
Traditional Exposure Assessments Focus Heavily on CVEs and KEVs
In 2024, the sheer volume of CVEs exploded—nearly 40,000 published, with over 13,000 marked critical or high severity. The standard approach is to rely on CVSS scores and CISA’s Known Exploited Vulnerabilities (KEV) list, hoping these signal which vulnerabilities actually matter. But this creates a brutal paradox: you can’t patch thousands of vulnerabilities, yet ignoring them risks breach.
So what? This flood of CVEs isn’t just a data headache—it leads to alert fatigue, wasted resources, and, worse, a reactive security posture where teams chase noise instead of real threats.
Traditional Exposure Assessments are Losing Relevance
Conventional exposure assessment, often driven by CVSS scores, can be misleading. A CVSS 10 on an air-gapped system poses far less risk than a CVSS 3 on an internet-facing asset. For SOC teams, this results in alert fatigue, wasted cycles, and a reactive posture. Chasing every “critical” vulnerability drains resources and distracts from what actually matters: stopping real, exploitable threats in your environment.
Aren’t KEVs Supposed to Strengthen the Exposure Assessment Process?
CISA’s Known Exploited Vulnerabilities (KEV) catalog does offer a meaningful upgrade to traditional, score-based exposure assessment. This real-world intelligence enables more precise prioritization, helping teams cut through noise and focus on what’s most likely to impact their environment. For SOC leaders, that means faster identification and remediation of high-risk threats, reduced time spent on low-impact issues, and stronger alignment with federal guidance.
While the KEV catalog is useful, it’s only part of the larger picture. Since it focuses on known, actively exploited vulnerabilities, it doesn’t account for zero-days or non-critical CVEs that haven’t yet made the list. Relying on KEVs alone can leave gaps. Also, not every KEV poses a real threat to your organization. Without understanding where your assets are, how your network is set up, and whether your controls are actually working, it’s hard to know which KEVs truly matter. Prioritization should be based on how a vulnerability affects your environment, not just that it’s on a public list.
Why Organizational Context Matters to Exposure Assessments
According to Gartner, 61% of security leaders have suffered a breach in the last 12 months due to misconfigured controls. Most teams manage an ecosystem of 70+ security tools and still struggle to connect the dots fast enough. The real challenge isn’t identifying exposures. It’s zeroing in on those exposures that actually impact your environment, assets, and controls. Effective exposure assessment demands context. Without it, even the best teams risk wasting cycles on low-impact issues while missing what really matters.
Enter Nagomi: Prioritization Built Around Your Environment
Relying only on the CISA KEV list to drive remediation can lead to blind spots. While it flags known, exploited vulnerabilities, it doesn’t account for how those vulnerabilities affect your particular environment. That’s where Nagomi can optimize the exposure assessment process.
Nagomi connects to your existing tools, including EDRs and vulnerability scanners, using read-only APIs to pull in real-time data on active vulnerabilities, assets, and deployed controls. It then shows how those vulnerabilities map to your actual infrastructure, including where controls may be misconfigured or policies missing.
By combining internal asset, security control, configuration, and policy data with external threat intelligence, including KEVs and MITRE ATT&CK, Nagomi delivers a truly unified exposure assessment experience by correlating all four critical signals—attack surface identifiers, exploitable vulnerabilities, control misconfigurations, and tool coverage—at the single asset level. Instead of chasing every alert, your SOC can focus on real exposure and remediate with precision. Benefits of this approach include:
- Detect Risky Combinations– remediate the highest-risk exposures first
- Comprehensive Visibility—data enrichment from multiple sources to provide a holistic, accurate view.
- Unmatched Context— link exploitable CVEs (powered by CISA KEV) with asset configurations and coverage so you understand which assets pose real risk and why.
