back to blog
BLOG
Automating Security Processes: Nagomi’s Approach to Reducing Manual Cybersecurity Bottlenecks
From our conversations with security leaders around the world, it’s clear that organizations are still struggling to aggregate data from their various security tools – a process that is frequently manual and inefficient. The volume and heterogeneity of the data make it very time-consuming for analysts to manually correlate and analyze it. What’s more, the dynamic nature of the attack surface, threat landscape and security controls means any manual analysis is likely obsolete the moment it is completed. These bottlenecks inhibit security teams from efficiently interpreting and taking action on the data, resulting in growing security debt.
Solving this problem by automating the work of correlating and normalizing data enables organizations to see the insight within the data and take faster, more focused action. In this blog, we’ll examine the major areas of these bottlenecks and how Nagomi’s Proactive Defense Platform automation helps enhance the accuracy of insights, reduce response times, and support stronger overall security posture.
Removing the Bottlenecks of Manual Security Processes with Security Automation
Reliance on manual processes within cybersecurity creates several inefficiencies. Although every organization is unique and we hear dozens of different ways prospective customers are experiencing this pain, we’ve called out the five areas we hear about most frequently and how Nagomi helps remove those bottlenecks to increase efficiency and accuracy.
Data Collection, Correlation and Analysis
Most security teams utilize a broad range of security tools, including things like endpoint protection, identity provider, device management, email security, and vulnerability scanners. These tools frequently operate independently, generating data in disparate formats and storing it across isolated repositories. With no common taxonomy, security analysts must manually aggregate, normalize, and analyze the data to obtain a comprehensive view of the security environment. To make matters worse the lack of context in the tools often means the data doesn’t just align cleanly – imagine an MDM or network-based vulnerability scanner reporting that 3 different IP addresses are 3 hosts when they’re actually 3 interfaces on the same host for example. This manual effort, often done in spreadsheets, consumes significant time and introduces the potential for human error, which can delay the detection of critical misconfigurations and compromise the accuracy of security assessments.
Nagomi integrates with a wide array of security tools and normalizes disparate data into a centralized platform. By correlating telemetry from all sources, the platform eliminates the need for manual spreadsheets and provides an immediate, contextualized view of assets.
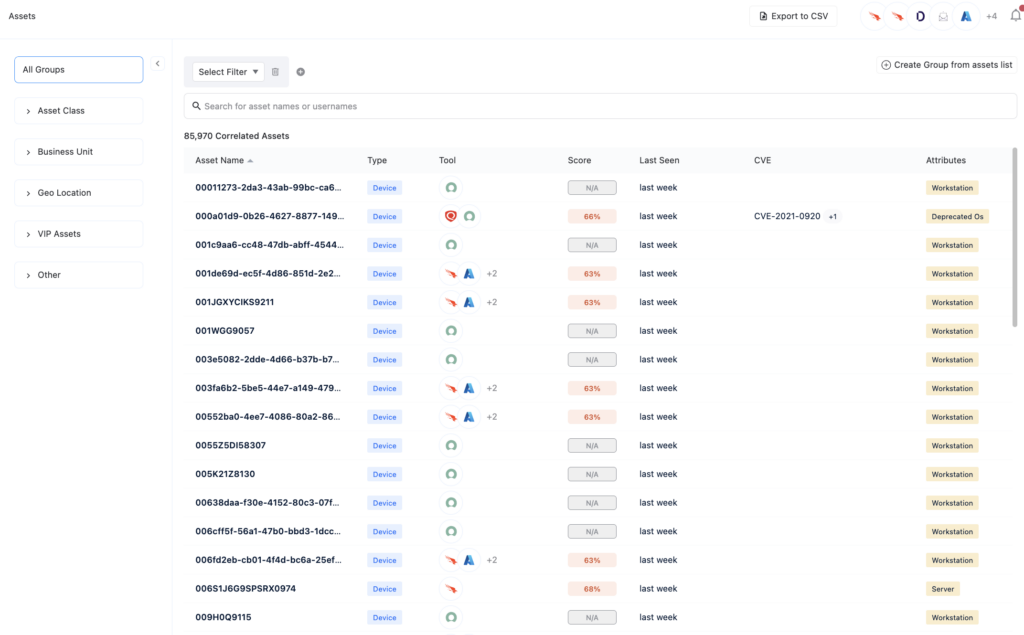
Validating Configuration and Policy Compliance
Ensuring the correct configuration of security tools and adherence to security policies is paramount for maintaining a strong security posture. Misconfigurations and deviations from security policies can increase risk exposure. However, manually identifying misconfigurations and policy drift requires substantial effort, as analysts must regularly review tool configurations, system settings, and audit policies to detect deviations from established baselines. In order to improve usability, most tools apply policy using abstraction like groups or tags, but this abstraction can make it hard to know for sure that you’ve applied policy to all of the right assets.
