back to blog
BLOG
When Qilin Ransomware Strikes Your Peers, Are You Safe? Day in the Life of a Nagomi Customer

Background
According to the 2024 Ransomware Landscape report released by Rapid7, the average ransom payment in Q32024 was nearly $500k, with the total number of active ransomware groups numbering 75. Each of these groups represents an advanced threat that today’s enterprises have to protect and prepare against to ensure that they don’t fall victim to these statistics. According to the same report, the following were the most prolific ransomware groups of 2024 (based on the number of posts on leak sites):
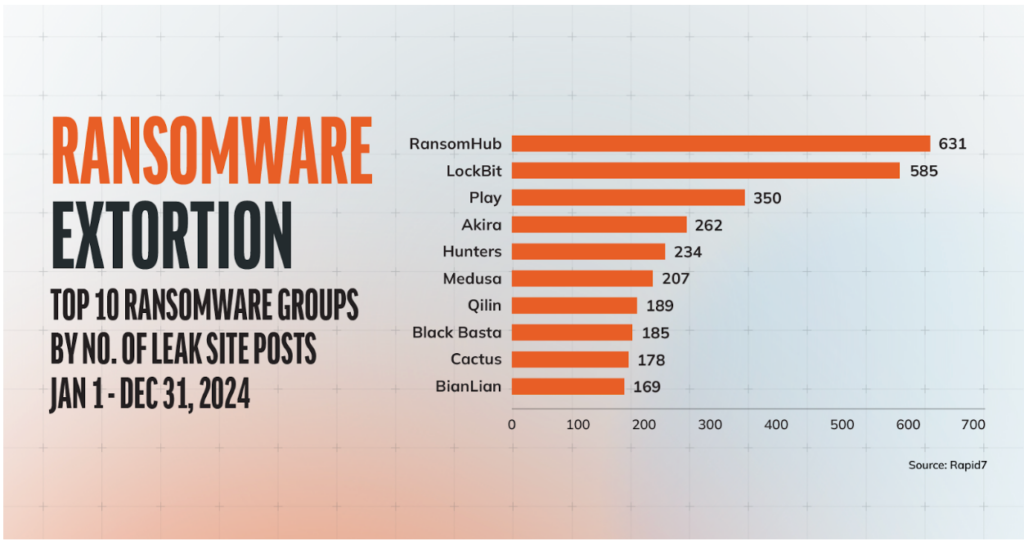
One of the groups listed in the Top-10 above is the Qilin ransomware group, which is the focus of today’s blog. We highlight how one of our customers in the media and publishing industry leveraged the Nagomi Proactive Defense Platform to not only ensure that their organization was protected against the Qilin ransomware threat, but also communicate the effectiveness of their security program against it to their board.
Who is the Qilin Ransomware Group, and why is the focus on them
The Qilin Ransomware group (also known as Agenda) is a Russian ransomware-as-a-service operation that has been previously linked to multiple attacks. The Qilin group typically leverages spear phishing to gain initial access to victim networks in addition to leveraging any exposed vulnerable applications, including the Remote Desktop Protocol (RDP). The Qilin ransomware group leverages double extortion techniques wherein they not only encrypt victim data, but they also steal it before encrypting it. This strategy enables them to intimidate victims by threatening to post their data on the dark web if they fail to make the required ransom payments.
The same Qilin ransomware group was recently involved in an attack on Lee Enterprises, which is an American media company owning 350 weekly and specialty publications across 25 U.S. states. This attack that unfolded in February 2025 affected nearly 75 publications, causing operational disturbances. Initial analysis of this attack revealed that threat actors were able to access their network, encrypt critical applications, and exfiltrate files.
In a post shared on the Dark Web, they highlighted that they were in possession of nearly 350 Gb of files from Lee Enterprises. They published samples of stolen data on March 5th, including PII data like passport and driver’s license scans—indicating that Lee Enterprises had either refused their ransom demand or ransom negotiations had failed.