- Prioritized Remediation Plans– identify coverage gaps, critical misconfigurations, and threat resilience weaknesses across your environment
How To With The Nagomi Platform
Nagomi gives SOC teams a clear, practical path to focus remediation where it counts. Here’s how to use it:
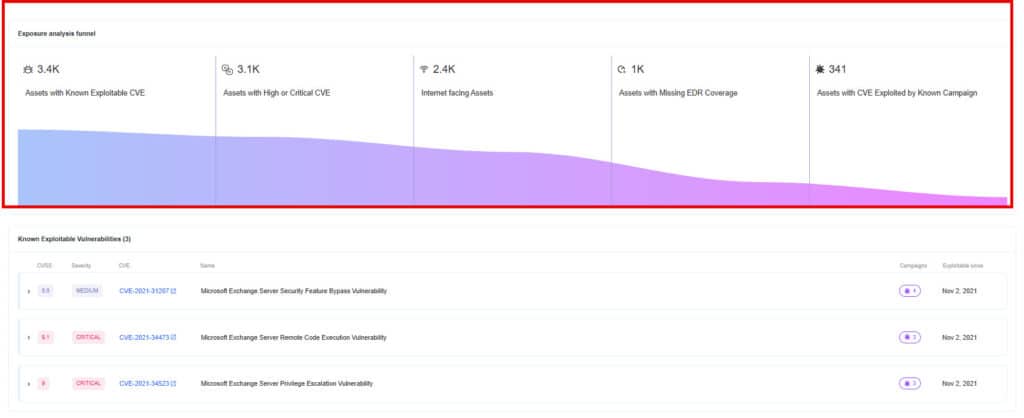
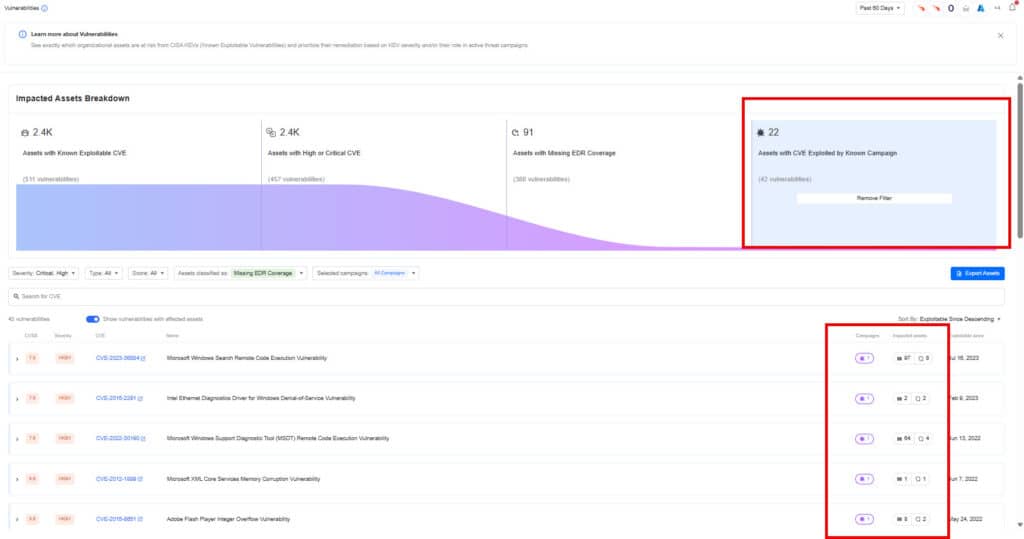
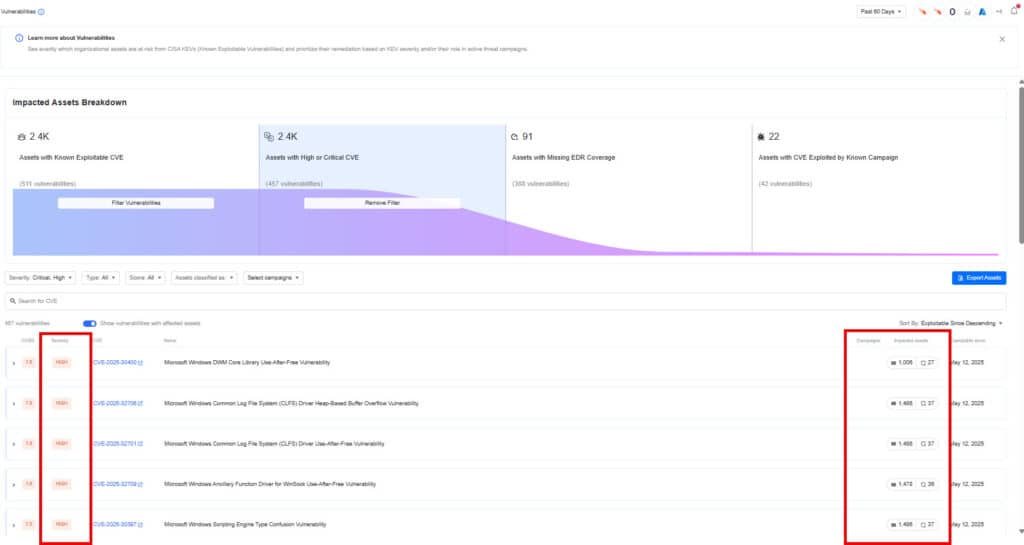
1) Start with the Vulnerabilities Page
Get a prioritized list of all assets affected by CVEs in the CISA KEV database—vulnerabilities known to be actively exploited. Focus your remediation by filtering for:
- Assets with Critical CVEs
- Internet-facing assets
- Assets missing EDR coverage
- Assets with CVEs tied to active threat campaigns
Export the asset list and assign it to the appropriate teams for action.
