
Table of Contents
What it is, latest developments, and how security teams can ensure their security tools are properly configured to minimize the threat

By Matan Tamir – Security Researcher
What is Black Basta Ransomware?
Black Basta (AKA BlackBasta) is a ransomware operator and Ransomware-as-a-Service (RaaS) criminal enterprise that first emerged in early 2022 and immediately became one of the most active RaaS threat actors in the world, racking up 19 prominent enterprise victims and more than 100 confirmed victims in its first few months of operation. Black Basta targets organizations in the US, Japan, Canada, the United Kingdom, Australia, and New Zealand in highly targeted attacks rather than employing a spray-and-pray approach. The group’s ransom tactics use a double extortion tactic, encrypting their victim’s critical data and vital servers while threatening to publish sensitive data on the group’s public leak site.
Black Basta is just one of many cases globally that continue to strike and spread daily. Recent examples include:
- AHA, H-ISAC warn hospitals about Black Basta following Ascension cyberattack (Healthcare IT News)
- CISA and Partners Release Advisory on Black Basta Ransomware (CISA Alert)
- Black Basta Ransomware Hit Over 500 Organizations (SecurityWeek)
- Black Basta ransomware group is imperiling critical infrastructure, groups warn (Ars Technica)
What is Ransomware as a Service (RaaS)?
RaaS known as Ransomware-as-a-Service is a cyber attack model that connects ransomware operators and servers to groups, campaigns, and other adversaries that are willing to pay in order to launch a ransomware attack.
The RaaS market is mature and contains many known services such as Black Basta, LockBit, Hive, and REvil, that aim to harm all kinds of industries around the world.
Although each service and operator has different tools, targets, and motivations, they still have many common characteristics. Most of the time, some preparations, configurations, and a proactive approach can mitigate and reduce the chance of being a victim of those attacks.
Latest Developments with Black Basta Ransomware
In his article for ars technica, Dan Goodin reported on a new development with Black Basta, crediting research from Rapid7:
Recently, researchers from security firm Rapid7 observed Black Basta using a technique they had never seen before. The end goal was to trick employees from targeted organizations to install malicious software on their systems. On Monday, Rapid7 analysts Tyler McGraw, Thomas Elkins, and Evan McCann reported:
Since late April 2024, Rapid7 identified multiple cases of a novel social engineering campaign. The attacks begin with a group of users in the target environment receiving a large volume of spam emails. In all observed cases, the spam was significant enough to overwhelm the email protection solutions in place and arrived in the user’s inbox. Rapid7 determined many of the emails themselves were not malicious, but rather consisted of newsletter sign-up confirmation emails from numerous legitimate organizations across the world.
With the emails sent, and the impacted users struggling to handle the volume of the spam, the threat actor then began to cycle through calling impacted users posing as a member of their organization’s IT team reaching out to offer support for their email issues. For each user they called, the threat actor attempted to socially engineer the user into providing remote access to their computer through the use of legitimate remote monitoring and management solutions. In all observed cases, Rapid7 determined initial access was facilitated by either the download and execution of the commonly abused RMM solution AnyDesk, or the built-in Windows remote support utility Quick Assist.
In the event the threat actor’s social engineering attempts were unsuccessful in getting a user to provide remote access, Rapid7 observed they immediately moved on to another user who had been targeted with their mass spam emails.
Common Ransomware-as-a-Service (RaaS) Techniques and How to Defend Against Them
Like all cyberattacks, ransomware attacks also tend to consist of similar phases, from Initial Access through Lateral Movement and Privilege Escalation to the Impact at the end of the scenario.
Nagomi customers are able to navigate through each phase of the kill chain (based on Mitre ATT&CK framework) and understand the consequences of each technique to their organization and how they can mitigate it using only their current security stack.
