
Research and surveys
Enterprises Worry End Users Will be the Cause of Next Major Breach
DarkReading
Respondents in Dark Reading’s Strategic Security Survey believe that the primary cause of their organization’s next major data breach would involve social engineering, negligent users, and insecure remote workers.
The sheer volume of data breaches and cyberattacks means these incidents are now more visible than ever. Long gone are those days when affected organizations would wait till late Friday afternoons to disclose incidents in hopes of burying the news. The heightened focus is driving security professionals to rethink their enterprise security strategy and investments in tools and services.
Despite deploying a wide range of security tools to address cyber threats against their organizations, the IT and security decision makers in Dark Reading’s Strategic Security Survey don’t seem confident in the organization’s ability to withstand attacks. A high percentage believe that the processes they have implemented, such as multi-factor authentication, malware analysis capabilities and end-user security awareness training programs are effective. Sixty-three percent are confident in their ability to respond effectively to a ransomware attack.
However, 55% say their organizations are more vulnerable to data breaches than a year ago because attackers have more ways to target and break into their networks, and 58% say their organizations were more concerned about ransomware than it was a year ago. And the future doesn’t look any more optimistic: 78% say adversaries will target cloud service providers more in the coming year.
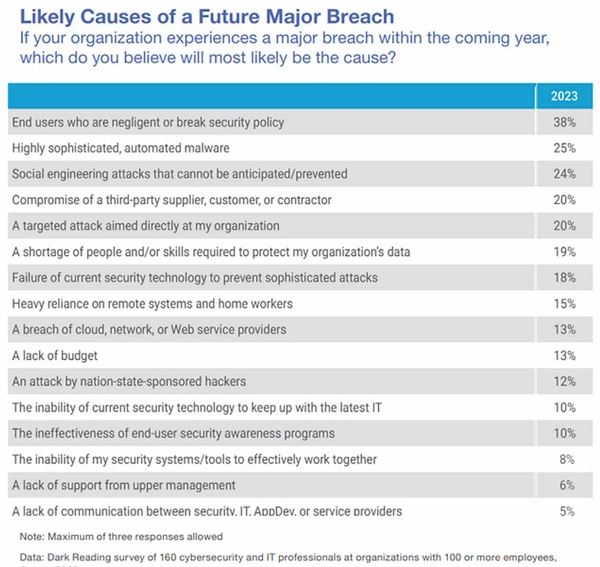
Twenty-five percent of respondents expect that if a major breach were to happen at their organization in the next 12 months, an automated malware tool will likely be the primary cause for it.
From a future breach standpoint, end users remain the biggest concern, though. Over a third (38%) believe that the primary cause of their organization’s next major data breach in the coming year would be a negligent end user or end user who breaks security policy. Almost a quarter (24%) expect it will be some kind of super elusive social engineering scam, and 15% worried about the organization’s heavy reliance on remote systems and homeworkers. And 10% felt end-user security awareness programs were ineffective.
Malware
FBI disrupts Russian Moobot botnet infecting Ubiquiti routers
by Sergiu Gatlan – BleepingComputer
The FBI took down a botnet of small office/home office (SOHO) routers used by Russia’s Main Intelligence Directorate of the General Staff (GRU) to proxy malicious traffic and to target the United States and its allies in spearphishing and credential theft attacks.
This network of hundreds of Ubiquiti Edge OS routers infected with Moobot malware was controlled by GRU Military Unit 26165, also tracked as APT28, Fancy Bear, and Sednit.
The Russian hackers’ targets include U.S. and foreign governments, military entities, and security and corporate organizations.
As part of court-authorized “Operation Dying Ember,” FBI agents remotely accessed the compromised routers and used the Moobot malware itself to delete stolen and malicious data and files.
Next, they deleted the Moobot malware and blocked remote access that would’ve otherwise allowed the Russian cyberspies to reinfect the devices.
RansomHouse gang automates VMware ESXi attacks with new MrAgent tool
By Bill Toulas – BleepingComputer
The RansomHouse ransomware operation has created a new tool named ‘MrAgent’ that automates the deployment of its data encrypter across multiple VMware ESXi hypervisors.
RansomHouse is a ransomware-as-a-service (RaaS) operation that emerged in December 2021 and is using double extortion tactics. In May 2022, the operation set up a dedicated victim extortion page on the dark web.
Although the RansomHouse gang was not as active as more infamous groups like LockBit, ALPHV/Blackcat, Play, or Clop, Trellix reports that it targeted large-sized organizations throughout last year.
