back to blog
January 7, 2025
Vulnerability Programs are Drowning in Data. Here’s the Fix
A SecOps Workflow for Faster Action
Hadas Bloom

Table of Contents
Finding vulnerabilities isn’t the hard part; the challenge is deciding what actually matters and acting fast. Security teams are flooded with CVEs, scores, and alerts, but real risk reduction comes from prioritizing with context, validating scope with full inventory visibility, and investigating vulnerabilities through the lens of exposure. By connecting a contextual Dashboard for rapid, risk-based prioritization with a unified Inventory for validation, ownership, and execution, teams can stop debating severity and start closing the issues that truly increase risk. Tying CVEs to asset criticality, control gaps, exploitability signals, and broader exposure paths shifts the focus from fixing what is easy or newsworthy to eliminating toxic combinations attackers exploit. The outcome is faster triage, stronger alignment with IT and engineering, clearer reporting, and measurable progress in reducing exposure, not just managing vulnerability lists.

Finding vulnerabilities has never been the hard part. Tools generate CVEs, severity scores, and exploit headlines constantly. The real challenge is making fast decisions and acting on what’s most relevant to the business.
When your security tools are working well, you can answer questions like: What should we patch first? Which vulnerabilities actually create risk in our environment? What connects to broader exposure paths? What can we close this week that makes a real difference?
Getting there requires a shift: prioritize with context, validate with full inventory visibility, and investigate through the lens of exposure. That is the difference between working through a list and actually reducing risk.
Two Views, One Workflow
The most effective vulnerability operations connect prioritization with execution. That means building workflows around two lenses: a dashboard for fast prioritization and an inventory for validation and action. When these work together, you spend less time switching contexts and more time moving forward.
Nagomi’s new Vulnerabilities page brings this approach together. The Dashboard view shows where risk concentrates across your environment. Instead of relying on counts and severity buckets, it highlights the vulnerabilities that deserve attention based on exploitability signals, asset importance, whether they contribute to broader exposure findings, and patterns that appear repeatedly.
It also elevates control-first signals and asset context that shift live risk. You can spot issues tied to missing protections such as EDR, and you can see when a vulnerability sits on an internet-facing system or another high-impact asset. This contextual view reduces time spent debating priorities and increases time spent resolving what matters.
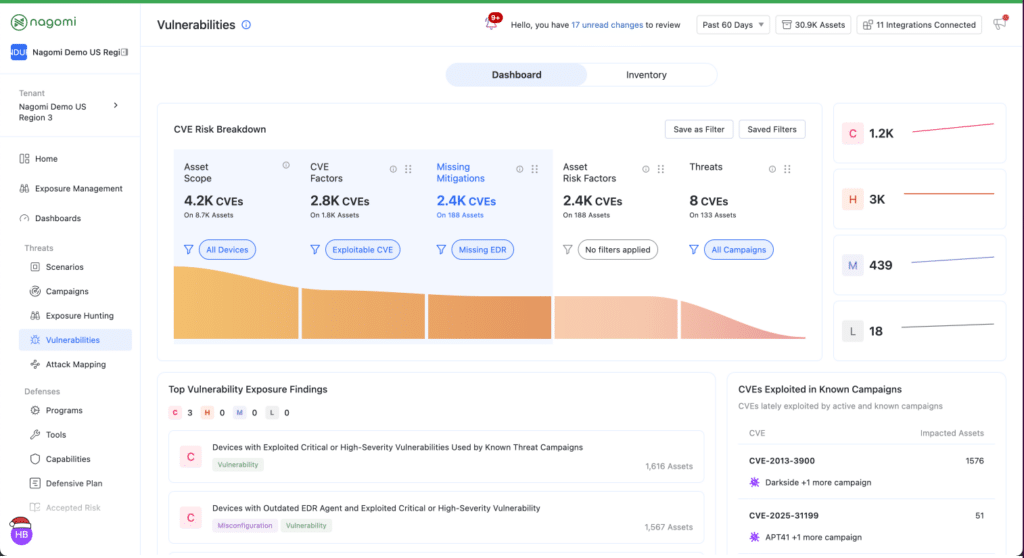
