
Table of Contents
The third in a five part series exploring how security teams can identify the most commonly exploited gaps in defenses and leverage their existing security tools to defend against real-world threats.

By Eden Sit – Security Researcher
Overview: What is a MITRE ATT&CK Technique?
In the MITRE ATT&CK Matrix for Enterprise, techniques describe the methods an adversary uses to achieve a tactical objective through specific actions. With over 200 techniques and 435 sub-techniques, how should security teams prioritize them?
MITRE ATT&CK Technique Prioritization
To help customers decide what techniques to prioritize, Nagomi analyzed the techniques used most frequently in groups and campaigns. We then cross-referenced the techniques, groups, and campaigns against defenses to pinpoint where security teams can make the most impact. Leveraging our vast dataset encompassing hundreds of campaigns and monitoring millions of assets, the analysis calculates and prioritizes techniques rooted in real-world threats coupled with insights into tool underutilization.
Top MITRE ATT&CK Techniques with the Largest Security Tool Underutilization
Here are the most frequently used techniques with the biggest tool underutilization in cybersecurity today:
OS Credential Dumping
What is OS Credential Dumping in MITRE ATT&CK Terminology?
OS Credential Dumping involves extracting sensitive authentication information – such as hashed passwords, Kerberos tickets, or other credentials from an operating system. This technique is employed by attackers after they have initially compromised a system to further their objectives. By extracting these credentials, attackers can escalate privileges, move laterally within a network, and maintain persistence, allowing them to access additional accounts and services beyond their initial entry point.
Commonly used tools for OS Credential Dumping include Mimikatz, which specializes in extracting and manipulating credentials, ProcDump, a utility for capturing memory dumps, and built-in Windows features like LSASS (Local Security Authority Subsystem Service) memory dumps. These methods enable attackers to bypass traditional security measures and gain deeper control over compromised environments.
Example Group Using OS Credential Dumping: FIN7
FIN7, also referred to as Carbon Spider, ELBRUS, or Sangria Tempest, is a cybercriminal group primarily targeting financial and retail businesses since 2015.
The group frequently uses OS Credential Dumping techniques to escalate privileges and move laterally within networks, using tools like Mimikatz to extract credentials. This technique enables them to maintain unauthorized access, often leading to fraud or ransomware attacks.
To mitigate these threats, organizations should first deploy endpoint detection and response (EDR) tools and use Privileged Access Management (PAM) solutions, as it is essential to control and monitor the use of privileged accounts. These two actions combined will significantly reduce the risk of credential dumping and unauthorized access.
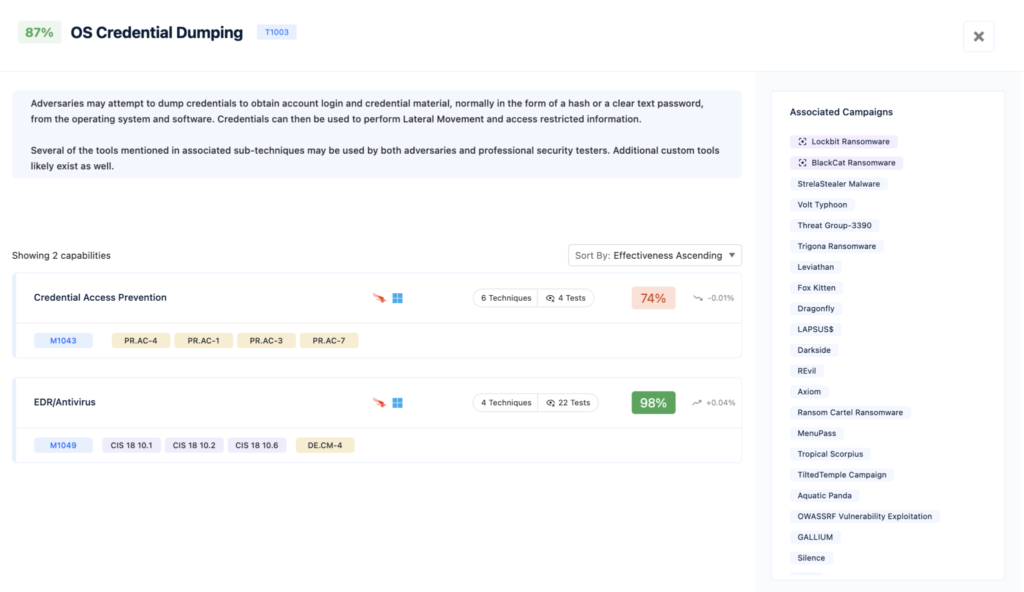
** OS Credential Dumping technique on Nagomi platform **
Two Ways to Defend Against OS Credential Dumping Using Existing Security Tools
The following section outlines two ways to improve your defense against OS Credential Dumping using the tools you may already have. For each, we’ll start by describing the defensive mechanism and then provide a detailed example.
A. Defending Against OS Credential Dumping with Privileged Access Management (PAM)
By implementing Privileged Access Management (PAM), you can control and monitor privileged access to critical systems. PAM solutions enforce the principle of least privilege, ensuring that users have only the access they need to perform their duties, thereby reducing the risk of credential dumping.
Feature: Memory Dump From Chromium Based Web Browsers
Web browsers store credentials and HTTP cookies in their process’ memory, including authentication cookies for websites and services. These credentials and cookies can be extracted by dumping the browser memory and then abused by an attacker to take action on behalf of the user and hijack the user’s session.
Example: Using CyberArk EPMBrowsers
The EPM agent protects the memory of Chromium based web browsers from being dumped.
- Log in to the CyberArk EPM Portal.