MrAgent vs. ESXi
Ransomware groups target ESXi servers because they deploy and serve virtual computers that typically hold valuable data that can be used in the subsequent extortion process.
Also, ESXi servers often run critical applications and services for businesses, including databases and email servers, so the operational disruption from the ransomware attack is maximized.
Breaches and Hacks
ALPHV ransomware claims loanDepot, Prudential Financial breaches
By Sergiu Gatlan Bleeping Computer
The ALPHV/Blackcat ransomware gang has claimed responsibility for the recent network breaches of Fortune 500 company Prudential Financial and mortgage lender loanDepot.
The two companies were added to ALPHV’s dark web leak site today, with the threat actors still having to publish proof of their claims. ALPHV plans to sell the stolen data from loanDepot’s network and release Prudential’s data for free after failed negotiations.
The company said it would notify those impacted by the data breach and provide them with free credit monitoring and identity protection services.
loanDepot is one of the largest U.S. nonbank retail mortgage lenders, with roughly 6,000 employees and over $140 billion in serviced loans.
On Tuesday, Prudential Financial also revealed that a suspected cybercrime group breached its network on February 4 and stole employee and contractor data.
US offers up to $15 million for tips on ALPHV ransomware gang
By Sergiu Gatlan Bleeping Computer
The U.S. State Department is offering rewards of up to $10 million for information that could lead to the identification or location of ALPHV/Blackcat ransomware gang leaders.
An additional $5 million bounty is also available for tips on individuals trying to take part in ALPHV ransomware attacks, likely to discourage affiliates and initial access brokers.
The FBI linked this ransomware gang to over 60 breaches worldwide during its first four months of activity between November 2021 and March 2022.
ALPHV has also raked in at least $300 million in ransom payments from more than 1,000 victims until September 2023, according to the FBI.
“The U.S. Department of State is offering a reward of up to $10,000,000 for information leading to the identification or location of any individual(s) who hold a key leadership position in the Transnational Organized Crime group behind the ALPHV/Blackcat ransomware variant,” the State Department said.
DOD notifying more than 26,000 people who may be impacted by a year-old data breach
By Brandi Vincent – DefenseScoop
The Pentagon is in the process of alerting more than 26,000 current and former employees, job applicants and partners that their sensitive personal information may have been exposed online in a “data breach incident” that was first detected in early 2023.
DefenseScoop viewed a notice — dated Feb. 1, 2024 and sent by the Defense Intelligence Agency to a longtime Defense Department official — encouraging them to sign up for government-provided identity theft protection services as a result of the exposure.
“This letter is to notify you of a data breach incident that may have resulted in a breach of your personally identifiable information (PII). During the period of February 3, 2023 through February 20, 2023, numerous email messages were inadvertently exposed to the Internet by a [DOD] service provider. Unfortunately, some of these email messages contained PII associated with individuals employed by or supporting the DOD, or individuals seeking employment with the DOD. While there is no evidence to suggest that your PII was misused, the department is notifying those individuals whose PII may have been breached as a result of this unfortunate situation,” the document states.
Broadly, PII refers to any data that can be used to distinguish or trace someone’s identity — like addresses, Social Security numbers, credit card info and biometric records.
Volt Typhoon targeted emergency management services, per report
by Christian Vasquez – Cyberscoop
Volt Typhoon, the China-sponsored hacking group that has been the focus of grim warnings from U.S. security agencies, has been targeting satellite and emergency management services in addition to electric utilities, according to a new report.
The industrial cybersecurity firm Dragos’s Tuesday report outlines how the notorious hacking group is positioning themselves to have disruptive or destructive impacts on critical infrastructure in the U.S.
Last month, Dragos observed Volt Typhoon — which Dragos tracks as Voltzite — target a large U.S. city’s emergency management services geographic information system, which is used for emergency dispatch operations like law enforcement or ambulance services and is used to assist in disaster recovery efforts. And in June 2023, Volt Typhoon infiltrated a U.S. emergency management organization, Dragos found. The firm has seen Volt Typhoon target electric utilities, satellite and telecommunications services, and the defense industrial base.
The targeting of disaster recovery services underscores the recent warnings from security officials about Volt Typhoon’s strategic targeting against U.S. infrastructure, particularly in the event of a conflict with China over an invasion of Taiwan — although it is not clear if emergency services targeting is for information gathering or to pre-position for additional disruption.
