

A new, high-risk vulnerability— CVE-2025-21298 —has emerged, giving hackers yet another way to exploit trusted systems. Discovered last month, this critical flaw affecting Windows Object Linking and Embedding (OLE) technology carries a CVSS score of 9.8, making it a prime target for sophisticated cyberattacks. As attackers innovate to bypass even the most trusted defenses, Nagomi Security can help you stay ahead with a proactive assessment to identify and close gaps before they’re exploited.
Why CVE-2025-21298 Is a Bigger Threat Than You Think
CVE-2025-21298 is a vulnerability within Windows OLE—a technology used to embed and link documents across applications. This vulnerability allows attackers to execute malicious code remotely by sending a crafted email containing a malicious RTF document. When the recipient previews or opens the email in Microsoft Outlook, the vulnerability is triggered, allowing the attacker to execute arbitrary code on the affected system—without requiring any additional user interaction.
RTF files are widely trusted because they’re often used for sharing text and are generally considered safe. However, an infected RTF file when opened or even previewed (in Outlook) can lead to the embedded malicious payload being executed automatically, giving attackers full control of the system. This turns what was once a harmless file format into a serious security risk, highlighting how even routine actions can lead to a major breach.
How to Strengthen Your Defenses Today
At Nagomi, we believe in a proactive, multi-layered approach to security. To ensure resilient defenses against emerging threats, we rely on Microsoft Defender for Office 365 as a key part of this strategy. One of its powerful features, “Extend Considered Suspicious File Types,” helps detect and block potentially dangerous file types, even those that are usually trusted, like RTF files.
Nagomi’s platform integrates with your existing security stack, providing your security teams with full visibility into configuration and policy gaps. This intelligence is correlated and normalized to provide you with appropriate context and tailored recommendations on how to strengthen your defenses against evolving threats.
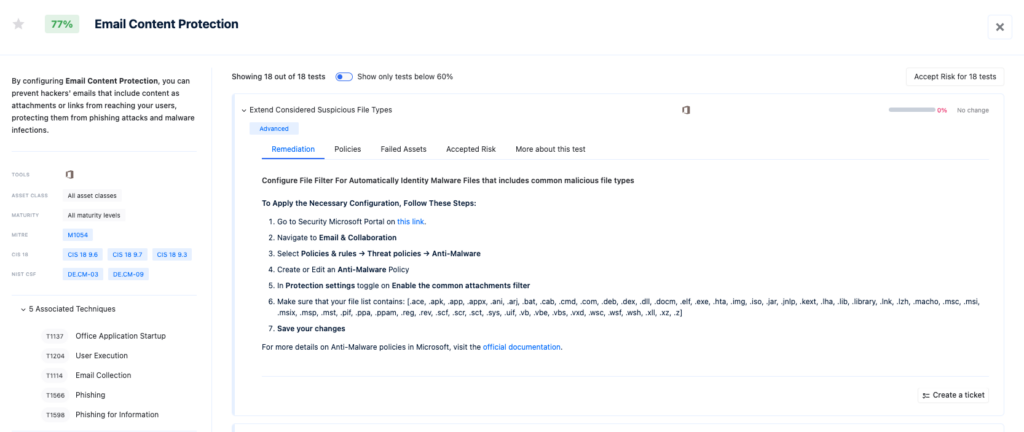
Let’s break it down step-by-step, showing you exactly how to add RTF files to the Suspicious File Types in the Microsoft Defender for Office 365, and automatically filter those types of files to prevent the recipient from opening them.
- Go to Security Microsoft Portal on this link.
- Navigate to Email & Collaboration
- Select Policies & rules → Threat policies → Anti-Malware
- Create or Edit an Anti-Malware Policy
- In Protection settings toggle on Enable the common attachments filter
- Make sure that your file list contains: [.ace, .apk, .app, .appx, .ani, .arj, .bat, .cab, .cmd, .com, .deb, .dex, .dll, .docm, .elf, .exe, .hta, .img, .iso, .jar, .jnlp, .kext, .lha, .lib, .library, .lnk, .lzh, .macho, .msc, .msi, .msix, .msp, .mst, .pif, .ppa, .ppam, .reg, .rev, .scf, .scr, .sct, .sys, .uif, .vb, .vbe, .vbs, .vxd, .wsc, .wsf, .wsh, .xll, .xz, .z, .rtf]
- Save your changes
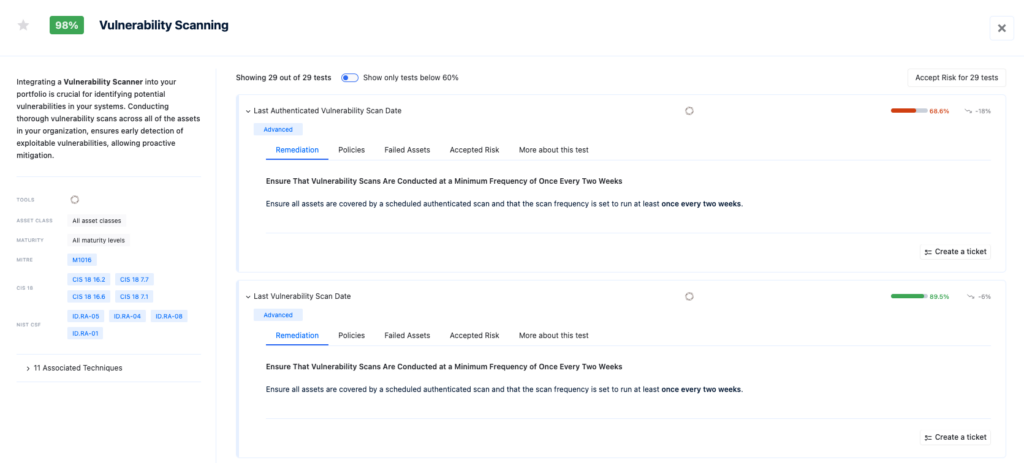
We understand the significance of your vulnerability scanners in this process. With easy read-only API integrations into your vulnerability management tools, Nagomi ensures these tools are not just installed – they’re configured properly and consistently across all departments. For example, the Nagomi Proactive Defense platform will not only identify the CVE-2025-21298 vulnerability, but ensure Microsoft’s patch is correctly deployed to ensure protection against this advanced threat vector. This minimizes the risk of critical vulnerabilities being overlooked, thereby enhancing your overall security posture.
