In a joint June 2025 advisory, CISA, the FBI, and the Australian Cyber Security Center (ACSC) confirmed a staggering escalation: Play (aka Playcrypt) ransomware has now breached 900+ organizations across critical sectors. That’s nearly 3x the number of confirmed victims just six months ago, and this count is still rising.
Play was one of the most prolific ransomware actors of 2024, and their operations aren’t slowing down. Their targets include public infrastructure, government entities, education, healthcare, and enterprise networks across North and South America, Europe, and beyond. This is no longer just another ransomware gang. It’s a campaign-level threat that requires campaign-level readiness.
Why Play (Playcrypt) Ransomware Group Should be Proactively Monitored
Play ransomware operators are tactical, evasive, and methodical. They use double extortion (encrypting + exfiltrating sensitive data), target known vulnerabilities (like Fortinet, Microsoft Exchange, and RMMs), and adapt payloads on the fly.
They evade antivirus, disable defenses, and hide their movements with customized, recompiled binaries, making signature-based detection nearly useless. To be more specific, their ransom notes direct victims to contact the Play ransomware group at an email address ending in @gmx[.]de or @web[.]de. Ransom payments are paid in cryptocurrency to wallet addresses provided by Play actors. If a victim refuses to pay the ransom demand, the ransomware actors threaten to publish exfiltrated data to their leak site on the Tor network ([.]onion URL).
Technical Drill-down
Based on the information available in the advisory, here is a step-by-step breakdown of how the Play ransomware threat actors executed their attacks:
- Initial Access—The group gains its initial access to victim networks by leveraging stolen credentials to valid accounts purchased on the dark web and through exploitation of vulnerabilities in public-facing applications, specifically:
- FortiOS: CVE-2018-13379 and CVE-2020-12812
- Microsoft Exchange: CVE-2022-41040 and CVE-2022-41082
- SimpleHelp RMM: CVE-2024-57727
- Discovery and Defense Evasion—Post initial access, threat actors leverage tools like AdFind to run Active Directory queries and Grixba, an infostealer, to enumerate network information and scan for deployed AV systems. Several tools, including GMER, IOBit, etc., are used to disable AV software and remove log files. PowerShell scripts have also been leveraged to target Microsoft Defender.
- Lateral Movement and Payload Execution—C2 applications like Cobalt Strike and SystemBC and tools like PSExec are then used to assist with lateral movement and file execution. Stolen or unsecured credentials are then leveraged to gain domain admin access, and malicious executables are distributed via Group Policy Objects.
- Exfiltration and Encryption—The compromised data is split into segments and compressed via WinRAR to be exported outside the victim network. Once successfully exfiltrated, the original files on the network are then encrypted, and a ransom note is placed in C:/Users/Public/Music.
- Ransom Demand—The ransom note directs victims to pay the ransom via cryptocurrency to wallet addresses provided by the threat actors. If the victim declines to pay the ransom, the threat actors publish the stolen data on the dark web.
It is important to note that the Play ransomware binary is recompiled for each individual attack, resulting in unique hashes for each deployment— essentially making the detection extremely complicated. Put simply: Play doesn’t rely on novelty. It relies on the fact that most organizations haven’t fully secured what they already have.
Test Your Readiness Against the Play Ransomware Campaign with the Nagomi Platform
How secure are we against Play (Playcrypt) ransomware? Trying to answer this critical question is easy if you are using the Nagomi Proactive Defense Platform. Our platform has been built to provide continuous visibility into your security posture and identify vulnerabilities that could be potentially exploited in an attack involving the Play ransomware group.