Atlassian vulnerability at fault in GAO breach
A breach of the Government Accountability Office that resulted in the compromise of data associated with thousands of current and former employees of the agency was carried out using a notorious vulnerability in an Atlassian workforce collaboration tool.
The breach of GAO, a nonpartisan entity that carries out investigations into taxpayer spending for Congress and federal agencies, occurred via one of its contractors, CGI Federal. The contractor notified GAO on Jan. 17 “of a data breach impacting approximately 6,600 people, primarily current and former GAO employees from 2007 to 2017, as well as some companies doing business with GAO,” agency spokesperson Chuck Young told CyberScoop in an email.
A spokesperson for CGI Federal, Mercedes Marx, told CyberScoop Tuesday that it was the victim of a breach of a third-party tool, the Atlassian Confluence workforce collaboration tool.
The Cybersecurity and Infrastructure Security Agency, FBI and the Multi-State Information Sharing and Analysis Center (MS-ISAC) issued an advisory in October detailing the active exploitation of a vulnerability affecting certain versions of Atlassian Confluence Data Center and Server. Malicious hackers exploited the vulnerability to “obtain access to victim systems and continue active exploitation post-patch,” the advisory warned. Researchers quickly warned of “mass exploitation” of the vulnerability.
Prudential Financial Discloses Data Breach
By Ionut Arghire – SecurityWeek
Prudential Financial says administrative and user data was compromised in a cyberattack earlier this month.
Insurance giant Prudential Financial this week informed the US Securities and Exchange Commission that it fell victim to a data breach earlier this month.
The incident, the company said in a Form 8-K filing, was identified on February 5, one day after a threat actor gained unauthorized access to some of its systems.
“With assistance from external cybersecurity experts, we immediately activated our cybersecurity incident response process to investigate, contain, and remediate the incident,” the company said.
Prudential Financial said that the attackers were able to access company administrative and user data stored on the compromised systems, as well as user accounts associated with employees and contractors.
What the company did not say was how many of its roughly 40,000 employees worldwide might have been impacted by the incident.
However, the company noted that a cybercrime group was likely responsible for the attack. This could mean a ransomware group is behind the intrusion.
“We continue to investigate the extent of the incident, including whether the threat actor accessed any additional information or systems, to determine the impact of the incident,” the company told SEC.
Prudential Financial also said that it has not found evidence of customer or client data theft, and that the incident was reported to law enforcement and regulatory authorities.
Cybersecurity in the future!
Cybercriminals are stealing iOS users’ face scans to break into mobile banking accounts
by Connor Jones – TheRegister
Cybercriminals are targeting iOS users with malware that steals face scans from the users of Apple devices to break into and pilfer money from bank accounts – thought to be a world first.
A Chinese-speaking cybercrime group, dubbed GoldFactory by Group-IB’s researchers, started distributing trojanized smartphone apps in June 2023, however, the latest GoldPickaxe version has been around since October.
GoldPickaxe and GoldPickaxe.iOS target Android and iOS respectively, tricking users into performing biometric verification checks that are ultimately used to bypass the same checks employed by legitimate banking apps in Vietnam and Thailand – the geographic focus of these ongoing attacks.
The iOS version is believed only to be targeting users in Thailand, masquerading as the Thai government’s official digital pensions app. That said, some think it has also made its way to Vietnam. This is because very similar attacks, which led to the theft of tens of thousands of dollars, were reported in the region earlier this month.
“It is of note that GoldPickaxe.iOS is the first iOS Trojan observed by Group-IB that combines the following functionalities: collecting victims’ biometric data, ID documents, intercepting SMS, and proxying traffic through the victims’ devices,” the researchers said.
“Its Android sibling has even more functionalities than its iOS counterpart, due to more restrictions and the closed nature of iOS.”
OpenAI’s Spectacular Video Tool Is Shrouded in Mystery
By Parmy Olson – Bloomberg
Sam Altman is being secretive in all the wrong places about AI that can be used to spread misinformation.
Every new OpenAI announcement sparks some measure of awe and terror. Late on Thursday, the maker of ChatGPT dropped its latest new gizmo, a text-to-video model called Sora that can create up to a minute of high-quality video. Cue a flood of remarkable AI clips going viral on social media, while stock video producers, filmmakers, actors and some startup founders likely fretted about their livelihoods.
AI video-generation has been around for more than a year, but Sora’s examples, including a high-definition clip of puppies shaking their fur in the snow and a sleepy woman being woken up by her cat, look more realistic than previous efforts. The glitches are harder to spot and the humans look more human.


