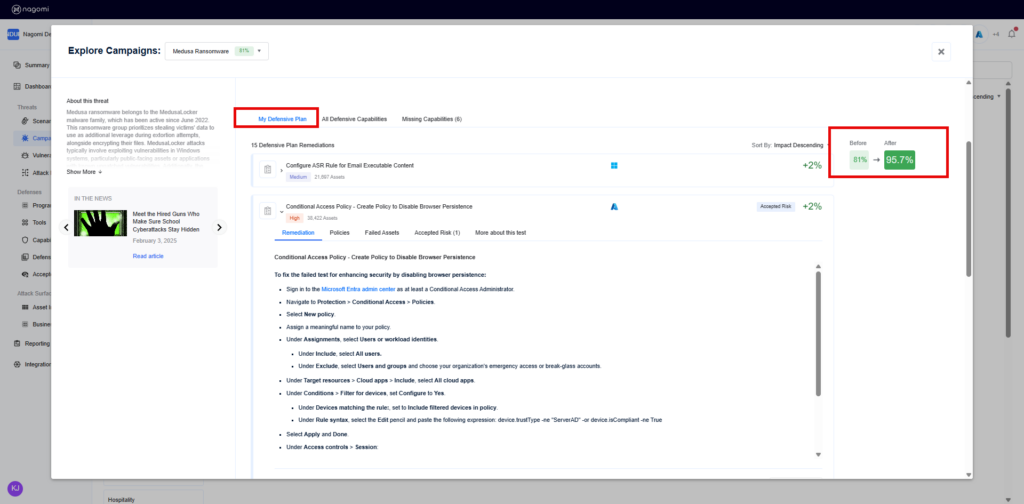
Nagomi’s remediation recommendations are intended to provide incident responders with results-driven steps that can be taken to reduce their mean-time-to-remediate (MTTR).
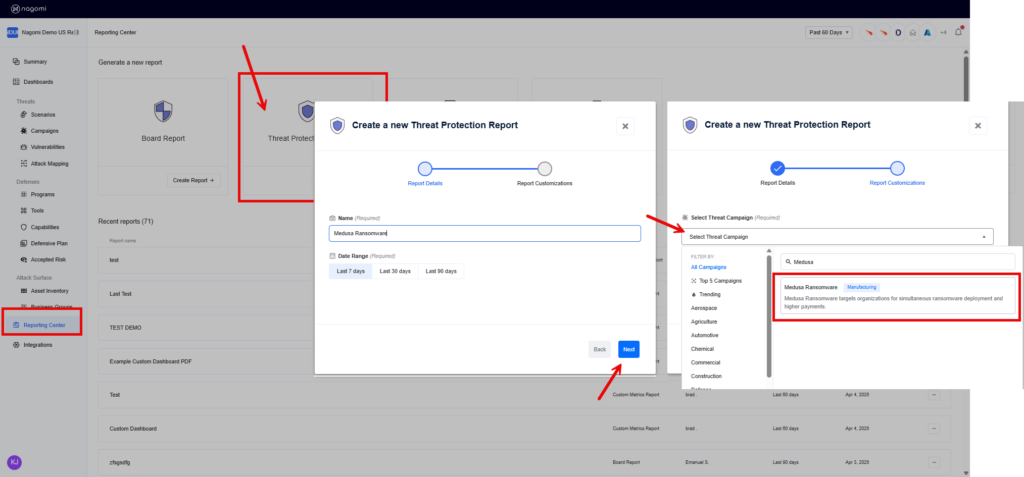
While identifying and closing gaps is a crucial aspect, it’s equally important to effectively communicate organizational preparedness to non-technical stakeholders, such as the Board. The Nagomi platform simplifies this process by providing SecOps teams with customizable reports and dashboards that can be quickly created to report program health. In this case, to specifically report organizational readiness against the Medusa ransomware campaign, simply click on the “Reporting Center” item from the left-hand menu and select the “Threat Protection Report.”