Nagomi’s Coverage for the Qilin Campaign
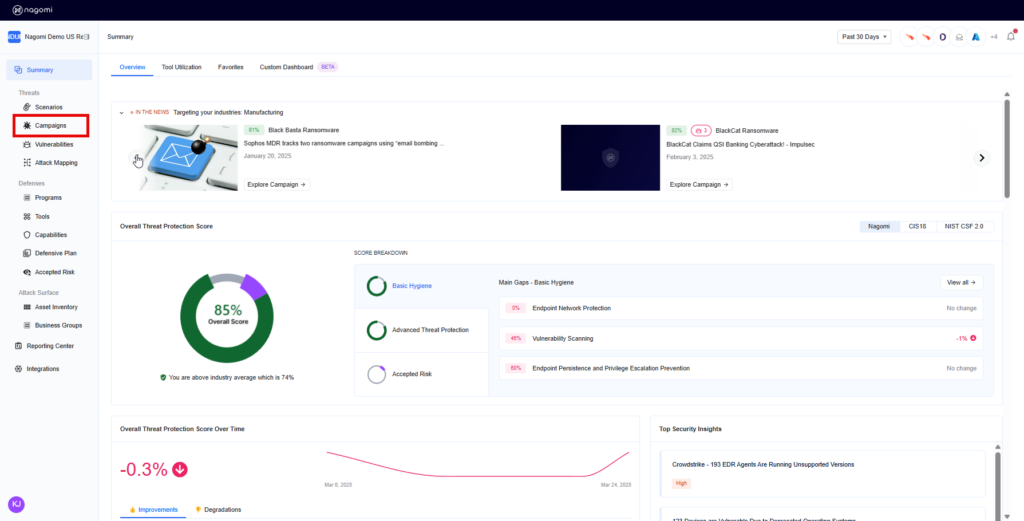
As this cyberattack garnered national and international attention, it became clear that Qilin threat actors could potentially target other organizations in the media space. Being in the same vertical as Lee Enterprises, the customer’s board of directors were concerned about the potential impact of this ransomware threat on their organization and wanted the CISO to highlight their readiness to face this threat. The CISO and their SecOps team turned to the Nagomi platform to understand how their defenses stacked up against the Qilin ransomware. The Nagomi platform has been designed to not only help the day-to-day technical SecOps user identify their policy/configuration gaps and measure the performance of their deployed security controls but also for a non-technical stakeholder like the CISO to communicate security program performance effectively. Let’s see how easy it would be to determine organizational preparedness against such advanced threat campaigns.
Step 1: Log into your Nagomi Platform and click “Campaigns” from the left menu
Step 2: Search for “Qilin” in the search menu to locate the Qilin Ransomware Campaign and click “Explore More”

Step 3: This campaign overview page will provide teams with a high-level overview of your organization’s preparedness against the Qilin Ransomware. This page includes the following information:
- Top Susceptible Techniques— Highlights the techniques your organization is most susceptible to based on analyzing the attack campaign, utilization of your deployed security tools, and your overall attack surface.
- MITRE ATT&CK Mapping— Highlights how prepared your organization is against the various MITRE tactics being used in the chosen threat campaign.
- Known Exploitable Vulnerabilities—Highlights if any CISA KEV’s are being leveraged as part of the attack campaign.
- Defensive Plans—Recommended remediation steps that can be taken to improve organizational security posture against Qilin ransomware based on the gaps identified by the Nagomi platform
- All Defensive Capabilities— Highlights all your existing deployed defensive controls with their identified coverage gaps and how they would potentially impact your security posture.
- Missing Capabilities— Highlights those defensive capabilities (security controls) that your organization is currently missing and needs to add to ensure comprehensive protection against the Qilin ransomware threat.
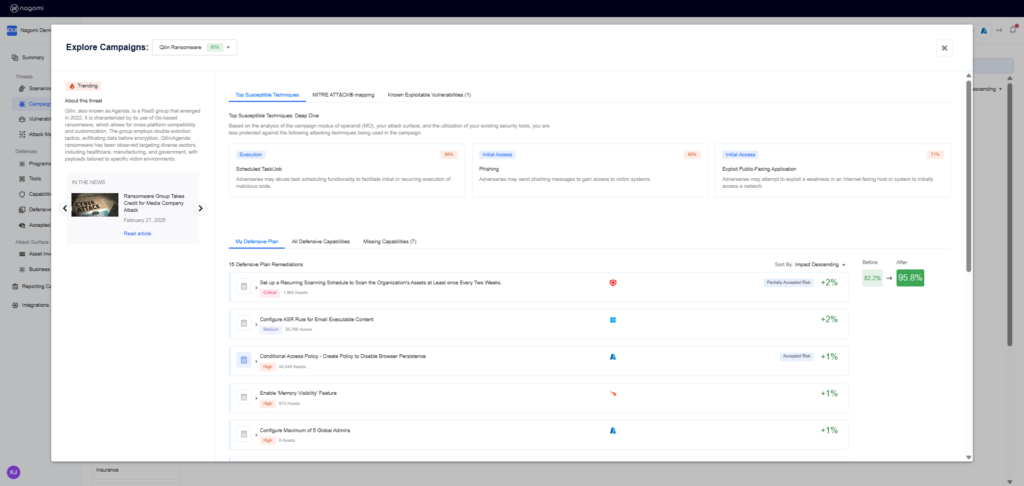
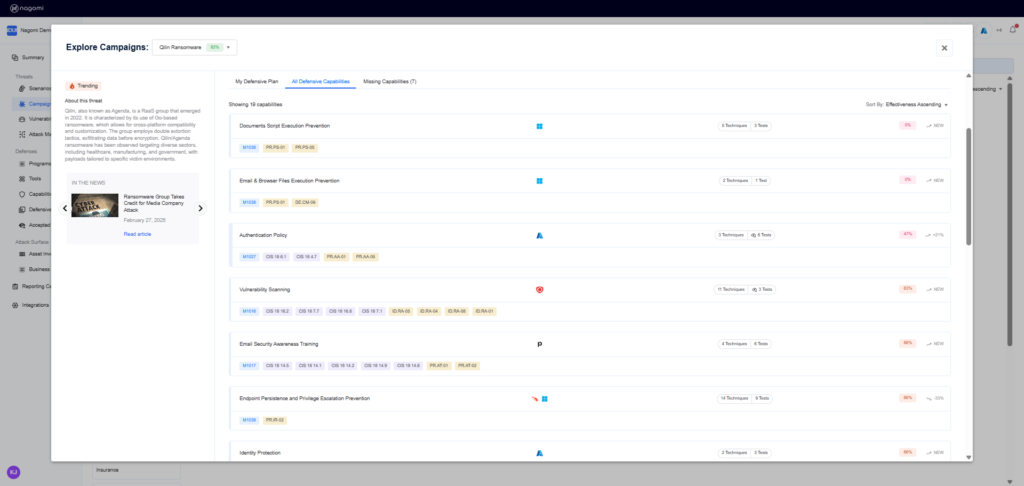
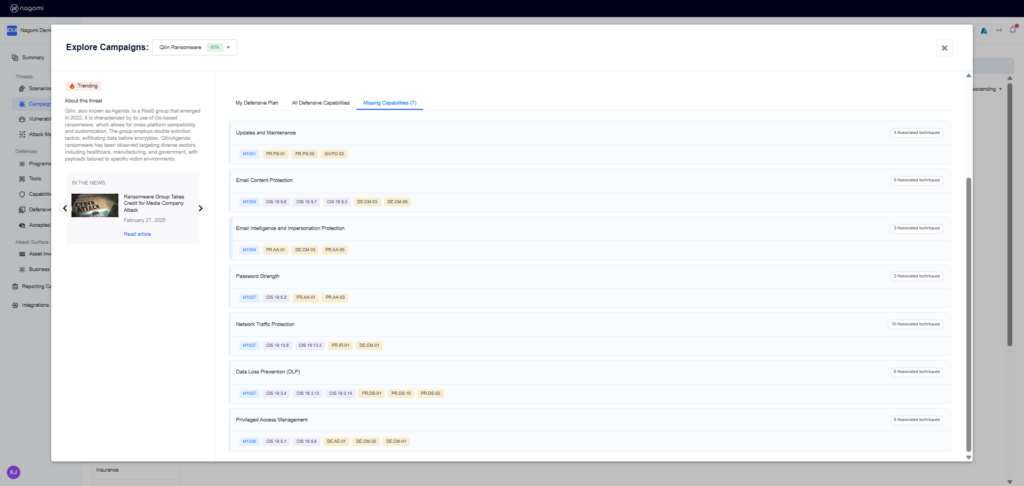
Step 4: Leverage the top-15 remediation recommendations provided by Nagomi to quickly begin the process of fixing identified security gaps
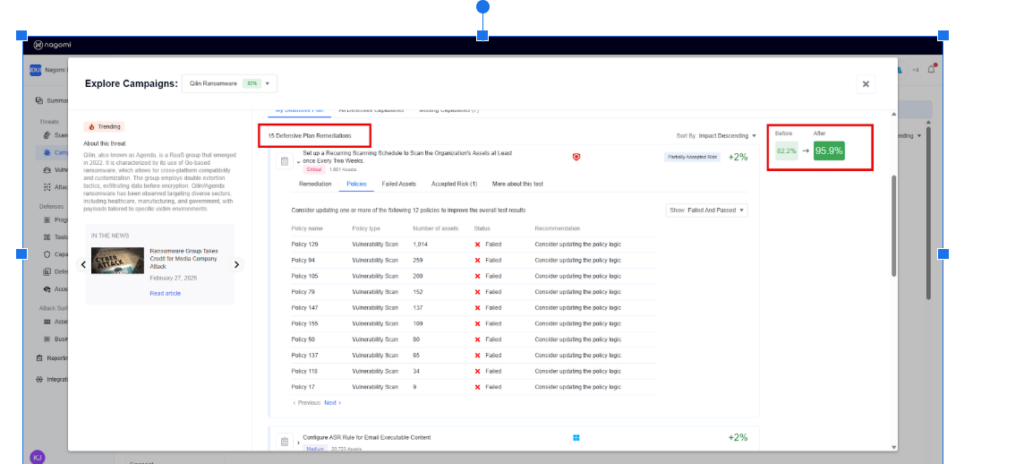
Nagomi’s remediation recommendations are intended to provide incident responders with actionable steps that can be taken to reduce their mean-time-to-remediate (MTTR).