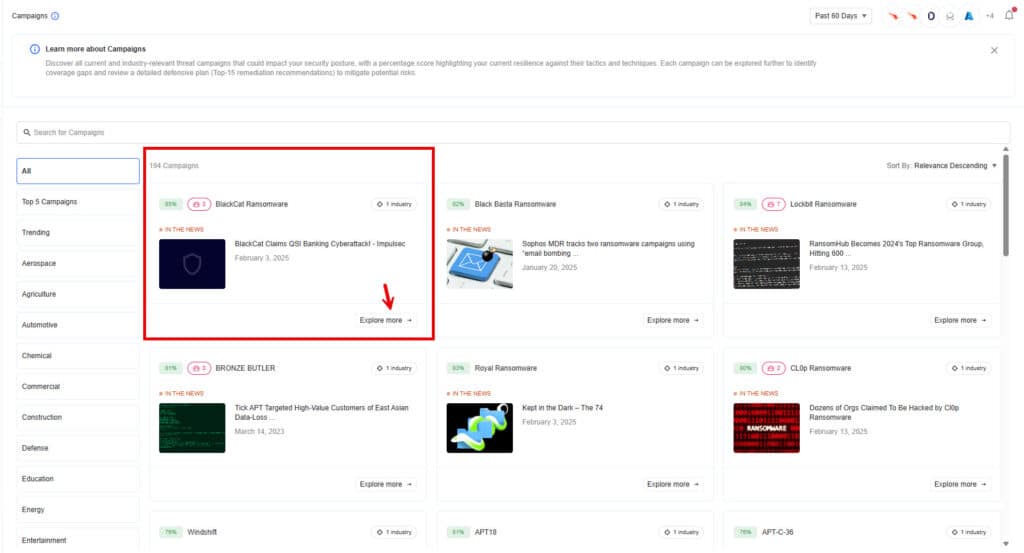
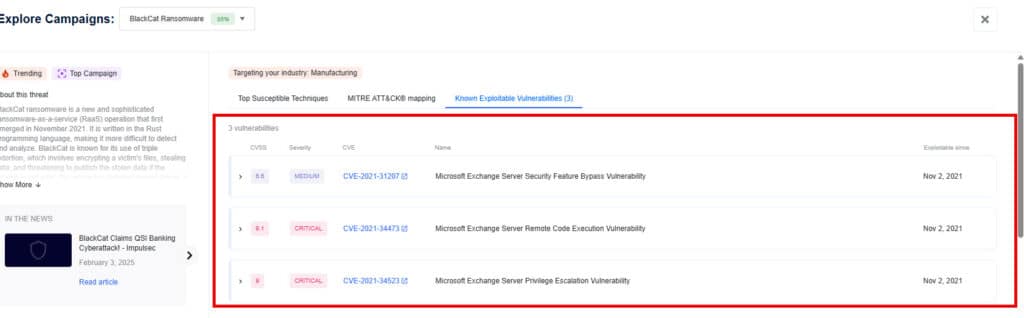
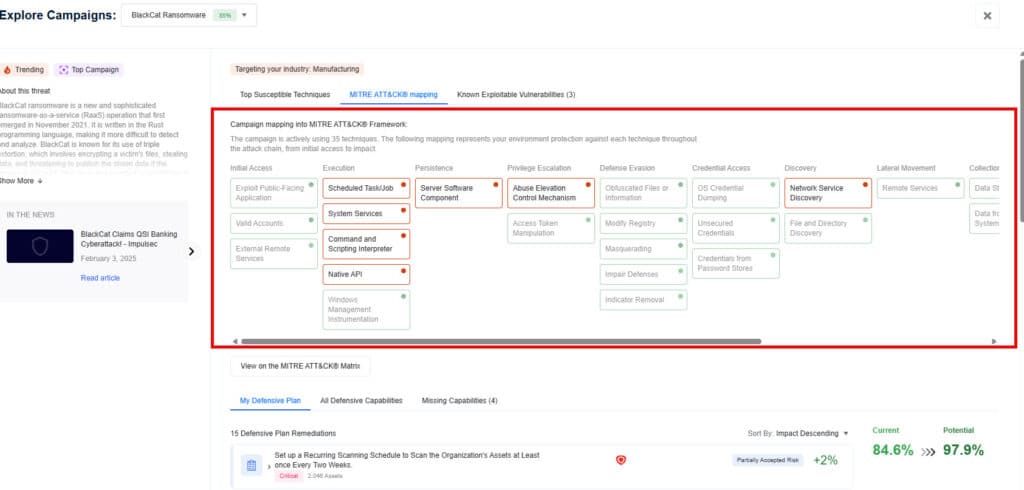
2) Investigate the Campaigns Page
Nagomi maps and correlates threat intelligence feeds (open-source as well as vendor-provided) to your environment, showing which active and relevant campaigns align with your industry vertical and can cause significant impact to your security posture. Each campaign highlights:
- KEVs by the threat actor as part of the campaign
- Exposure gaps mapped to MITRE ATT&CK matrix
Use this to prioritize based on actual threats targeting your industry or environment.