Nagomi continuously monitors your environment to detect misconfigurations and drift from established policies. The platform does the challenging work of assessing which policies are actually in effect for each asset. Rather than relying on periodic audits, the platform offers near real-time visibility into configuration issues—flagging them automatically and mapping them to business-relevant risk, so that remediation can be prioritized effectively.

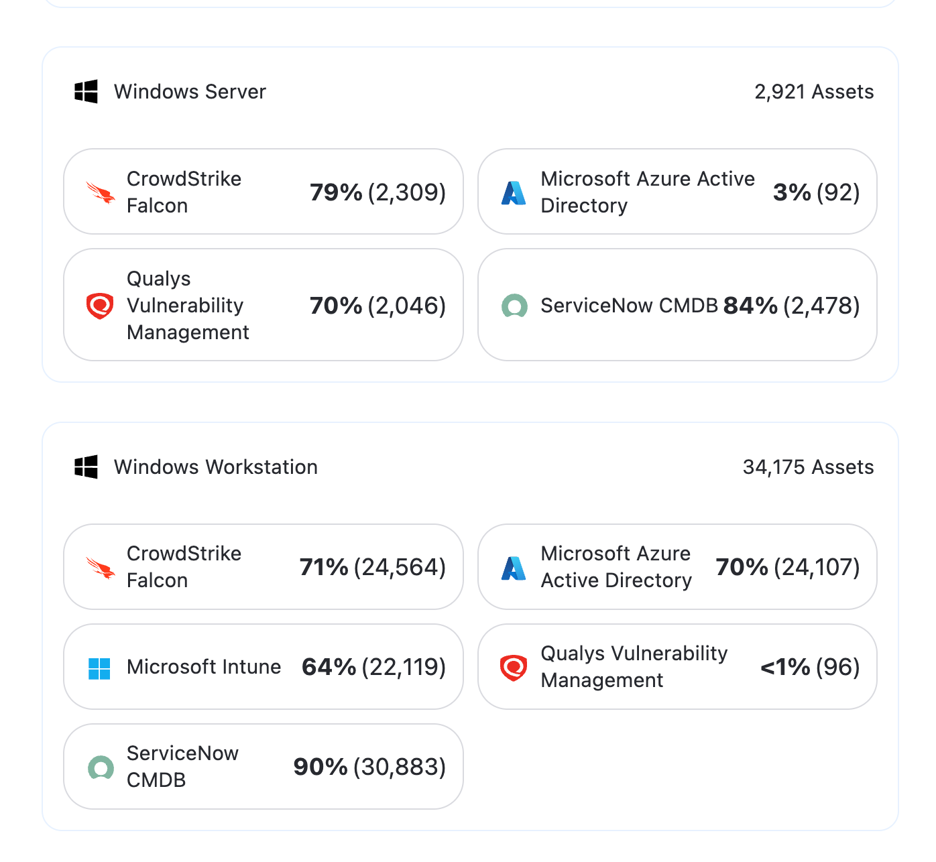
Validating Tool Coverage
Organizations must also address the challenge of identifying gaps in security coverage – a perfect policy is useless if the tool isn’t installed on the endpoint. Nagomi uses the correlated data from your security tools to discover all of the assets and identify where an asset is covered by one tool, but not another. Any individual tool can only report that it’s covering what it knows about – Nagomi knows about every asset from every tool and can help analysts easily find and fill gaps in coverage. Just selecting a couple of items in an asset filter can quickly highlight all systems with endpoint protection that aren’t being scanned for vulnerabilities.
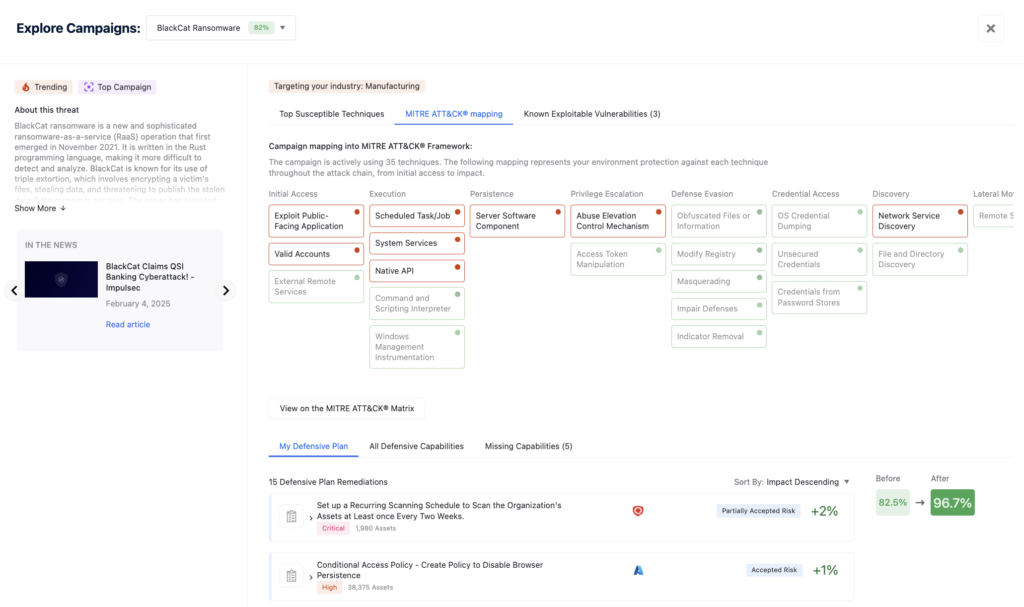
Threat and Control Mapping
Another challenge lies in threat and control mapping; the process of assessing your security policy against an adversary’s known tactics to understand where the gaps and exposures are, and where policy changes could improve resilience.. Manually mapping threats and controls is a complex undertaking, particularly in expansive and dynamic environments. Analysts must meticulously review threat intelligence reports, security control documentation, and system configurations to establish relevant connections. Maintaining the currency of this mapping is also difficult as both threats and systems evolve, potentially leading to a diminished security posture.