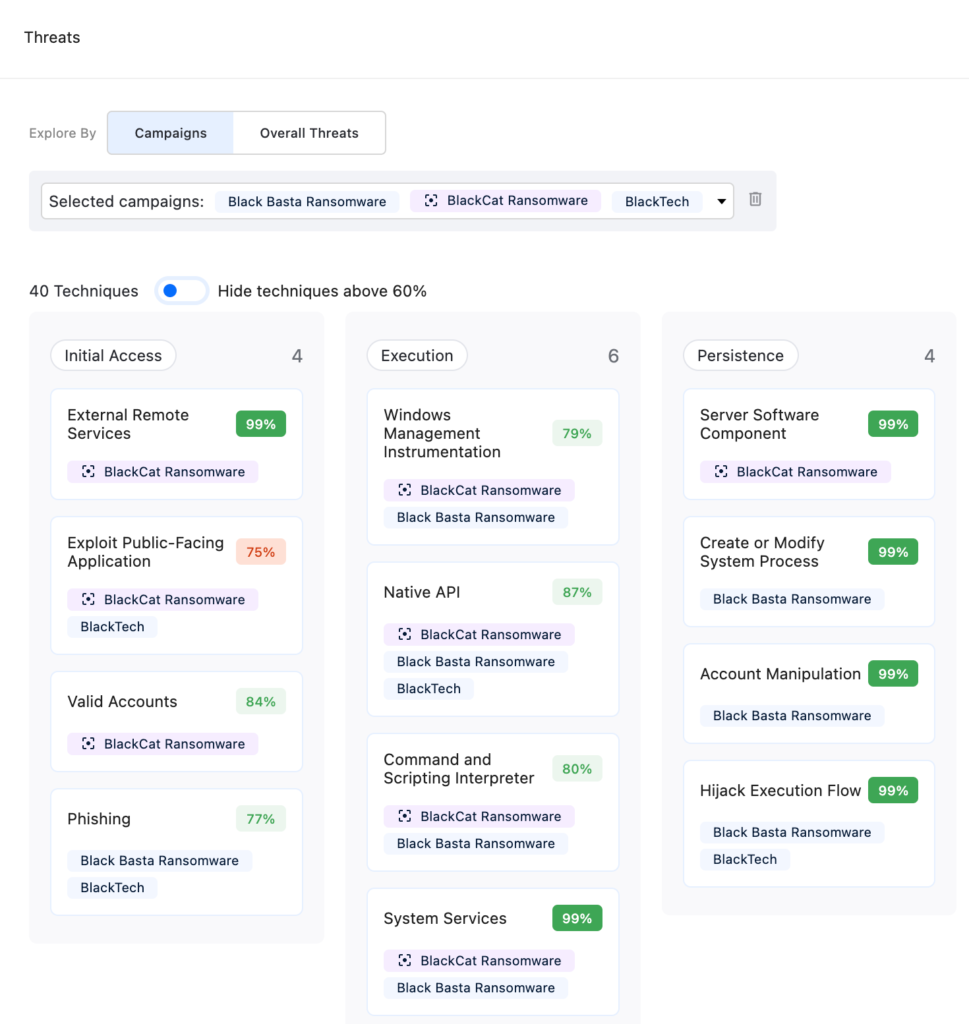
Figure 1 – Kill Chain and Technique Examples
Black Basta Ransomware: Main Characteristics and Attack Methods
BlackBasta has many variants. One of them uses a tool called Backstab, which tries to disable the endpoint detection and response (EDR) software on the endpoint to allow itself to operate more comfortably.
Nagomi associates the relevant defensive capabilities against anti-tampering and malicious driver load attempts with Impair Defenses Mitre Technique (T1562)
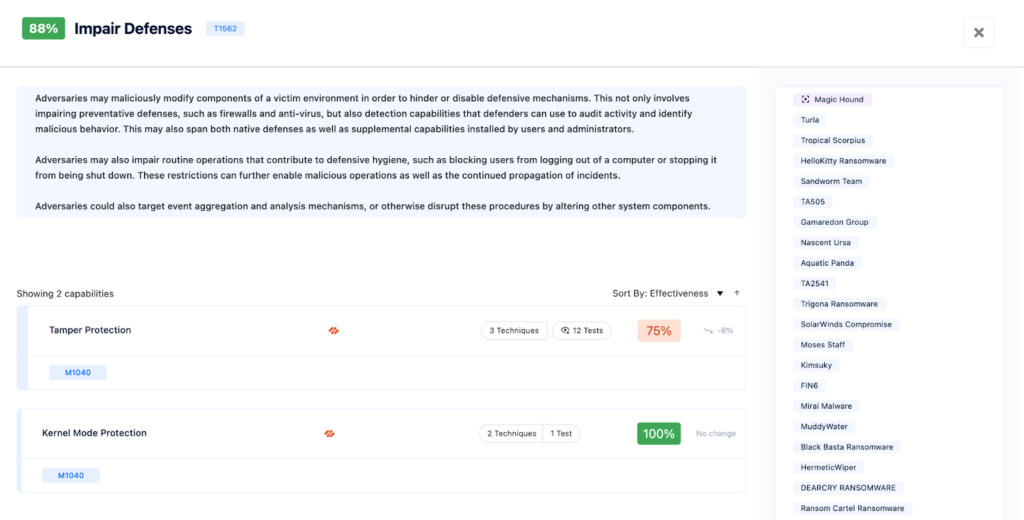
Figure 2 – Impair Defenses Technique on Nagomi Platform
By inspecting the techniques on the Nagomi Platform, customers are able to understand how secure they are against each specific technique and what defensive capabilities are available for them to adjust their posture. They can also browse those capabilities and understand more deeply what actions and features you need to cultivate to become more secure.