Step 1: Log into your Nagomi Platform and click “Campaigns” from the left menu. Search for “Play ransomware” in the search menu to locate the campaign. Then, click “Explore More”
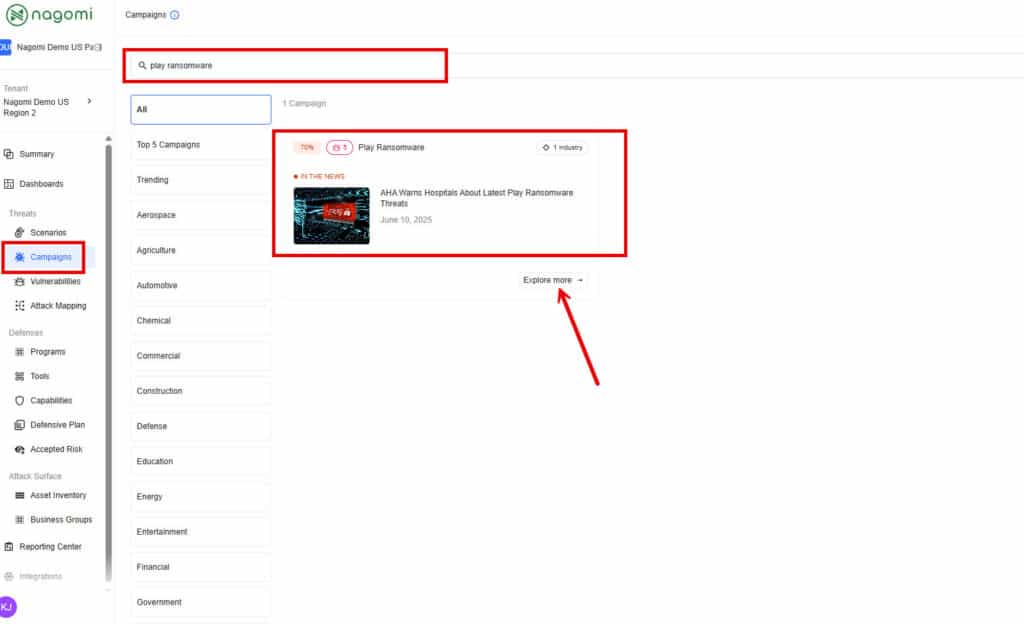
Step 2 – This campaign overview page provides teams with a high-level overview of your organization’s preparedness against Play ransomware. This page includes the following information:
- Top Susceptible Techniques: Highlights the techniques your organization is most susceptible to based on analyzing the attack campaign, utilization of your deployed security tools, and your overall attack surface.
- MITRE ATT&CK Mapping: Highlights how prepared your organization is against the various MITRE tactics being used in the chosen threat campaign.
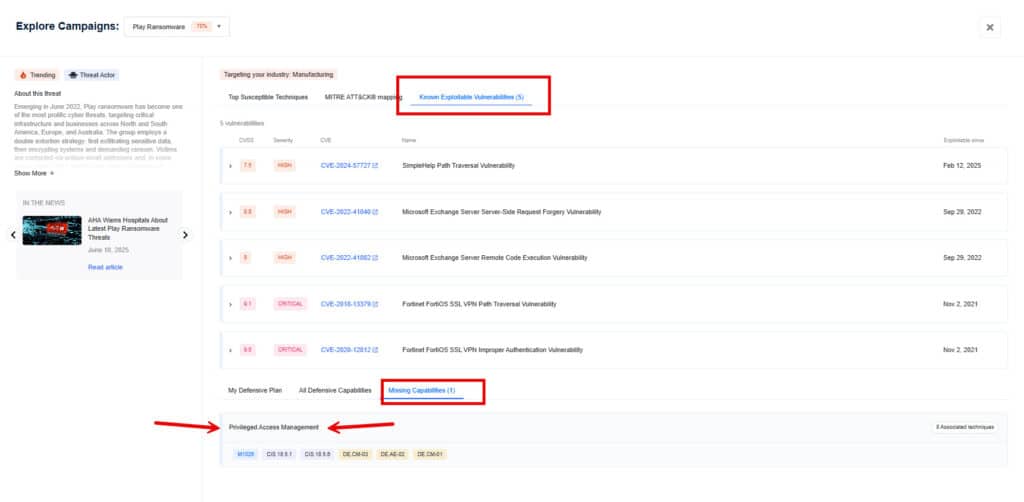
- Known Exploitable Vulnerabilities: Highlights if any CISA KEV’s are being leveraged as part of the attack campaign.