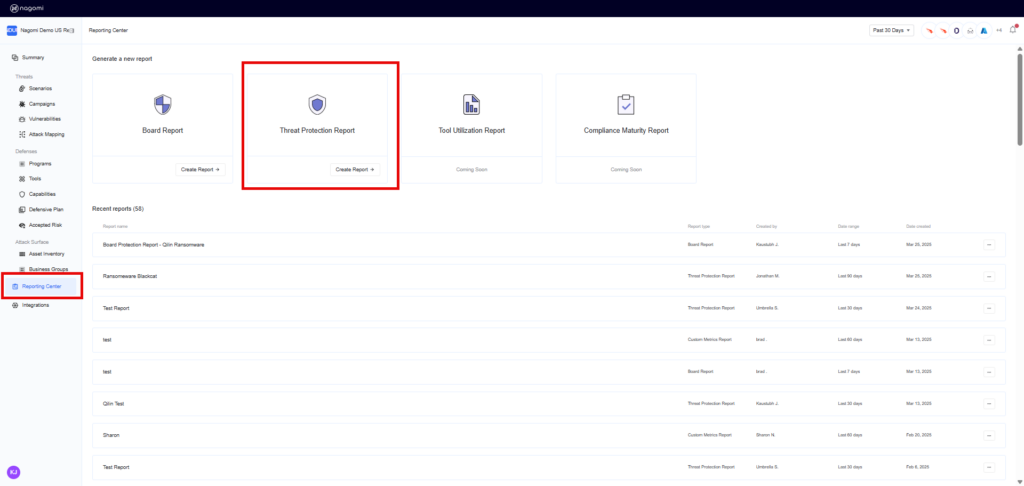
While identifying and closing gaps is a crucial aspect, it’s equally crucial to effectively communicate organizational preparedness to non-technical stakeholders, such as the board of directors. The Nagomi platform simplifies this process by providing SecOps teams with customizable reports and dashboards that can be quickly created to report program health. In this case, to specifically report organizational readiness against the Qilin campaign, simply click on the “Reporting Center” item from the left-hand menu and select the “Threat Protection Report.”

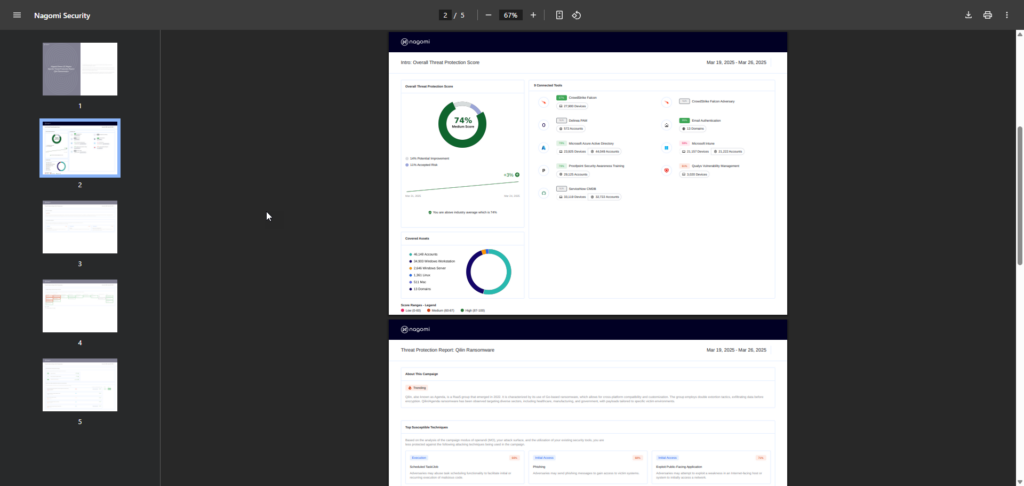
The final report is generated in an easy-to-understand visual PDF format that can be used to communicate organizational preparedness against this ransomware campaign. The above document is the same report that our customer CISO leveraged to highlight their enterprise’s readiness against the Qilin ransomware to their board of directors.

Conclusion
The Nagomi Platform is more than a tool—it’s your proactive defense platform. By helping you evaluate and continuously improve your program’s performance, it empowers teams to move beyond reactive cycles into a future of confidence and control. Whether it’s unifying the view of your attack surface, reducing security debt, or translating security metrics for stakeholders, Nagomi reduces threat exposure while transforming cybersecurity from a technical cost center into a strategic business enabler.


