
Table of Contents
The second in a five part series looking at where security teams can understand the most commonly exploited gaps in defenses and how they can use their existing security tools to defend against real-world threats.

By Leeya Shaltiel – Security Researcher
Overview: What is a MITRE ATT&CK Technique?
In the MITRE ATT&CK Matrix for Enterprise, techniques describe the methods an adversary uses to achieve a tactical objective through specific actions. With over 200 techniques and 435 sub-techniques, how should security teams prioritize them?
MITRE ATT&CK Technique Prioritization
To help customers decide what techniques to prioritize, Nagomi analyzed the techniques used most frequently in groups and campaigns. We then cross-referenced the techniques, groups, and campaigns against defenses to pinpoint where security teams can make the most impact. Leveraging our vast dataset encompassing hundreds of campaigns and monitoring millions of assets, the analysis calculates and prioritizes techniques rooted in real-world threats coupled with insights into tool underutilization.
Top MITRE ATT&CK Techniques with the Largest Security Tool Underutilization
Here are the most frequently used techniques with the biggest tool underutilization in cybersecurity today:
Command and Scripting Interpreter
What is the Command and Scripting Interpreter in MITRE ATT&CK Terminology?
In MITRE ATT&CK Terminology, the Command and Scripting Interpreters are interfaces that allow the execution of commands and scripts on a computer’s operating system. These interfaces and languages, such as PowerShell, Bash, or Python, provide ways of interacting with computer systems and are a common feature across many platforms.
These tools are accessible to users and potential adversaries because they offer powerful system management and automation capabilities, making them essential for legitimate administrative tasks and attractive targets for exploitation. Adversaries may abuse command and script interpreters to execute harmful commands or scripts, leveraging these to gain unauthorized access, escalate privileges, and move laterally within a network.
Example Group Using Command and Scripting Interpreters: BlackCat (ALPHV)
BlackCat, also known as ALPHV, is a sophisticated ransomware group that emerged in late 2021. According to CISA, since mid-December 2023, the healthcare sector has been the most commonly victimized by this group among nearly 70 leaked victims. BlackCat quickly became well known due to its advanced capabilities and for being the first known ransomware written in the Rust programming language. A notable example of their use of the Command and Scripting Interpreters technique is deploying PowerShell scripts to alter security features. Specifically, BlackCat has been observed executing PowerShell commands to modify Windows Defender’s settings, such as adding exclusions to bypass real-time monitoring, allowing them to operate undetected and escalate their attacks.
3 Ways to Defend Against Command and Scripting Interpreters Using Existing Security Tools
At Nagomi, we believe in addressing threats and techniques holistically, focusing on minimizing the chances before an attack, preventing execution during an attack, and mitigating risks after an attack. By considering the entire attack chain, we can ensure a robust and effective defense. The following section outlines three comprehensive ways to enhance your defense against Command and Scripting Interpreters. For each capability, we’ll describe the defensive mechanism and provide a detailed example.
A. Before the Technique: Minimizing Access with Network Protection
To minimize the chance an adversary gains access to a shell, network protection capabilities are crucial. Implementing network protection can prevent compromised accounts from accessing target networks, as seen in BlackCat (ALPHV) attacks.
Example #1: Using Zscaler Internet Access (ZIA) “URL Filtering Policy” feature
Zscaler Internet Access (ZIA) helps prevent unauthorized access by inspecting all internet traffic and enforcing security policies. Leveraging URL Filtering, ZIA blocks access to malicious or unauthorized websites by categorizing URLs and enforcing policies that restrict access to high-risk sites. Administrators can create custom URL filtering policies to allow or block specific categories, ensuring that only safe and authorized websites are accessible.
For more information about creating URL Filtering Policy in ZIA, visit ZIA Documentation.
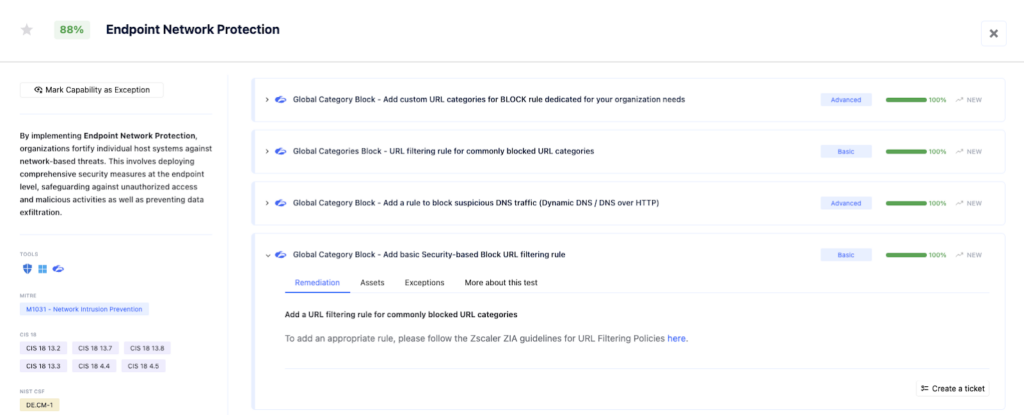
B. During the Technique: Preventing Scripts Execution with Endpoint Detection and Response (EDR)
Implementing Endpoint Detection and Response (EDR) solutions enables real-time monitoring and analysis of command-line activities. EDR solutions such as CrowdStrike Falcon, SentinelOne, and Microsoft Defender for Endpoint can detect unusual command-line activities, terminate malicious processes, and isolate compromised systems to prevent further spread. These tools detect anomalies and respond to potential threats by analyzing behaviors and patterns associated with scripting interpreters, effectively mitigating the risk of malicious activities.