- Defensive Plans: Recommended remediation steps that can be taken to improve organizational security posture against Play ransomware based on the gaps identified by the Nagomi platform.
- All Defensive Capabilities: Highlights all your existing deployed defensive controls with their identified coverage gaps and how they would potentially impact your security posture.
- Missing Capabilities: Highlights those defensive capabilities (security controls) that your organization is currently missing and needs to add to ensure comprehensive protection against the Play ransomware threat.
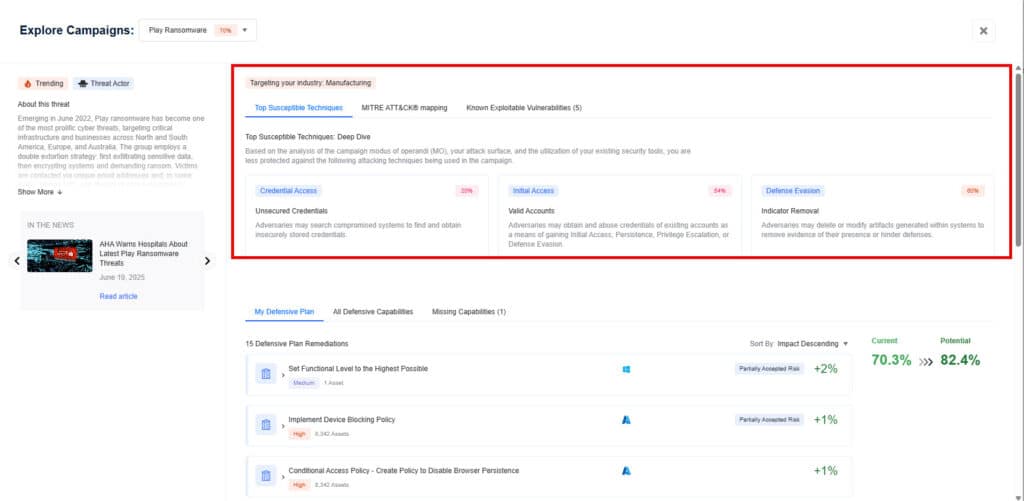
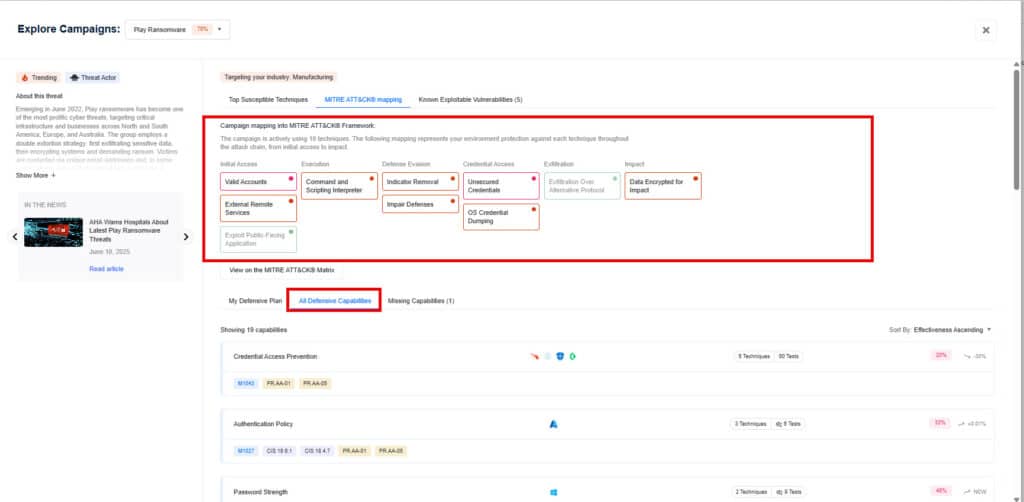
Step 3: Leverage the top 15 remediation recommendations provided by Nagomi to quickly begin the process of fixing identified security gaps.