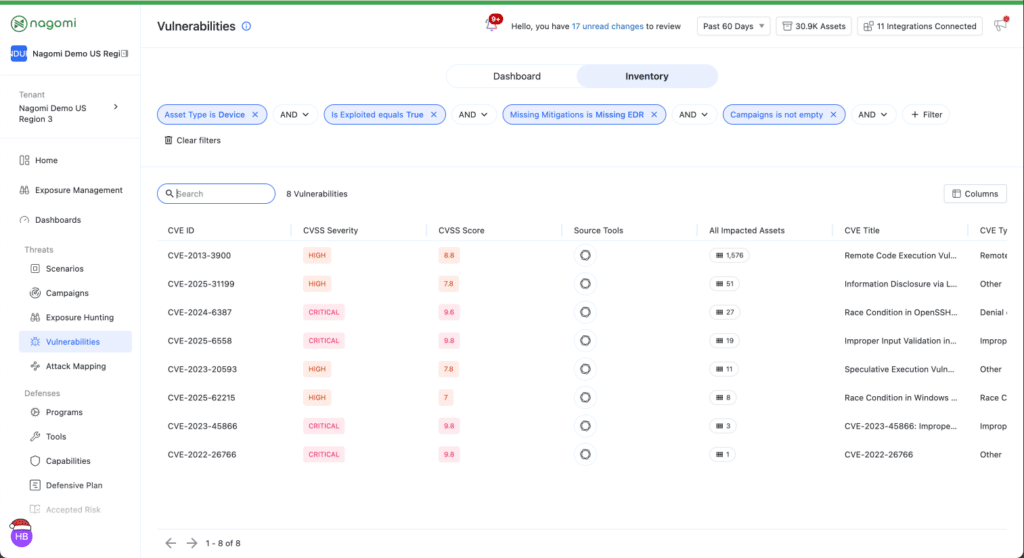
From there, the Inventory view becomes operational. Once you know what matters, you need to validate scope and plan the work. Inventory pulls together CVEs from your connected tools, including vulnerability scanners and CVEs surfaced by controls like EDR. It supports filtering and triage without constant exports, and it includes metadata columns that help you make decisions faster.
This reduces the need to switch between consoles to get a full view of vulnerabilities across your organization. This is where you confirm scope, assign owners, and track closure. Moving from Dashboard to Inventory feels seamless because you work in one place, with the same context, instead of rebuilding it across different tools.
Investigating Exposures, Not Just Isolated CVEs
When you select a specific CVE, the new CVE Drawer supports quick decisions. You can see impacted assets, exploitability insights, and whether the vulnerability forms part of an Exposure Finding, a toxic combination that creates higher risk. When these decision signals live in one place, you avoid two common traps: fixing what is easy instead of what is risky, and chasing headlines instead of reducing exposure.
The highest-risk scenarios usually involve combinations: a vulnerable asset with reachable services, an exploit path, weak identity controls, or misconfigurations that amplify impact. This is where exposure hunting changes the conversation.
The refreshed Exposure Hunting page (formerly the Vulnerability Funnel) lets you identify recurring patterns and explore toxic combinations across the environment. You can pivot between asset-centric and vulnerability-centric investigation, which helps connect the dots between individual CVEs and the exposure paths they contribute to. The work shifts from “How many vulnerabilities did we patch?” to “Which exposure paths did we close?” That is what makes risk reduction tangible.
Turning Prioritization Into Progress
When prioritization, inventory, and investigation connect, a few things change.
- Triage gets faster because you are working from context rather than debating severity scores.
- Alignment with IT and engineering improves because you can show why something matters in your specific environment.
- Backlog work becomes more coherent, tied to exposure rather than volume. And reporting becomes more meaningful when you can show exposure reduction instead of just closure counts.
The Shift
SecOps teams already have plenty of vulnerability data. What makes the difference is a workflow that connects a contextual dashboard, a unified inventory, drill-down into exploitability and impacted assets, and exposure hunting that reveals the combinations driving real risk. When those pieces work together, you stop managing CVEs and start reducing exposure.
Schedule a demo to see how Nagomi helps you prioritize what matters and reduce exposure faster.