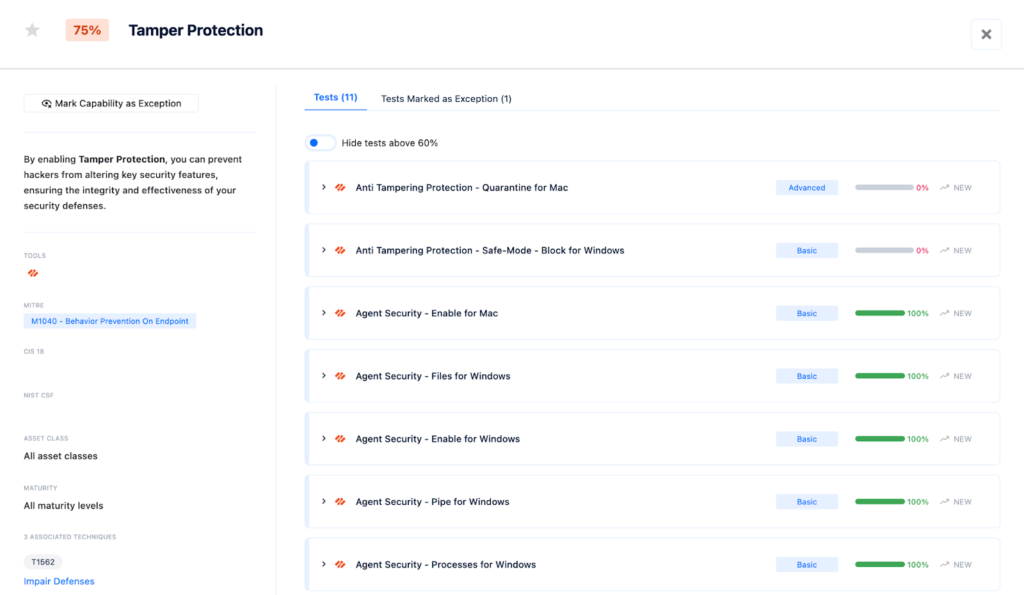
Appendix 3 – Tamper Protection
Since cyber threats such as ransomware are always evolving, security vendors are continuously making efforts to keep pace. As such, each company works hard to add new features and new security capabilities. Since new features are usually disabled by default, they are often unused despite offering protection against new threats. As an example, we can take a look at the new Anti-Tamper Protection in Palo-Alto Cortex XDR that was added on March 2023
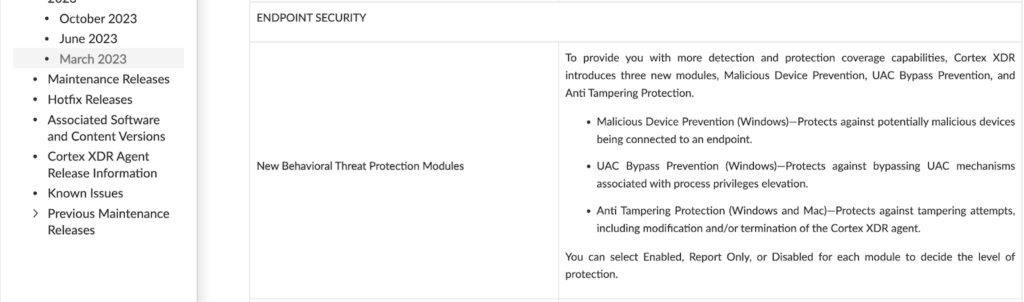
Figure 4 – Palo-Alto Cortex Releases notes
Nagomi is helping its customers monitor and be aware of all new security features that will help them mitigate the most modern and up-to-date security threats.
“Black Basta affiliates use common initial access techniques—such as phishing and exploiting known vulnerabilities,” as CISA mentioned. Again, you can inspect your relevant defenses for “Phishing” and “Exploit Public-Facing Applications” as shown in Figure 1.
As we discussed before, the final phase will be the impact. Each threat will act differently according to its main purpose. Sometimes, it will exfiltrate data, destroy a critical service, or encrypt files, as is most common for ransomware. Black Basta was designed to encrypt files on the endpoints, but it does so just after deleting volume shadow copies via the ‘vssadmin.exe’ program. Deleting shadow copies is a common technique ransomware uses to inhibit system recovery.