Nagomi leverages MITRE ATT&CK to automatically align threat actor leveraged tactics & techniques with the organization’s defenses. It dynamically evaluates which techniques are best defended, and where you’re most exposed—empowering teams to close those gaps proactively.
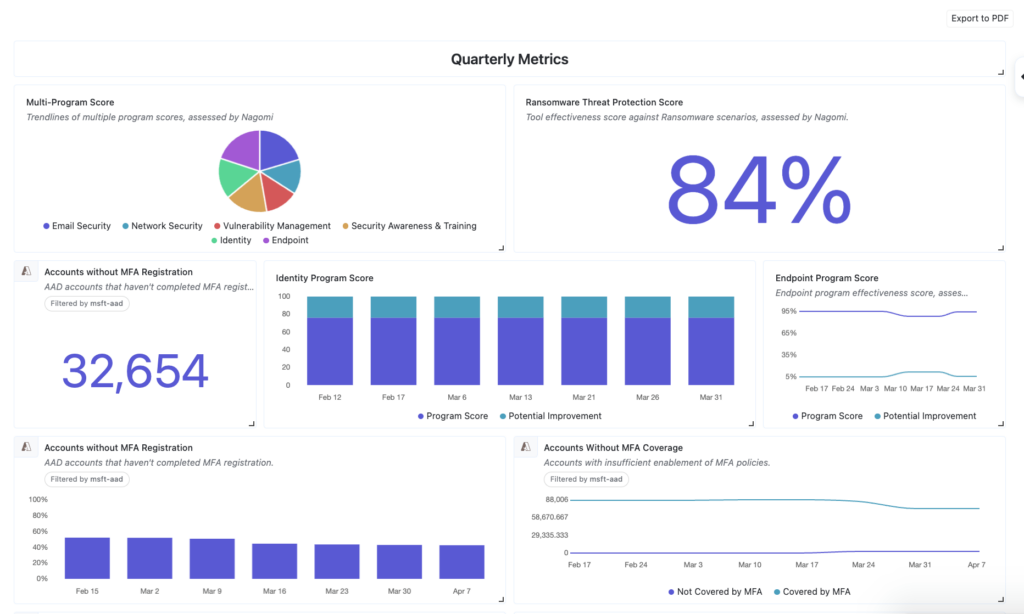
Executive Reporting
Finally, manually generating reports for the leadership team that reflect the organization’s security posture in aggregate, aligning programs to business objectives and KPIs is one of the most common frustrations we hear. Manually creating these reports often necessitates tasking multiple analysts every month or quarter to consolidate data from multiple sources, summarize key findings, and present information clearly and concisely. Manually compiling this data is a time-consuming and error-prone process, potentially affecting the accuracy and consistency of the information presented.
With Nagomi, executive reporting is streamlined through automated, customizable dashboards that link security posture to business objectives. Nagomi reduces the manual burden of monthly or quarterly reporting cycles and ensures leadership teams get clear, accurate insights into program performance, risk reduction, and ROI—without relying on spreadsheets.
Using Automation to Shift to a Proactive Operational Model
Replacing traditional manual processes with a comprehensive automation solution like the Nagomi Proactive Defense Platform frees security teams to work more strategically. When analysts are no longer bogged down by repetitive tasks, they can allocate more time to high-value activities like threat hunting, incident response, and long-term risk mitigation.
Consistency and accuracy also improve when manual variability is minimized. Automation helps ensure that checks and validations are performed uniformly, reducing the likelihood of misconfigurations and missed alerts. By reducing the cognitive load on security analysts, automation can contribute to lower burnout and higher job satisfaction.
Additionally, automation supports ongoing compliance efforts. Instead of viewing compliance as an annual or periodic activity, automated systems can provide a continuous stream of relevant data to help organizations stay aligned with regulatory requirements and internal policies.
Ready to Remove the Manual Roadblocks in Your Security Program?
See how Nagomi automates what matters—so your team can focus on what’s next.




