Nagomi connects your tools and workflows so teams can prioritize the right work, reduce exposure, and report measurable improvement.
Unified Attack Surface Visibility

Automate Asset Inventory and Coverage Gap Analysis
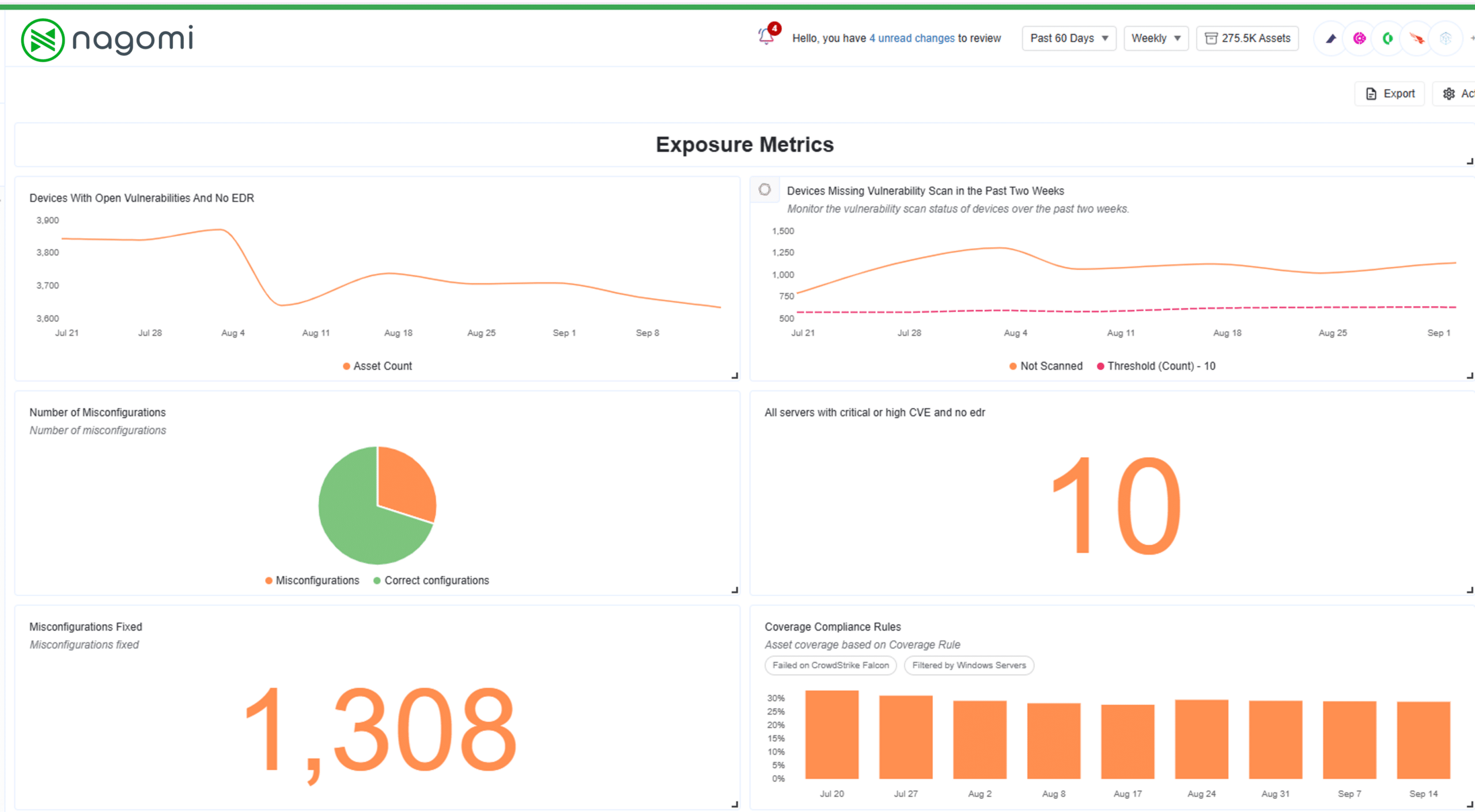
Unify data from your entire security stack into one clear view, creating an accurate asset inventory to continuously assess and evaluate the effectiveness of your defenses against evolving threats.
Threat Intelligence Activation
Operationalize Threat Intelligence
Align security data, tools, and processes to turn raw threat intelligence into comprehensive insights and prescriptive remediation plans.
Exposure Management

Prioritize Exposures with Context
Fix exposures based on asset importance, control effectiveness, vulnerability impact, and live threat data – all relevant to your unique environment.
Subsidiary and M&A Risk Oversight

Unify and Oversee Risk Across Subsidiaries & M&A
Evaluate security risks across acquisitions, subsidiaries, and business units to ensure consistency and compliance.
Dynamic Reporting