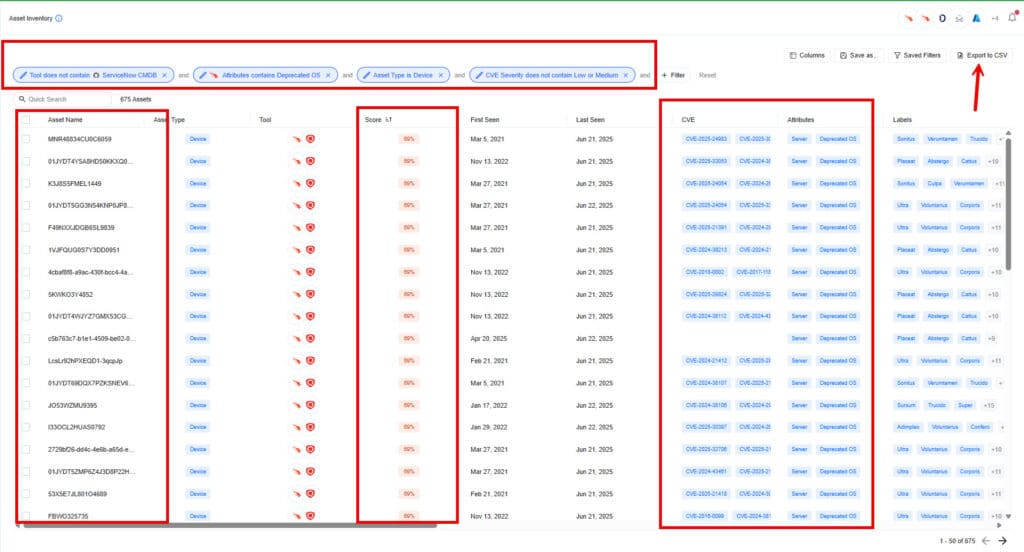
3) Review the Asset Inventory Page
As the Nagomi platform ingests and correlates data from all your connected tools, it can provide you with comprehensive visibility into your entire attack surface from the Asset Inventory page. Nagomi’s asset inventory provides users with rich context that security teams need to assess real risk, enabling them to view attack surface identifiers, exploitable vulnerabilities, tool coverage, and tool misconfigurations on an individual asset level. From this page you can:
- See all of your assets, correlated with proactive context.
- Quickly filter and export asset lists to drive targeted remediation for misconfiguration, coverage, policy gaps, and vulnerabilities (KEV and non-KEV) that pose real risk to your business.
With Nagomi, you’re not just tracking vulnerabilities—you’re taking informed, targeted action.
Why This Matters Today
Cyber threats evolve fast. Your organization can’t afford to be reactive or overwhelmed by vulnerability noise. Nagomi transforms vulnerability management from a technical chore into a strategic advantage, reducing risk, optimizing security investments, and aligning teams.
The question is no longer “How many CVEs do we have?” but “Which exposures put us at risk right now?”
Nagomi gives you that answer so you can finally control your attack surface with confidence. Schedule a demo and learn how Nagomi can help your organization reduce your threat exposure with greater clarity, efficiency, and confidence.