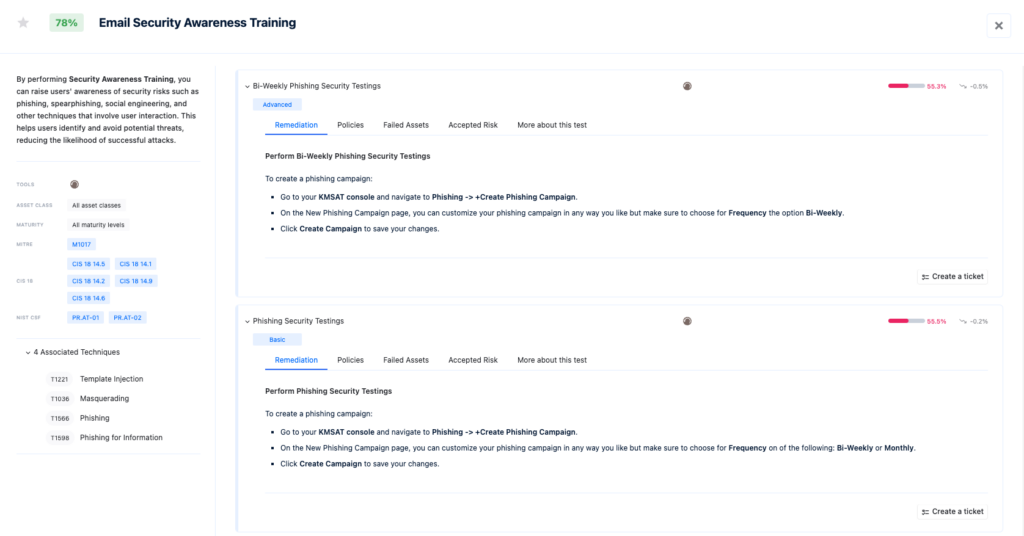
How to Empower the Team With Good Email Hygiene
Another key line of defense against sophisticated email attacks, like those using hidden RTF content, is a well-informed and vigilant workforce. Nagomi helps ensure your team is always prepared by integrating with top security awareness tools to deliver targeted training on threats like CVE-2025-21298.
- Integrated Awareness Solutions:
Nagomi links with your security awareness tools to make sure the right training is reaching the right people. It tracks if training or simulated phishing tests were delivered properly and identifies any gaps in engagement. - Continuous Monitoring and Support:
Nagomi also keeps tabs on how employees respond to simulated phishing tests, providing insights into their readiness to spot and respond to potential threats. This ensures your team is always up-to-date on the latest risks and knows how to act when they encounter suspicious emails or attachments.
This all boils down to preparedness. By integrating these measures, Nagomi can help you build a culture of cyber vigilance—reducing risk and strengthening your overall security posture against email attacks.
Use What You Have. Secure What Matters.
The CVE-2025-21298 vulnerability shows just how easily trusted file formats like RTF can be used to exploit systems. Poor vulnerability prioritization, the failure to assess controls against real-world threats, and the absence of a unified platform to integrate and measure these tools only exacerbate the problem making it nearly impossible to answer the critical question: ‘Are we truly protected?’
Using read-only API connections Nagomi seamlessly integrates with over 50 leading technologies – like Microsoft Defender for Office 365. Deployment is fast, frictionless, and designed to amplify the value of your existing tech stack. Instead of adding unnecessary layers, the Nagomi Proactive Defense Platform automates a thorough assessment of your security controls, connecting the dots between attackers’ tactics, business impact, and your defensive capabilities.
Our goal is simple: We aim to make security effective with your existing tools.
Interested in learning more? Request a demo today.