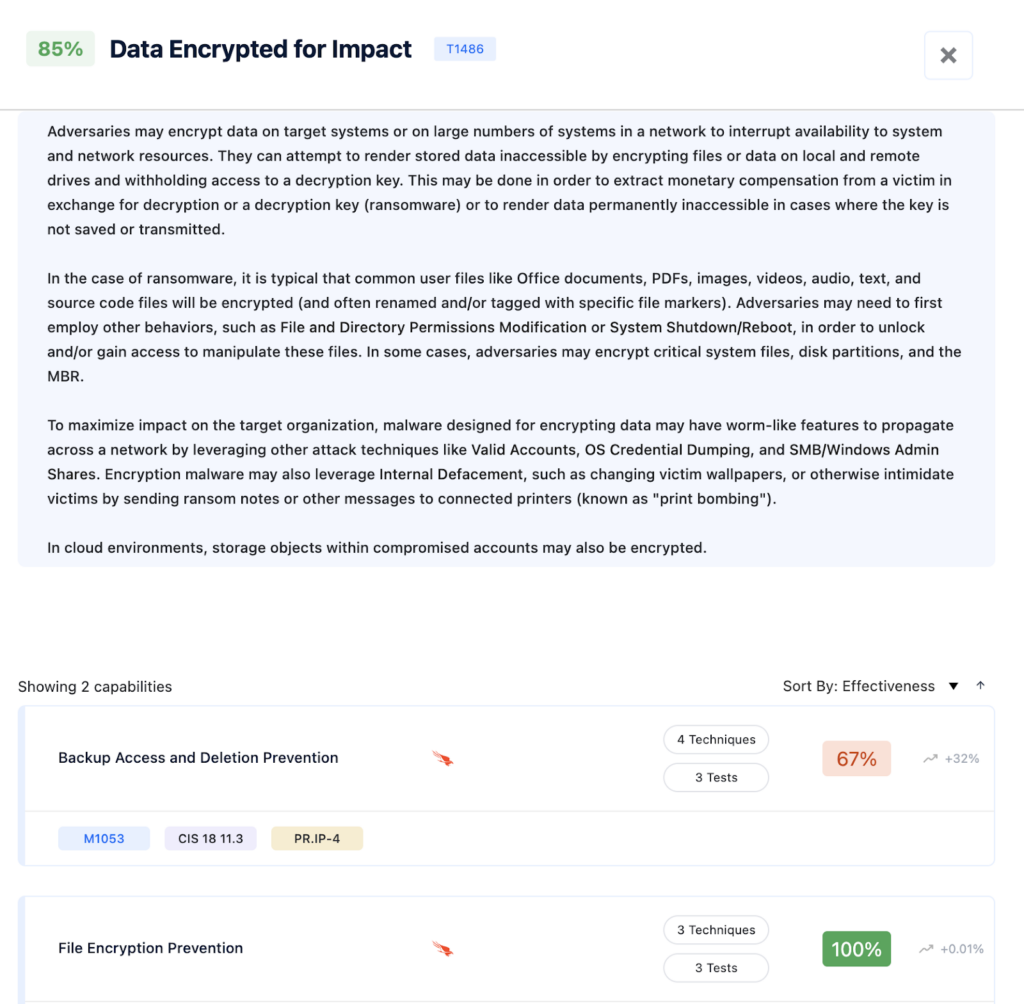
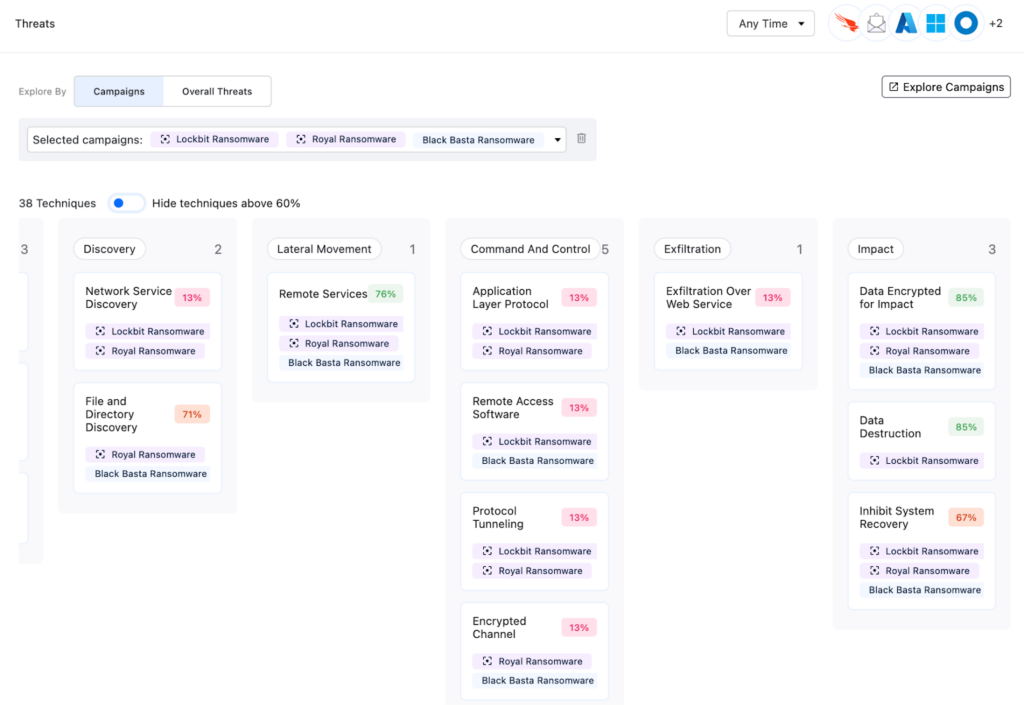
Figure 5 – Nagomi Technique Investigation Flow
In the Nagomi Platform, you can see the relevant attacking groups and the threat that is relevant for each technique (left figure) by pressing on it you can see the relevant defensive capabilities, in this case, are “Backup Access and Deletion Prevention” and “File Encryption Prevention”.
Now we’ll look at one specific tool and how to ensure the best protection against Black Basta given these defensive capabilities.
Example: How to Configure CrowdStrike Falcon to Protect Against Black Basta Ransomware
For each of them, you will be able to see your stats and measurements in order to improve your security against this threat, for example, CrowdStrike – “Volume Shadow Copy” protection. In this case, it is not enabled for most of the organization endpoints (right figure).
Enable Volume Shadow Copy in CrowdStrike Falcon
The Nagomi Proactive Defense Platform gives customers detailed instructions to remediate misconfigurations and measurements to show impact. For the Volume Shadow Copy example in CrowdStrike, Nagomi suggests navigating to your CrowdStrike options, and there on the left pane menu go to:
“Endpoint security” -> “Configure” -> “Prevention policies” -> “Windows policies” and there you should choose your relevant policies.
Inside the policies configuration, navigate to the “Behavior-Based Prevention” Section and make sure to toggle “Volume Shadow Copy—Audit” and “Volume Shadow Copy—Protect”. These configuration settings will aid in preventing malicious actions against your backups.
More than that, it is well recommended to enable other ransomware preventions such as “Backup Deletion”, “File Encryption” and “File System Access” to make sure that theCrowdstrike Agent takes action for more malicious ransom attempts.
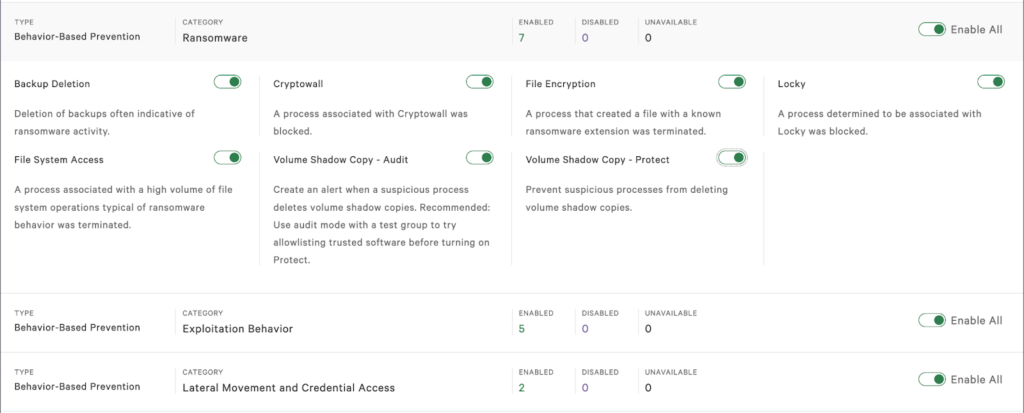
Figure 6 – CrowdStrike Ransomware Preventions
Summary
While Black Basta isn’t new, the group – like other ransomware groups – is evolving its techniques. To meet the challenge, security tools are constantly adding new features and options to protect against these new threats. At Nagomi, we will continue to highlight examples of how security teams can ensure that their existing tools are optimized to combat threats like Black Basta. To see how Nagomi can help you maximize the effectiveness of your tools, check out the Nagomi Proactive Defense Platform or book a demo.