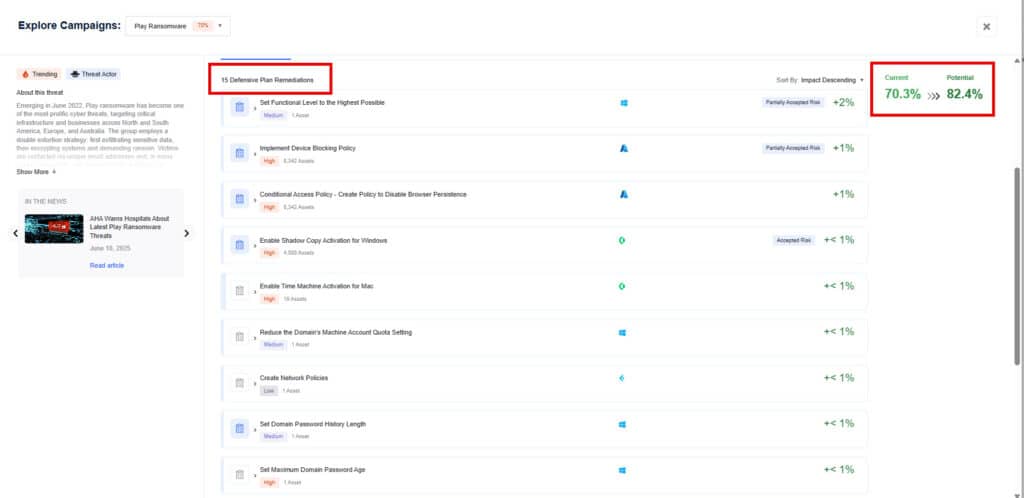
Nagomi’s remediation recommendations are intended to provide incident responders with results-driven steps that can be taken to reduce their mean-time-to-remediate (MTTR).
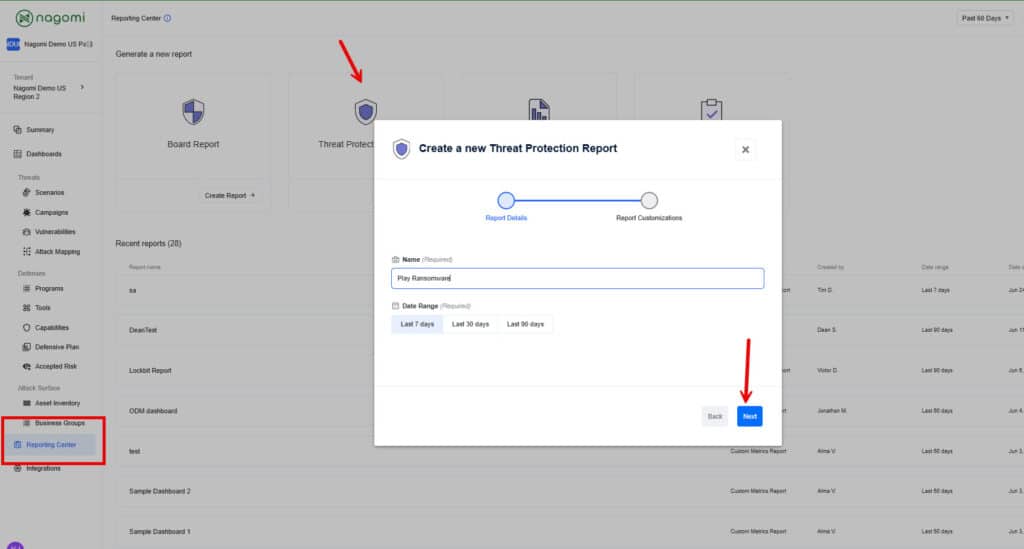
While identifying and closing gaps is a crucial aspect, it’s equally important to effectively communicate organizational preparedness to non-technical stakeholders, such as the board. The Nagomi platform simplifies this process by providing SecOps teams with customizable reports and dashboards that can be quickly generated to report program health. In this case, to specifically report organizational readiness against Play ransomware, simply click on the “Reporting Center” item from the left-hand menu and select the “Threat Protection Report.”