Example #1: Using CrowdStrike Falcon “Suspicious Scripts and Commands” feature
CrowdStrike Falcon includes a feature called “Suspicious Scripts and Commands” which blocks the execution of unauthorized or suspicious scripts. This feature monitors script execution in real-time, identifying and stopping potentially malicious scripts from running. By analyzing the behavior of scripts, it can prevent exploitation attempts that leverage scripting languages such as PowerShell, and JavaScript.
Example #2: Using CrowdStrike Falcon “Sensor Machine Learning – Sensor Anti-Malware” feature
CrowdStrike Falcon’s Sensor Anti-Malware feature uses machine learning to detect and prevent malicious activities. By analyzing patterns and behaviors, it can identify suspicious scripts and commands, blocking them before they can cause harm. This proactive approach helps in mitigating risks associated with command and scripting interpreters by stopping potential threats at the sensor level.
Example #3: Using Microsoft Defender “Execution of Potentially Obfuscated Scripts” feature
Protecting against obfuscated scripts is crucial as adversaries often use obfuscation techniques to hide their malicious code. Microsoft Defender provides an Attack Surface Reduction (ASR) rule that leverages the AntiMalware Scan Interface (AMSI) to detect and block the execution of potentially obfuscated scripts.
For more information about Microsoft Defender ASR rules, visit Microsoft Defender Documentation.
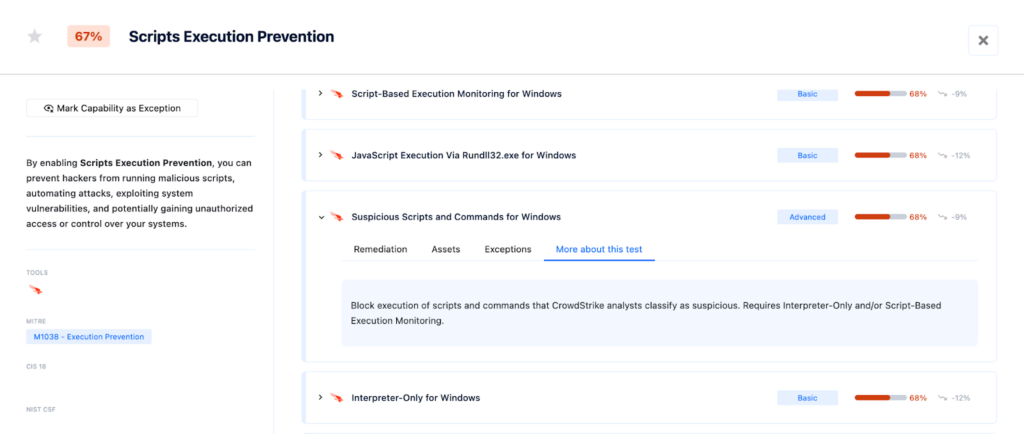
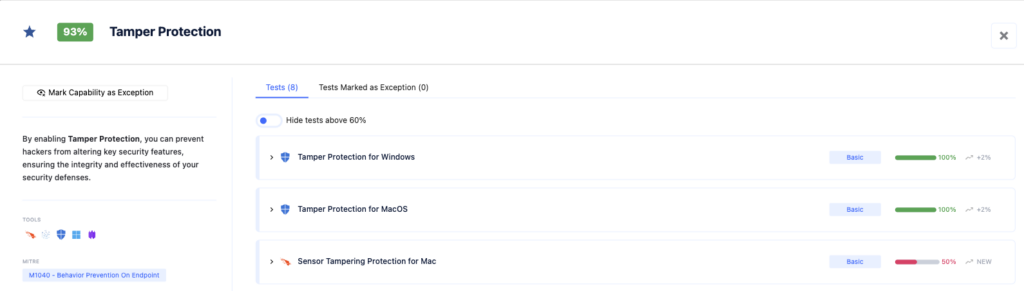
C. After the Technique: Mitigating Risk with Tamper Protection
If an adversary successfully executes a command or script, it is essential to have mechanisms in place to mitigate the impact and prevent further damage.
Example: Using Microsoft Defender Tamper Protection
Microsoft Defender’s Tamper Protection helps prevent changes to security settings that could make a system vulnerable. This feature blocks attempts to modify critical security settings, ensuring that security measures remain effective. In the case of BlackCat (ALPHV) ransomware, adversaries used PowerShell commands to alter Windows Defender’s real-time monitoring. With Tamper Protection enabled, such attempts to alter or disable security features would be blocked, maintaining the integrity of the protection mechanisms. Tamper Protection safeguards key security features from being disabled or altered by malware, continuously monitoring and alerting on tampering attempts, providing ongoing defense against further exploitation after an initial compromise.
For more information about enabling Tamper Protection in Microsoft Defender, visit Microsoft Documentation.
Summary
Here we understand the critical need for organizations to prioritize defenses against Command and Scripting Interpreter techniques, given their frequent exploitation by adversaries. By analyzing real-world threat data, Nagomi identifies these techniques as high-risk yet often underprotected areas in cybersecurity.
Highlighting the example of BlackCat (ALPHV), the blog illustrates how adversaries exploit PowerShell and other scripting languages to bypass security measures and escalate attacks. To mitigate these risks, the blog recommends proactive measures across three fronts: leveraging network protections to minimize initial access, implementing EDR solutions for real-time monitoring and response during attacks, and employing tamper protection features to safeguard against post-compromise manipulation of security settings.
By adopting these strategies and optimizing the use of existing security tools like Zscaler, CrowdStrike Falcon, and Microsoft Defender, organizations can effectively bolster their defenses against Command and Scripting Interpreter techniques, thereby reducing vulnerabilities and enhancing overall cybersecurity resilience.
To see how Nagomi can help you maximize the effectiveness of your tools, check out the Nagomi Proactive Defense Platform or book a demo.