- Select your relevant Set and click the ‘Policies’ menu in the left pane.
- Click on ‘Privilege threat protection policies’ in the selection bar on the top of the page.
- Look for ‘Memory Dump From Chromium Based Web Browsers’ in case it is missing, add it using the blue button ‘Add threat protection policies’ at the top of the page.
- Set it to ‘block’.
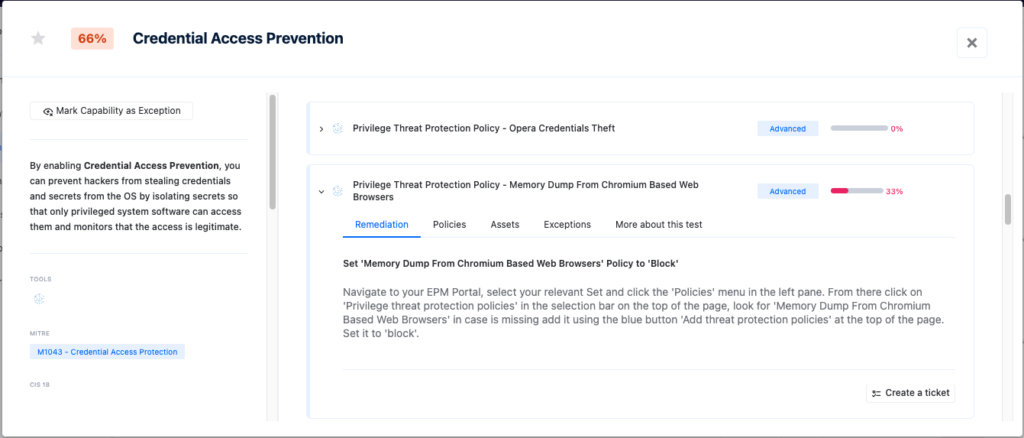
** Memory Dump from Chromium-Based Web Browsers on Nagomi Platform: This Customer Needs Some Improvements! **
B. Defending Against OS Credential Dumping with Endpoint Detection and Response (EDR) – Credential Access Prevention
Endpoint Detection and Response (EDR) solutions monitor and analyze endpoint activity to detect and respond to suspicious behavior, such as credential dumping. By implementing EDR, you can quickly identify and mitigate threats before they escalate.
Feature: Credential Dumping for Windows
Memory protection prevents unauthorized access to processes like LSASS, commonly targeted during credential dumping attacks.
Example: Using CrowdStrike Falcon
Identify and stop any suspicious processes attempting to steal login credentials and passwords.
- Log in to the CrowdStrike Falcon dashboard.
- Navigate to ‘Prevention Policies’
- Search for ‘Credential Dumping’ feature and enable it.
This feature kills suspicious processes determined to be stealing logins and passwords.
Endpoint Detection and Response Capability on the Nagomi Platform
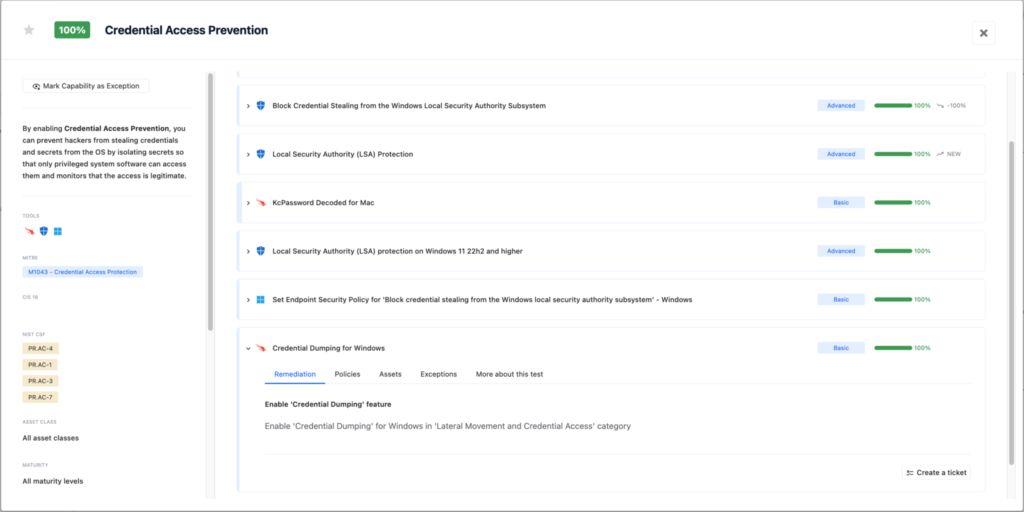
** Credential Dumping for Windows on Nagomi Platform: This Customer Did a Great Job! **
Summary
Here we underscore the importance of strategically prioritizing cybersecurity techniques based on real-world threat data. By focusing on OS Credential Dumping—an advanced technique used by attackers to extract sensitive authentication information—security teams can better allocate their resources and defenses.
The analysis by Nagomi reveals that OS Credential Dumping, among other techniques, suffers from significant tool underutilization, making it a critical area for improvement. Implementing effective defensive measures, such as Privileged Access Management (PAM) and Endpoint Detection and Response (EDR), can greatly mitigate the risks associated with this technique. PAM helps control and monitor privileged access, while EDR tools provide real-time detection and response to suspicious activities like credential dumping.
By adopting these strategies and leveraging existing tools more effectively, organizations can strengthen their defenses against OS Credential Dumping and enhance their overall cybersecurity posture.
To see how Nagomi can help you maximize the effectiveness of your tools, check out the Nagomi Proactive Defense Platform or book a demo.