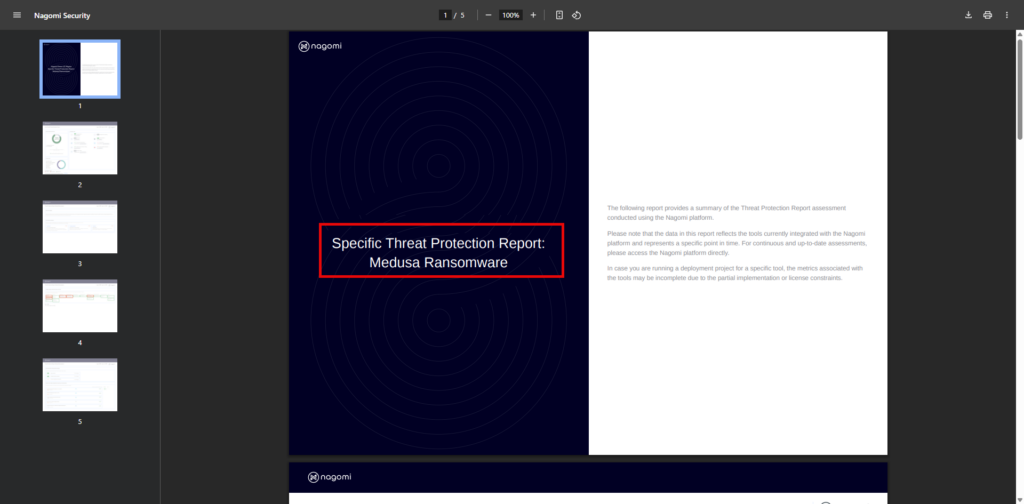
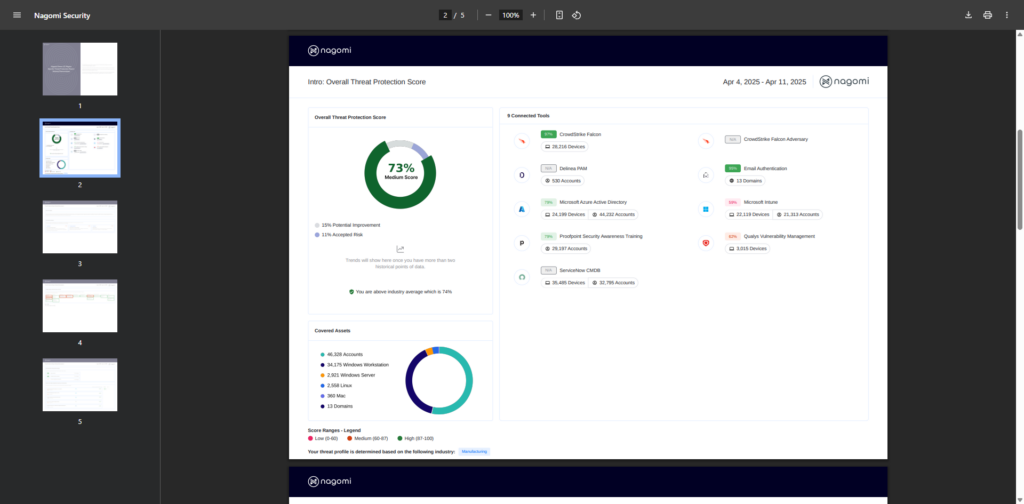
The final report is generated in an easy-to-understand visual PDF format that can be used to communicate organizational preparedness. The report below is the same report that teams can leverage to highlight their organization’s readiness against the Medusa ransomware to all of their stakeholders (both technical and non-technical).
Important Note
The FBI, CISA, and MS-ISAC recommend organizations implement the mitigations below to improve cybersecurity posture based on threat actors’ activity. Recommendations include:
- Implement a recovery plan to maintain and retain multiple copies of sensitive or proprietary data and servers in a physically separate, segmented, and secure location.
- Require all accounts with password logins (e.g., service accounts, admin accounts, and domain admin accounts) to comply with NIST’s standards.
- Require multifactor authentication for all services to the extent possible, particularly for webmail, virtual private networks, and accounts that access critical systems.
- Keep all operating systems, software, and firmware up to date.
- Audit user accounts with administrative privileges and configure access controls according to the principle of least privilege
- Additional mitigation recommendations can be seen in the advisory.
Conclusion
The reality is simple: Cyber threats like Medusa aren’t waiting around, and neither should you. Ransomware actors are evolving, and as they adapt, so must your defense strategies. It’s no longer enough to react to an attack once it’s already made its way through your defenses. The key to staying secure lies in anticipating the next move and closing vulnerabilities before they can be exploited.
The Nagomi Platform gives you the visibility and tools needed to not only detect and respond to threats, but also to continuously evaluate and improve your security posture. It’s about staying ahead of the curve and creating a resilient defense that can handle whatever comes next. Because in cybersecurity, the best defense is a relentless, forward-thinking strategy. One that’s always preparing, always improving, and always ready.