Dynamic Risk & Performance Reporting
Transform complex security data into clear, concise reports that translate across the business. Automate the process to save time, highlight key risks, and showcase the true value of your security efforts.
A clear path from discovery to remediation.
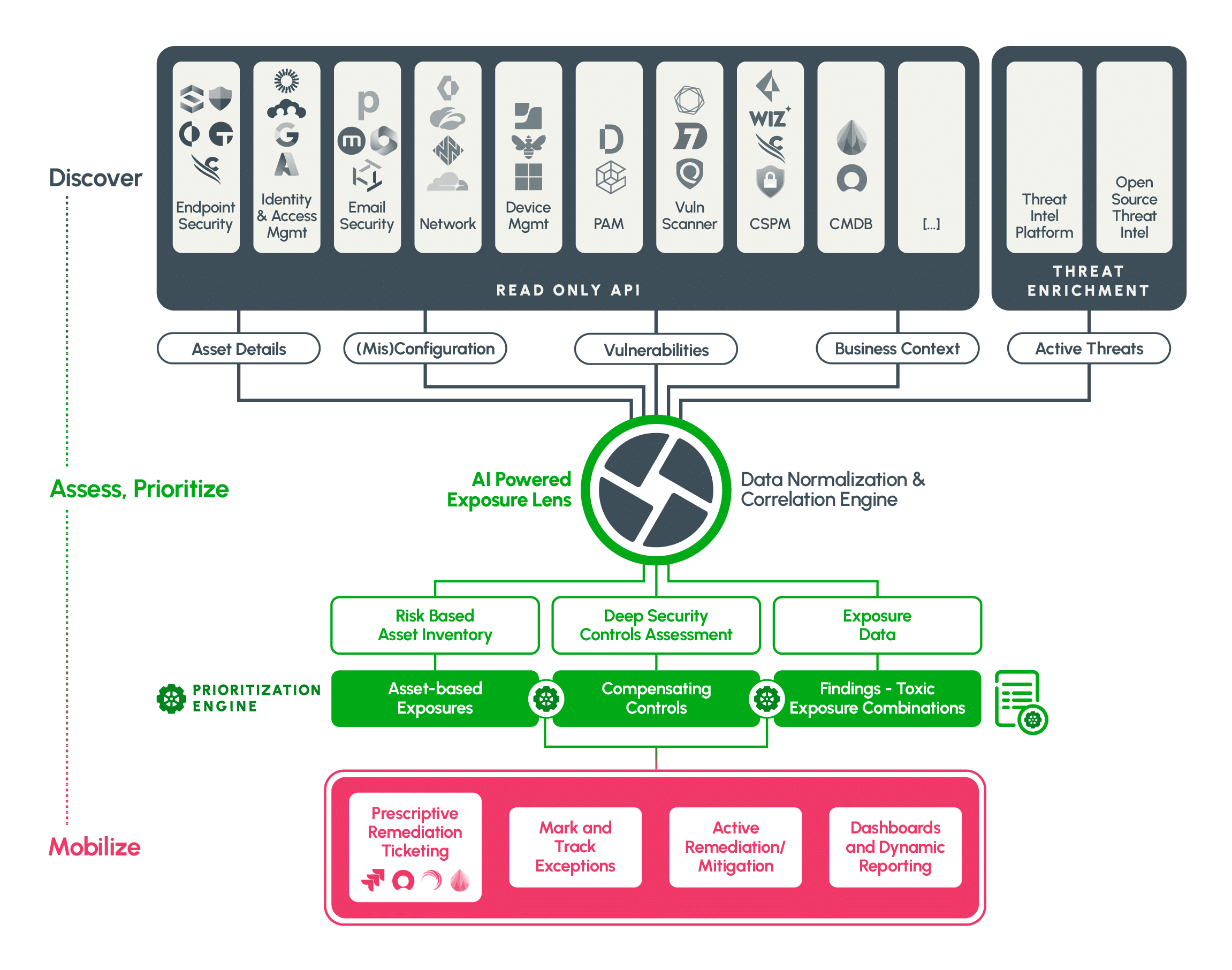
Unify inputs, apply context, and drive execution across your program with a Continuous Threat Exposure Management (CTEM) approach.
INTRODUCING EXPOSURE LENS
Seeing exposure requires context.
Exposure Lens powers a CTEM-driven approach by turning raw findings into validated, prioritized exposure scenarios across multiple sources.
70% faster threat alignment with live TTP correlation.
Turn threat intel into action by matching active attacker behaviors to your environment, so you can preempt exploitation before it happens.
Cut vulnerability noise by 90%
Unpatched CVEs, flawed dependencies…Exposure Lens shows which are actively exploited and whether your controls compensate, so you fix what matters first.
Validate control performance across 100% of assets
Detect configuration drift, blind spots, and coverage gaps before attackers do, ensuring your defenses perform exactly as designed.
Prioritize the 10% of exposures driving 90% of risk
Keep a live inventory of what you have, what’s enforced and where controls fall short. Focus effort on exposures that put the business at real risk, not the longest CVE list.
100% confident
With unified context and automation, Exposure Lens helps teams act decisively, measure impact, and regain control over complexity.
Your security
stack in one place.
From guesswork to confidence
Nagomi automates the process of proving your security is actually working. Our platform unifies data across your assets, defenses, and threats to clearly illustrate your security program is both efficient and effective to key stakeholders.
25%
Decrease in overall threat exposure.
Fortune 500 company fully transitioned their board exposure and utilization reporting to be continuous and live on Nagomi.
350+ hours a year
Saved meeting with vendors.
300+ hours
Of auditor time saved per person.
Large Australian mining company found 1.3M misconfigurations, fixing 332K in less than 1 month.
$250,000
Saved annually for a mid-sized enterprise by eliminating redundant tools.
Increased relevance of defenses through real-time mappings.
Enabled more strategic resource allocation, improving planning efficiency by 30%.
Reduced time-to-remediation by 45%.