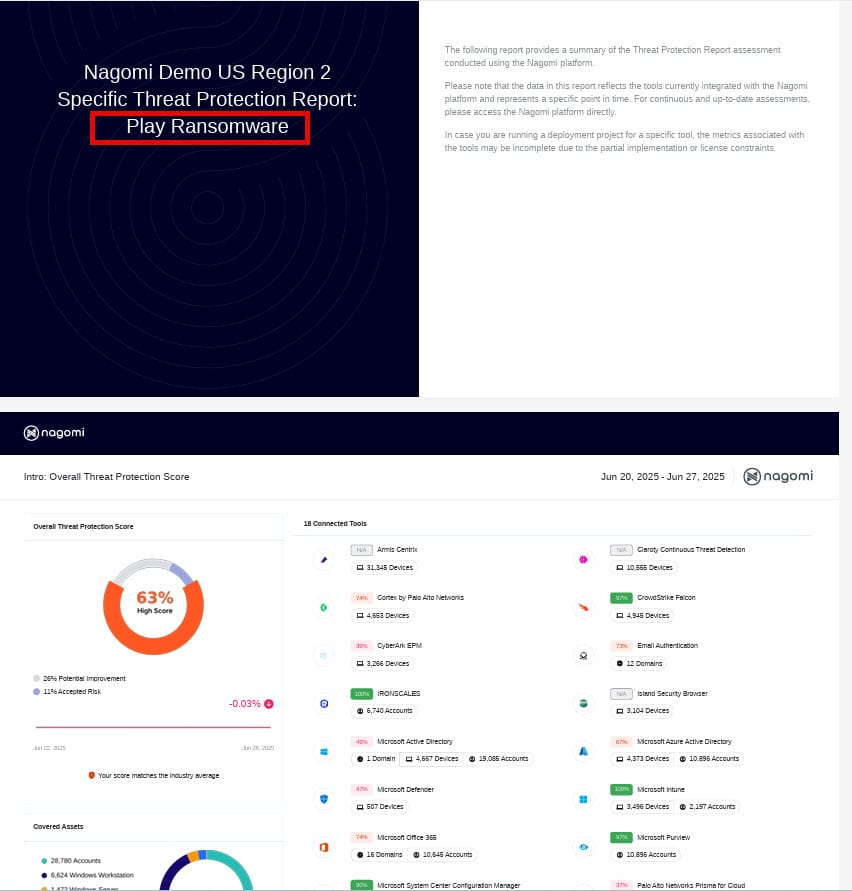
The final report is generated in an easy-to-understand visual PDF format that can be used to communicate organizational preparedness. The report below is the same report that teams can leverage to highlight their organizational readiness against the Play ransomware campaign to all their stakeholders (both technical and non-technical).
The Real Question: Are You Secure?
900 victims should be a wake-up call. The Play group isn’t using zero-days; they’re using your own weak points against you.
Nagomi helps your team:
- Detect exposures beyond vulnerabilities
- Prioritize what attackers can actually use
- Translate technical posture into executive insight
If you are uncertain about your exposure to Play ransomware or how your technology stack would respond in a real attack, now is the time to assess it. Book a demo or log in to the Nagomi platform and search “Play Ransomware” to test your readiness. Threats evolve. So should your defenses.